In accordance with the Presidential Circular on Information and Communication Security Measures, published on 6 July 2019, public institutions and businesses providing critical infrastructure services; It has been obliged to implement certain security measures in order to reduce and neutralize the security risks encountered and to ensure the security of critical types of data that may threaten national security or cause disruption of public order, especially when its confidentiality, integrity or accessibility is impaired.
In this context, as CyberArts our country's “ Electronic Communications”, “Energy” “Finance”, “Transport", "Water Management" of all public services, especially critical infrastructure sectors. We attach great importance to its protection against cyber threats and increasing its resilience.
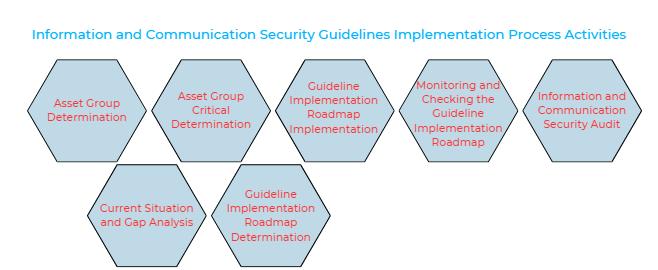
We meticulously provide consultancy services within the following scope to all our institutions that demand art, not mediocrity, in compliance with the Information and Communication Security guide. In order to ensure that the measures in the Information and Communication Security Guide can be implemented, the implementation process has been completed as follows. The guide includes measures and activities that will technically contribute to the basic existing management processes.
Asset Group Determination:
In the studies carried out within the scope of the guide, the assets should be grouped and grouped under the determined headings and measures should be implemented by taking these groups into account. Directory; It includes the information processing facilities where the information/data in the electronic environment is stored, transferred and processed, the personnel using the information processing facilities and the physical environments that contain the information processing facilities.
The main headings of the asset group defined in the guide are listed below:
- Network and Systems
- Apps
- Portable Devices and Media
- Internet of Things (IoT) Devices
- Physical Spaces
- Employee
Asset Group Critical Determination:
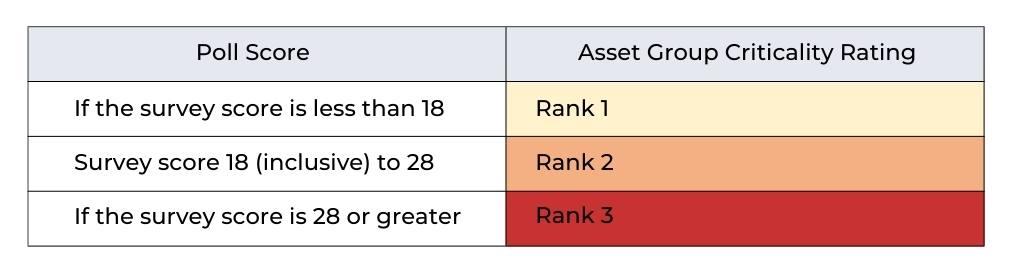
For each asset group, a survey should be conducted to determine the criticality level with the participation of the owners of the assets, system administrators, developers, user representatives, managers and the most competent personnel of the institution, according to the Delfi method.
Survey Questions In Terms of Processed Data;
- Privacy
- Integrity
- Accessibility
In terms of Domain;
- Number of Affected People
- Social Consequences
- Institutional Results
- Sectoral Impact
- Dependent Assets
The survey score for the asset group is determined by adding together the dimensions and the scores they have received from the survey. According to the survey score, the criticality of the asset group is determined as follows.
Current Situation and Gap Analysis:
Considering the criticality of the asset groups, a detailed study should be carried out to determine which security measures should be applied and to determine the current situation according to the determined security measures. Security measures are classified under three main headings in the guide.
- Main headings of security measures for asset groups
- Main headings of security measures for application and technology areas
- Main headings of security measures for tightening activities
Preparation of Guideline Implementation Roadmap:
After determining the activities required to eliminate the deficiencies identified as a result of the gap analysis, planning is made. All relevant legal, regulatory and contractual requirements are taken into account within the scope of the plans.
The work to be done within the scope of the guideline implementation roadmap is determined at this stage. Studies can be grouped as follows, but not limited to the following groups:
- Competence acquisition and trainings
- Product supply
- Procurement of services
- Consultancy
- Development / redevelopment
- Design / redesign
- Compression
- Version update
- Documentation
- Enterprise process improvement
Guideline Implementation Roadmap Implementation
The guideline implementation roadmap will be implemented by the personnel of the institution as planned, taking into account the periodically determined targets. In this context, procurement, service procurement, redesign, etc. determined in the roadmap. The allocation activities of the necessary resource needs of all studies should be prioritized.
The basic principles to be considered in the application are as follows.
- Security Based Design (Security by Design)
- Privacy by Design
- Defense in Depth
- Reducing the Attack Surface
- Minimum Authorization
- Identifying the Weakest Link
- Alignment of Security Goals with Business Goals
- Preferring Domestic and National Products
- Prevention of Duplicate Work and Investments
- The Need to Know Principle
Monitoring and Checking the Guideline Implementation Roadmap
It is necessary to carry out activities related to the follow-up of the progress of the guideline implementation roadmap studies and the determination of the deviations from the prepared plan and taking the necessary measures. In addition, the management of the problems and risks that will be encountered while carrying out the implementation roadmap studies should also be carried out.
At the end of the semester, roadmap progress reports containing information about the work carried out in the implementation roadmap, deviations from the planned targets, problems and risks, and the measures taken should be prepared.
Information and Communication Security Audit
Institutions have been given a 24-month adaptation period as of 27 July 2020, the publication date of the Guide. In the first year audits, institutions should start the preparatory work for the audit activities at the end of the 24-month period at the latest. However, institutions that have completed their compliance work before 24 months can start the preparatory work for audit activities without waiting for the compliance period to expire.
The audit team should consist of at least 2 auditors. Personnel must provide at least one of the following competencies.
- To have ISO/IEC 27001 Lead Auditor certificate
- Have CISA certification
- Being an authorized auditor or lead auditor within the scope of the Certification Program
CyberArts Bilişim A.Ş. We want you to know that we are ready for audits that add value to our institutions with our competent, impartial and experienced auditor staff.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.