In this article, we will discuss the ZTA title from the NIST Framework. Let's examine the ZTA and VPN structures beforehand. VPN solutions, which are frequently used in information technologies, are a technology that allows connecting to different networks via remote access. Significantly increases the risk of breaches by opening corporate networks and resources to untrusted devices. Security vulnerabilities occur at this point, as the VPN authenticates after access. In addition, it is ignored that VPN solutions are a technology for more than 30 years and that VPN technology, like most old systems, has security vulnerabilities.
Translated into Turkish as “Zero Trust Architecture”, the architecture is a model that considers that there is no 100% trust in any flow within the boundaries of the enterprise. Zero trust means that the existing system should not be trusted, even if the networking devices are connected to the corporate network.
One hundred percent security is not possible for every area where people are present. This is where the Zero Trust architecture treats all users as potential threats. Users are denied access to data and resources until they are properly authenticated and granted access. The structure is advancing in the understanding of "Never trust and always verify" instead of "Trust but verify". In this sense; Many possible cases such as theft of critical data, Keylogger attacks, network eavesdropping attacks are prevented.
ZTA is a solution in corporate networks with remote users. It is a solution that will also minimize the risks brought by the BYOD (bring your own device) model. This model can also be used safely in remote working methods that have increased due to the Covid-19 Pandemic process.
ZTA from the NIST Framework
Founded in 1901, NIST (National Institute of Standards and Technology) is a US federal states standards institute that publishes measurement methods and standards rather than Industrial standards. NIST describes Zero Trust Architecture in Special Publication 800-207 on August 11, 2020.
ZTA strategies already exist in cybersecurity policies and programs, but the document includes a gap analysis of areas where further research and standardization is needed to assist businesses in developing and implementing ZTA strategies. Additionally, this document establishes zero trust and an abstract definition of ZTA as well as general distribution models.
Principles of Zero Trust
There are basic principles that must be found in the Zero Trust architecture. It should be noted that these principles are ideal targets, while in businesses, not all principles can be fully applied to a particular strategy in its purest form.
- All data sources and computing services are considered resources. A network can consist of multiple device classes.
- All communication is secure, regardless of network location.
- Access to individual and corporate resources is granted on a per-session basis.
- Access to resources is determined by the observable state of customer identity, application/service, and dynamic policy involving the requesting entity, and may include other behavioral and environmental attributes.
- The organization monitors and measures the integrity and security status of all owned and associated assets. By its very nature, no being can be trusted. When evaluating a resource request, the organization evaluates the security state of the asset. An organization implementing a ZTA should set up a continuous diagnostic and mitigation (CDM) or similar system to monitor the health of devices and applications and apply patches/fixes as needed.
- All resource authentication and authorization are dynamic and strictly enforced before access is granted. It is a continuous cycle of gaining access, scanning and evaluating threats, adapting trust in continuous communication, and constantly re-evaluating.
- The organization collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture. An organization should collect and process data about asset security status, network traffic, and access requests, and use any insights gained to improve policy formulation and enforcement.
ZTA Logical Components
There are many logical components that make up a ZTA deployment in an organization. These components can be run as an on-premises service or through a cloud-based service. The conceptual framework model in the figure shows the basic relationship and interactions between the components.
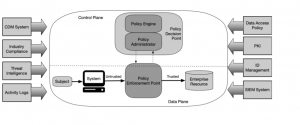
Image in figure This image from NIST Special Publication 800-207 illustrates the Zero Trust architecture. Zero Trust architecture describes the processes of providing secure access to resources. Threat intelligence, network and system activity logs, information from components such as PKI and SIEM, and access requests are evaluated in the PEP (Policy Enforcement Point). This system is the component responsible for enabling, monitoring and terminating links between a topic and an enterprise resource, where policy updates are made to organizations. Policies are where the user's access to which resources is determined. The PEP system created by the Policy Engine and the Policy Administrator provides the definition and control of the necessary policies. As a result of the control, requests matching the policy can access company resources, otherwise access is not possible.
As a result, the methods used in the security of data, which is one of the most valuable resources of institutions / organizations, are increasing. As a result of the use of outdated and vulnerable solutions, backdoors and vulnerabilities may occur in the systems. As explained in NIST's Special Publication 800-207, the Zero Trust architecture has once again demonstrated that one hundred percent trust is not possible in cyber security, based on the definition of zero trust.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












