PHISHING ATTACKS (PHISHING) WHAT IS IT?
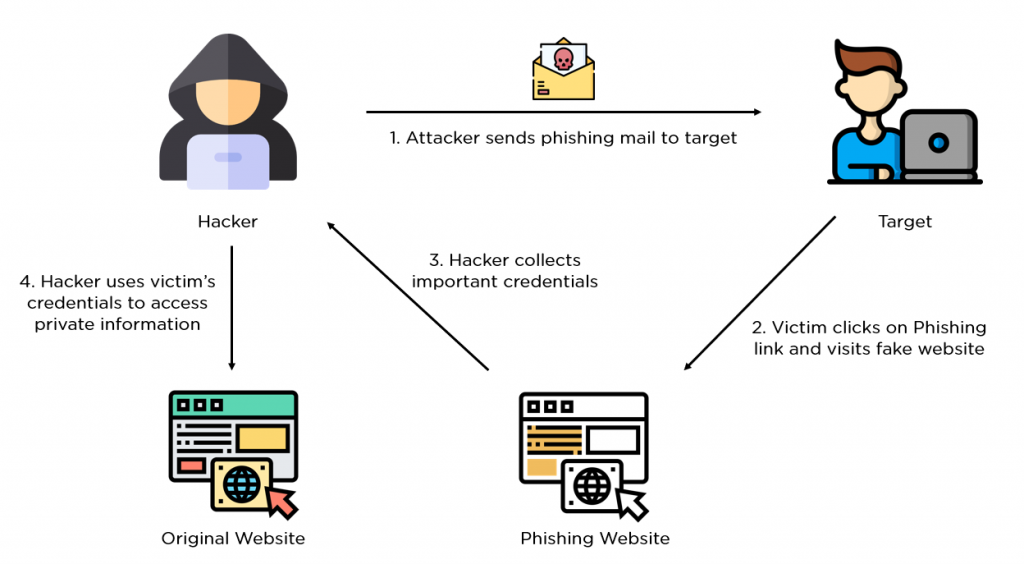
Phishing phishing attacks; used to steal user data, including login credentials and credit card numbers is a kind of social engineering attack. It occurs when an attacker who appears to be a trusted entity tricks the victim into opening an email, instant message, or text message. The recipient is then tricked into installing malware, freezing the system as part of a ransomware attack, or clicking on a malicious link where sensitive information has been exposed.
Phishing is often used to gain a foothold in corporate or official networks as part of a larger attack, such as an advanced persistent threat (APT) incident.
In this second scenario, it is used to bypass security steps, distribute malware in a closed environment, or obtain privileged access to secure data, endangering corporate employees and the organization. An organization that has succumbed to such an attack often suffers serious financial losses, as well as a reduced sunday share, reputation and consumer confidence. Depending on its scope, a phishing attempt may cause the enterprise to experience a security event that the organization will have difficulty recovering..
WHAT IS A FISHING ATTACK ON SOCIAL MEDIA?
Social media phishing attack, in short, the link for users to click on an infected link is interesting ("Congratulations, you have won an Iphone 13 as a result of our lottery, if you fill in your address information by clicking the link below, the shipping process will start." ), scary ("You tried to log in to your account. Click this link immediately. Change your password by clicking on it!”), by imitation (“Instagram: There is a mismatch in your account, your username and password are required for a detailed review.” or let us know by clicking the link below.” ), using friendships (“Look at this video, Ali is very i'm posting the funny link 😊”) is a type of fraud in which they encourage clicking the link by using these and similar methods, restoring them, designing fictions. As for what they will do when they enter your account, you are completely at the mercy of the attacker. Your private pictures, conversations with your friends, videos, personal information (information such as Turkish Identity Information, date of birth, city you live in), if registered, your card information may be put up for sale on the Dark Web or shared on all social media in order to disclose you. Information is power. An attacker can use information to realize any request.
HOW IS SOCIAL MEDIA PHISHING DIFFERENT FROM PHISHING?
In social media phishing, criminals use social engineering through social media to achieve their goals. On the other hand, for phishing (phishing), criminals mainly use e-mail. In addition, Social media phishing may contain intriguing plugins or topics that seem legitimate because they appear in an online community that users already know. Such baits are less likely to succeed in phishing email.
WHAT DOES IT HAVE TO DO WITH SOCIAL ENGINEERING?
Social engineering is the process of identifying weaknesses in human behavior and abusing them by manipulating them.
Although it is a difficult situation for an attacker to infiltrate the targeted system and access critical information, it is possible for him to achieve his goal by performing this process with social engineering. It is mainly used to describe human relationships or people’s carelessness.
Because human relationships and trust are at the forefront of social media, the attacker can find more incentive factors for you to click on the link by doing some social engineering.
An attacker can obtain information about his prey, establish a trust relationship, infiltrate his prey’s group of friends, and infiltrating his group means more data.
WHY IS SOCIAL MEDIA PREFERRED FOR FISHING LINE ATTACKS?
It has the advantage of gaining a sense of trust and reaching a wider audience in a short time through social engineering.
With the social engineering method, it increases the chances of people clicking on the link by creating an easier scenario because they know their interests and weaknesses.
When the accounts of people with high trust in social media are seized, it will also be easy for the attacker to access the information of his followers and those he has contacted.
When a corporate email arrives, a person suspects and questions it before opening a mail that is equipped according to their interests, but suspicion becomes much less for such submissions on social media.
HOW DO I KNOW IF I’M THE ONE ON THE HOOK OR NOT?
Kendimizi, aşağıdaki soruları sorarak değerlendirmemiz gereklidir.
- am I trying to open links that I don’t trust 100%?
- Do I make friends on social media with people I don’t know?
- Do I click on the links sent to set up an application with the promise of making money?
- Do I ask my friend by phone or face to face and confirm when I encounter a dialogue other than the dialogue that my friends have established with me?
- Do I know that social media sites such as Instagram, Twitter, Facebook, Linkedin will not send me messages personally?
- Can I realize that my interests are being exploited, used?
- Do I confirm the click requests on the link by calling the sender?
- If I clicked on the link, do I take into account the warnings of the firewall and evaluate it?
- If I clicked on the link, do I check its URL before filling out the login screen?
- If I clicked on the link and entered my information, I couldn’t log in to the page and I was redirected to the login screen again?
- If you evaluate his questions carefully and answer them, you will notice whether you are on the end of the line.
WHAT ARE THE PICING ATTACKS THAT I MAY ENCOUNTER IN SOCIAL MEDIA ATTACKS?
The attack could come in the form of a post with a link designed to persuade the victim to share it on their social media. The victim's links can click on the link, trusting the source. From here they can be taken to a phishing (but real looking) website. They redirect the user to a fake login screen that forces them to authenticate using their information (login screen) with the promise of showing the content they tricked the user into following them. Often, authentication fails and forcing the victim to re-enter their credentials, obtaining these credentials is all it takes for an attacker to cause and infect digital destruction.
Facebook is the third most imitated brand for phishing attacks. With so many users worldwide, it’s easy to see why. The platform offers a large number of profiles and messages filled with personal information for phishers to take advantage of.
Attacks on Facebook are usually aimed at consumers, not large organizations. Phishers use social engineering to expose unsuspecting victims to their data.
By pretending to be from Facebook, messages are sent to users, for example, about a security alert. From here, users are instructed to log in to their Facebook profile and change their password. They are then posted to a fake Facebook login page where their credentials are collected.
How Does Phishing Target Your Friends?
If they access your account, they can create a wider network by victimizing your contacts. In addition, they can use the information that your friends have shared with you for another attack fiction later.
Phishers use your account to send messages or send a status with a malicious link. And because your contacts trust you, they are more likely to click on it.
What is Lantern Phishing?
This is a type of phishing that uses social media, but has a more complex MO. They are aimed at users who post (mostly rants) about a service or account. Attackers pretend to be from the service provider, then send the user a link to contact a customer service representative.
Formerly a selfie gallery, the app has now become a multimillion-dollar app used by some of the world’s biggest brands and influencers.
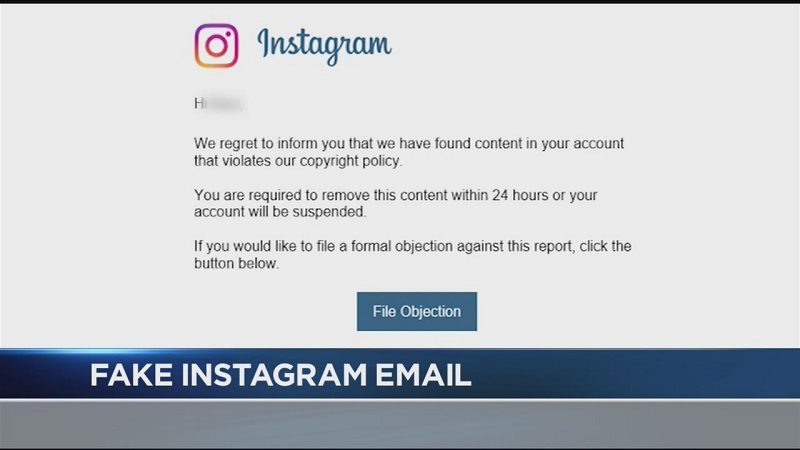
Like phishing users on Facebook, those who use Instagram send messages to users about a security alert. For example, it may be a message about an attempt to log in from an unknown device. The email has a link that sends users to a fake site where their login information is collected.
Once they have access, they will have a gold mine of personal information to use in different ways. For example, a possible attack involves blackmailing you or your friends by threatening to leak photos you have shared privately through Instagram Direct Messenger (IGdm) if you do not comply with their demands.
What is Copyright Infringement Fraud?
Phishers can launch more insidious phishing campaigns through IGdm if they seize business accounts, in particular verified accounts.
What is Blue Badge Scam?
Nothing feels as legit as having that coveted blue check. Phishers also take advantage of this.
An Instagram phishing scam is also to send an email offering users a certified badge. When users click on the “Verify Account” button, they will be taken to a phishing page where their personal information will be collected. Most often, influencers and “Insta-famous” users are targeted for this type of attack.
Linkedin, the main platform for business, used by more than 900 million professionals, is also a favorite target of phishers.
People trust Linkedin more than any other social networking site, according to a digital trust report. Users are more likely to post detailed information about their business, making them a primary target for spear phishing and whaling attacks.
How Do Fake Recruiters Scam Linkedin Users?
One of the most brutal social media phishing campaigns is an attack on Linkedin targeting job seekers. Cybercriminals pretend to be recruiters and reach out to users about a fake job posting via Linkedin Messaging.
Phishers lure you in by saying that your background is perfect for the role they are trying to fill. They make it even more irresistible with an increased compensation package.
You will see a link where the phishing agent says that he has all the details about the work. Alternatively, they can october an attachment in Microsoft Word or Adobe PDF for download.
It sounds exciting, especially for someone who is looking for a job. But the links lead you to a fake landing page, and in the Word file there are Macros for launching malware. The latter can steal your data or open a backdoor into your system.
WHAT SHOULD I DO IF I’M THE ONE ON THE HOOK?
- If you’ve been hooked by some clever social media phishers, you’ll need to do some damage checks. Start by treating this as a case of identity theft, because it can lead to it if you don’t take action.
- Turn off your computer immediately.
- Change your passwords by using a different computer.
- Put a fraud alert on your account.
- If you have provided your bank or credit card information, call your bank and report it.
- If you are unable to log in to any of your accounts, immediately notify us of an account seizure.
- Let your friends know, ask your friends to share about it.
- If you are a victim of social media phishing, let others know. No need to be ashamed! By raising awareness in your social media environment, you will ensure the safety of people who trust you, which will hopefully reduce the amount of successful hacks.
WHAT IS MY DUTY IN SOCIAL MEDIA ATTACKS? HOW CAN I BE PROTECTED FROM THESE ATTACKS?
- It is recommended that you use MFA (Multi Factor Authentication), that is, Multi-Factor Authentication.
- When you think that your relative's account has been hacked, the person should be contacted and verified.
- If his account has been compromised, you should spread it on social media to prevent other people from falling for it.
- You should not open links that you do not 100% trust.
- You should not make friends on social media with people you don’t know.
- Shouldn’t you click on the links sent with the promise of free gifts to make money?
- If you encounter a dialogue other than the dialogue that your friends have established with you, you should ask your friend by phone or face to face and confirm it.
- You should know that social media sites such as Instagram, Twitter, Facebook, Linkedin will not send you messages personally.
- You should be able to realize that your interests are being exploited and used.
- You must confirm the requests to click on the link by calling the senders.
- If you clicked on the link, you should be considering and evaluating the warnings of the firewall.
- If you clicked on the link, you should check its URL before filling out the login screen.
- If you clicked on the link and were unable to log in to the page when you entered your information and were redirected back to the login screen, you should realize that your account information has been compromised and ensure that it is notified.
IT DOESN’T MATTER WHAT HAPPENS IF MY ACCOUNT IS STOLEN?
You may think that your account is insignificant, but you should think that the people who follow you and trust you through your account will also be affected by this, that these people may have private information, and their information will be in danger due to your reckless attitude.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.
[/vc_cta][/vc_column][/vc_row]