Information and Communication Security Guide Our Compliance Audit Service
T.R. Within the scope of the "Person and Firm Providing Information and Communication Security Guide Compliance Audit Service" certification program carried out by the Turkish Standards Institute for the Digital Transformation Office Information and Communication Security Guide audits. CyberArts IT audit service company as authorized. To increase the cyber resilience of our institutions that demand art, not mediocrity in the cyber world; Our authorized team of auditors, which has always adopted the principle of working meticulously by preserving its professional reputation and prestige, has started to provide value-adding audit services with the company qualification obtained from TSE.
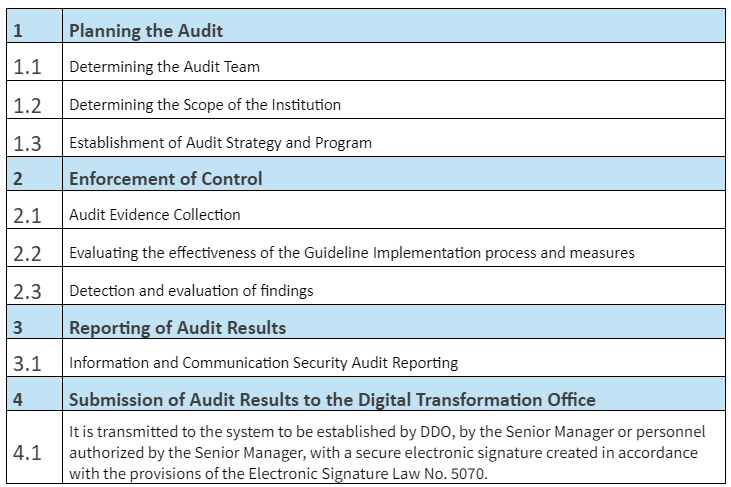
As known; It is expected that public institutions and organizations and businesses providing critical infrastructure services that have completed their compliance studies with the Information and Communication Security Guide will plan and perform the Information and Communication Security Guide audit as of 27 July 2022.
Our Audit Processes:
CyberArts Informatics Inc.. olarak yetkin, tarafsız, deneyimli denetçi kadromuzla kurumlarımıza değer katan denetimler için hazır olduğumuzu bilmenizi isteriz. Bilgi ve İletişim Güvenliği Denetimleri ile ilgili herhangi bir sorunuz olur ise buradan bize her zaman ulaşabilirsiniz.
Information and Communication Security Guide Our Compliance Audit Service
CyberArts olarak ülkemizin “Elektronik Haberleşme”, “Enerji” “Finans”, “Ulaştırma”, “Su Yönetimi” olarak tanımlanan kritik altyapı sektörleri başta olmak üzere tüm kamu hizmetlerinin siber tehditlere karşı korunması ve dayanıklılığının artırılmasına büyük önem vermekteyiz. Bilgi ve İletişim Güvenliği rehberine uyumlulukta sıradanlık değil sanat talep eden tüm kurumlarımıza titizlikle aşağıdaki kapsamda danışmanlık hizmetleri sunmaktayız. Bilgi ve İletişim Güvenliği rehberinde yer alan tedbirlerin uygulanabilmesini sağlamak için aşağıdaki gibi uygulama süreci tamamlanmıştır. Rehber temel olarak mevcut yönetim süreçlerine teknik olarak katkı sağlayacak tedbirleri ve faaliyetleri içermektedir.
Information and Communication Security Guide Compliance Project Consulting Our Service Steps:
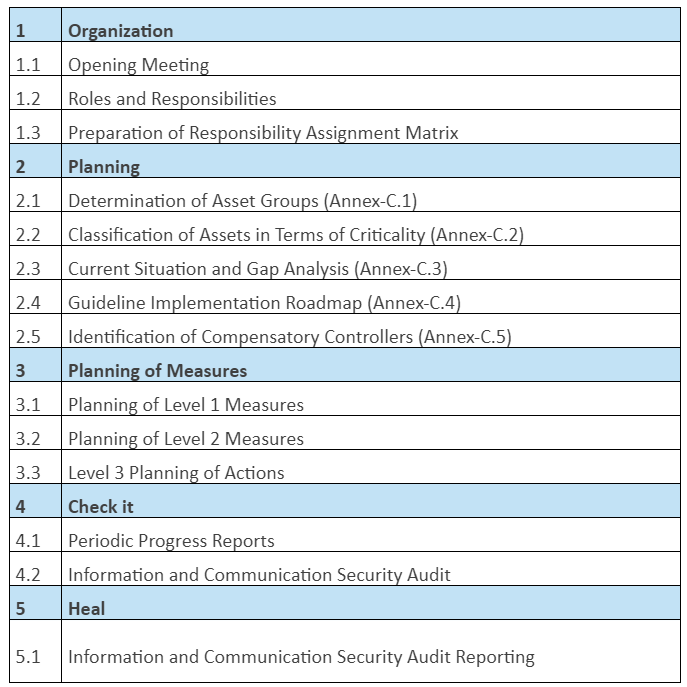
- Asset Group Determination:
In the studies carried out within the scope of the guide, the assets should be grouped and grouped under the determined headings and measures should be implemented by taking these groups into account. Directory; It includes the information processing facilities where the information/data in the electronic environment is stored, transferred and processed, the personnel using the information processing facilities and the physical environments that contain the information processing facilities. The main headings of the asset group defined in the guide are listed below:
- Network and Systems
- Apps
- Portable Devices and Media
- Internet of Things (IoT) Devices
- Physical Spaces
- Employee
- Asset Group Critical Determination:
For each asset group, a survey should be conducted to determine the criticality level with the participation of the owners of the assets, system administrators, developers, user representatives, managers and the most competent personnel of the institution, according to the Delfi method.
Survey Questions In Terms of Processed Data;
- Privacy
- Integrity
- Accessibility
In terms of Domain;
- Number of Affected People
- Social Consequences
- Institutional Results
- Sectoral Impact
- Dependent Assets
The survey score for the asset group is determined by adding together the dimensions and the scores they have received from the survey.
- Current Situation and Gap Analysis:
Varlık gruplarının kritiklik dereceleri dikkate alınarak güvenlik tedbirlerinin hangilerinin uygulanması gerektiğinin belirlenmesi ve belirlenen güvenlik tedbirlerine göre mevcut durumun tespiti için detaylı çalışma yapılmalıdır. Rehberde güvenlik tedbirleri üç ana başlık altında sınıflandırılmıştır.
- Main headings of security measures for asset groups:
- Main headings of security measures for application and technology areas:
- Main headings of security measures for tightening activities:
- Preparation of Guideline Implementation Roadmap:
After determining the activities required to eliminate the deficiencies identified as a result of the gap analysis, planning is made. All relevant legal, regulatory and contractual requirements are taken into account within the scope of the plans. The work to be done within the scope of the guideline implementation roadmap is determined at this stage. Studies can be grouped as follows, but not limited to the following groups:
- Competence acquisition and trainings
- Product supply
- Procurement of services
- Consultancy
- Development / redevelopment
- Design / redesign
- Compression
- Version update
- Documentation
- Enterprise process improvement
- Guideline Implementation Roadmap Implementation
The guideline implementation roadmap will be implemented by the personnel of the institution as planned, taking into account the periodically determined targets. In this context, procurement, service procurement, redesign, etc. determined in the roadmap. The allocation activities of the necessary resource needs of all studies should be prioritized. The basic principles to be considered in the application are as follows.
- Security Based Design (Security by Design)
- Privacy by Design
- Defense in Depth
- Reducing the Attack Surface
- Minimum Authorization
- Identifying the Weakest Link
- Alignment of Security Goals with Business Goals
- Preferring Domestic and National Products
- Prevention of Duplicate Work and Investments
- The Need to Know Principle
- Monitoring and Checking the Guideline Implementation Roadmap
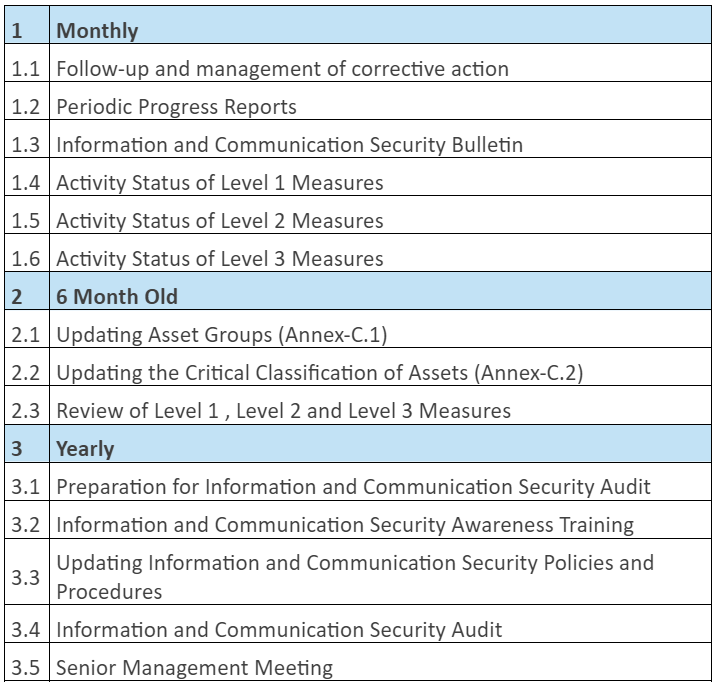
It is necessary to carry out activities related to the follow-up of the progress of the guideline implementation roadmap studies and the determination of the deviations from the prepared plan and taking the necessary measures. In addition, the management of the problems and risks that will be encountered while carrying out the implementation roadmap studies should also be carried out. At the end of the semester, roadmap progress reports containing information about the work carried out in the implementation roadmap, deviations from the planned targets, problems and risks, and the measures taken should be prepared. Bilgi ve İletişim Güvenliği Uyum çalışmaları ile ilgili herhangi bir sorunuz olur ise bize buradan her zaman ulaşabilirsiniz.
Information and Communication Security Guide Compliance Sustainability Our Consultancy Service
Denetim süreci boyunca kontrollerin tasarımı ve işletimine dair tespit edilen bulguların Kurumun bilgi güvenliğinde yaratacağı risk faktörlerinin etkin Yönetimi için uyum süreci sürdürülebilirlik danışmanlık hizmetini aşağıdaki proje adımları ile vermekteyiz. Bulguların kritiklik derecesi, kurumda ortaya çıkaracağı Güvenlik riskinin bilgi güvenliğine olan etkisi ve gerçekleşme olasılığı dikkate alınarak, kurumun siber dayanaklılığının artırılması ancak tedbirlerin sürdürülebilir olması ile mümkün olacaktır.
Information and Communication Security Guide Compliance Sustainability Consulting Our Service Steps:
Information and Communication Security If you have any problems with compliance and sustainability, you can always contact us here