A previously undocumented python backdoor was detected targeting Wmware ESXi servers, and the vulnerability allowed remote code execution on the exposed system.

What is WMware ESXi?
ESXi, a product of Wmware software company, is expressed as an enterprise-specific hypervisor that performs the distribution and presentation of virtual computer servers. It is not a product like Workstation, it is an operating system with Unix AA infrastructure. In the structure where it is installed, there is enough RAM, processor and space for other machines that want to be virtualized by doing very little processing.
It was discovered by Juniper Networks researchers on the Backdoor Wmware ESXi server, but they were unable to determine how it was compromised. For now, they believe the server may have been compromised using vulnerabilities CVE-2019-5544 and CVE-2020-3992 in ESXi’s OpenSLP service.
Backdoor, new lines are detected in the file ‘/etc/rc.local.d/local.sh’. These lines are not affected during the reboot and continue to exist.
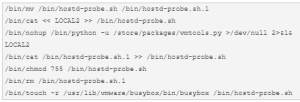
Dosyaya eklenen ek satırlar (Juniper Networks)
The attack starts with the Python script saved as “/store/packages/vmtools.py” in the directory where VM disk images, logs and more are stored. “Although the Python script used in this attack can be used cross-platform and on Linux or other UNIX-like systems with little or no modification, there are several indications that this attack was designed specifically to target ESXi,” explains Juniper Networks.
Since the script used does not look different from the Wmware copyright information and the Python file provided by Wmware, attackers can control this file from the outside and manage this file through the web server. It can start a reverse shell with base-64 encoded payloads.
To ensure the connection, they edit the ‘etc/vmware/rhttpproxy/endpoints.conf’ file and make it permanent inside.
Can be controlled:
You can check whether the above lines exist in the “local.sh” file. Configuration files should be examined and checked for additional lines. Finally, access to ESXi servers should only be allowed from certain IPs.
Source:
VMware ESXİ Nedir? (veriakademi.com)
What is VMware ESXi? – Definition from TechTarget.com
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












