Although automobile penetration techniques seem to be one of the areas that show the difference, it will be one of the important test methods for today and the future. As our cars become smarter, more electronic, it makes cars more vulnerable.
As we enter the era of literally driverless or autonomous cars, the safety of cars has become and will become more important.
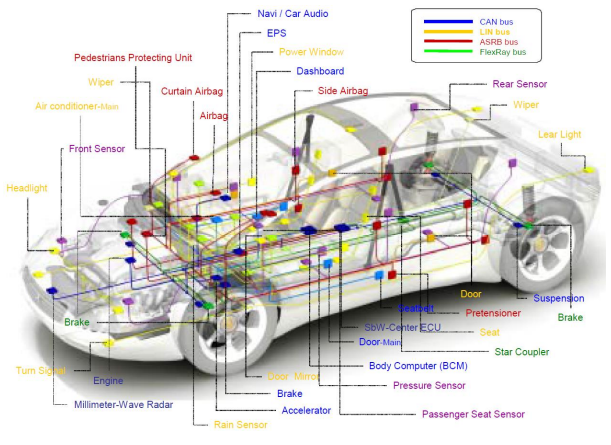
Before we move on to automobile infiltration techniques, we need to understand the basics. Automobile electronics, multiple microcontrollers, sensors , indicators, actuators , etc. It uses several different protocols to communicate between The most widely used of these protocols is Controller Area Network or CAN.
CAN, Every node in the Network can “see” every transmission. Unlike Ethernet or TCP/IP (but similar to modbus in SCADA systems ) you cannot send messages to a single node, but CAN provides local filtering so each node only acts on messages related to its own operation. You can think of it as “content messaging” where the content determines the target node.
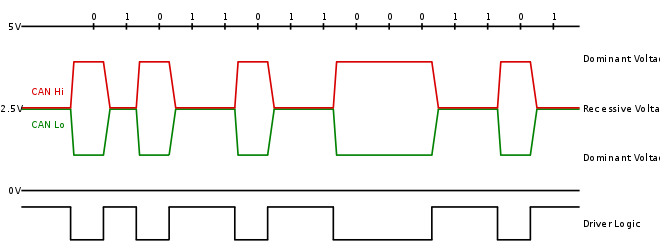
BELL; It works over two wires, high and low. Because of the “noise” inherent in automobile systems, CAN uses differential signaling . This is where the protocol raises and lowers the voltage on the two wires to communicate. In both high speed and low speed CAN signaling drives the high wire towards 5v and the low wire towards 0v while transmitting zero (0). But when sending one (1) it doesn’t drive both wires.
CAN uses four (4) different types of messages;
- Data Frame
- Remote Frame
- Error Frame
- Overload Frame
Data Frame
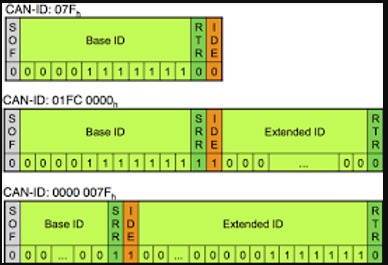
This is actually the only framework used for data transmission. In most cases, the data source node sends the data frame. There are two types, standard and extended. The standard has 11 identifier bits and the extended has 29 bits. CAN standard, the base data frame MUST be adopted and extended frame MUST BE TOLERANCED. In other words, does not break the protocol or transmission.
Remote Frame
Data destination node requests data from the source.
Error Frame
It has two different fields, the first one is given by Error Flags and different stations contributed by. And the second is Error Delimeter, which only shows the end of the error message.
Overload Frame
Overload The Frame has two fields. These are the Overload Flag and the Overload Limiter. The overload frame is triggered by the internal conditions of a receiver or by detecting the dominant bit (0) during transmission.
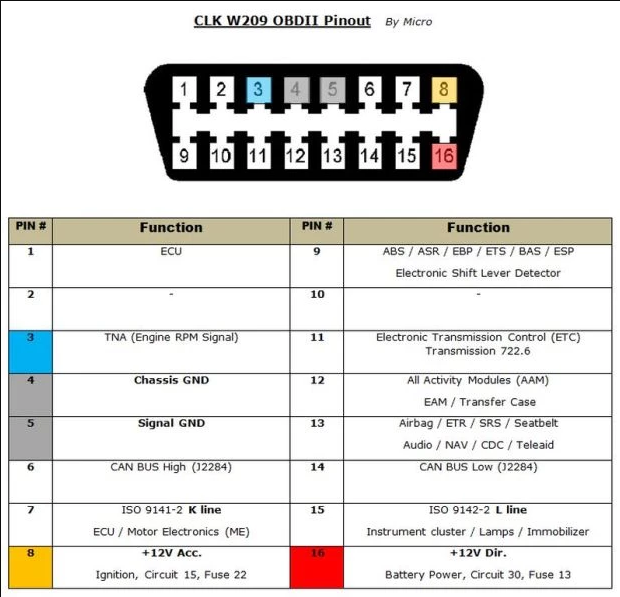
Onboard Diagnostic (OBD)-II Connector
With an ODB-II connector . If you’ve taken your car to a shop for repairs, it’s this connector at the bottom of the dashboard that the mechanic connects to his computer to get a reading.
OBD – II has 16 pins and looks like the diagram below.
As a pentester , we can connect to this OBD-II connector and send messages to various devices over the CAN network..
CAN Bus Packet Layout
There are two types of CAN packages, standard and extended. Extended packs share the same elements as the standard pack. But extended packages have additional space to include IDs
Standard Packages
Each CAN packet has four critical sections. These;
- Arbirition ID
The ID of the device that sent the packet.
- Identifier Extension
This bit is always 0 for standard CAN.
- Data Length Code (DLC)
This indicates the size of data from 0 to 8 bytes.
- Data
This is the data in the message. As mentioned above, it can be up to 8 bytes.
As mentioned above, all CAN packets are broadcast. So every device or controller can see every packet. There is no way for any device to know which controller sent the packet (no return address). Therefore, fake messages in the CAN network are irrelevant. This is one of the main weaknesses of CAN.
Extended CAN Packages
Extended CAN packages are the same as standard CAN packages. But they are chained together to form longer identities. Extended CAN is backward compatible with standard CAN. This means that if a sensor is not designed to accept extended CAN packets, this system will not fail.
Security
Because CAN is a low-level protocol, it does not have any built-in security features. By default there is NO encryption or authentication. This can lead to man-in-the-middle attacks (no encryption) and spoofing attacks (no authentication). In some cases, manufacturers have implemented authentication mechanisms in mission-critical systems such as modifying software and checking brakes, but not all manufacturers have implemented them. Even where passwords are enforced, they are relatively easy to crack.
You can access other parts of this content series at the following links:
- How Should New Generation Automobile Safety Tests Be Performed? [2]
- How Should New Generation Automobile Safety Tests Be Performed? [3]
- How Should New Generation Automobile Safety Tests Be Performed? [4]
Disclaimer
Dear visitor,
This blog post is for information purposes and has been prepared with the aim of raising awareness against attacks and taking measures in this direction. We remind you that it is not legal to use the information in this article for any other purpose. We declare that CyberArts company cannot be held responsible for direct or indirect damages and losses that may arise from what is explained.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.
[/vc_cta][/vc_column][/vc_row]