APT campaigns have been observed targeting companies in multiple industries, including cybersecurity researchers, automotive, pharmaceutical and engineering, and managed service providers based in Japan.
Kaspersky researchers named the campaign A41APT (not APT41), derived from the hostname “DESKTOP-A41UVJV” from the attacker's system used in the initial infection. The findings, called “A41APT”, were developed by the APT group known as APT10 alias Stone Panda, by SodaMaster, P8RAT and It explores a new spectrum of attacks using previously undocumented malware such as FYAnti. The new attacks uncovered by Kaspersky are said to occur in January 2021. The attack, on the other hand, is through the misuse of SSL-VPN using zero-day vulnerabilities or exploiting stolen credentials.
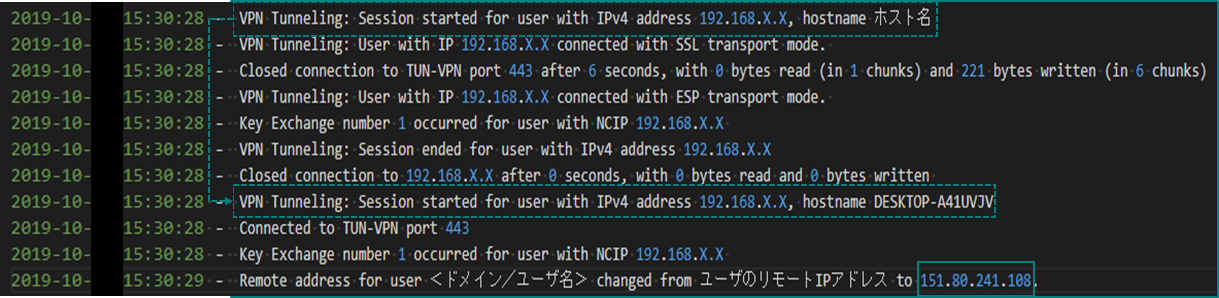
Logs of VPN session captured from DESKTOP-A41UVJV
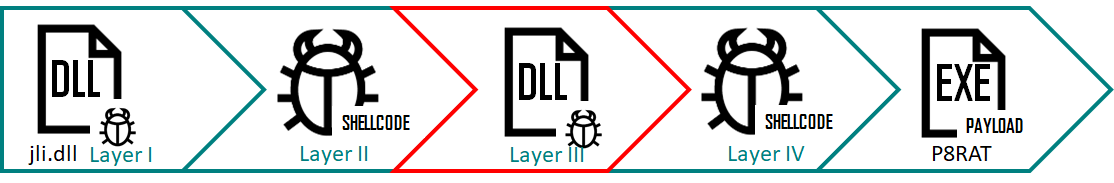
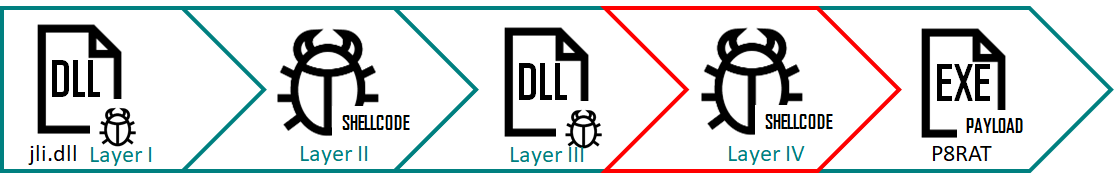
The attack campaign uses four files to load and decrypt 4 fileless loader modules in a row. Complicated loading schema management is used, utilizing four different files to load and decrypt four fileless loader modules one after the other.
Ecipekac Technical Analysis
A multi-layered x64 installer was observed, named Ecipekac after a unique string used exclusively by attackers and found in the second layer of the Ecipekac installer. The string is “Ecipekac” in the opposite direction.
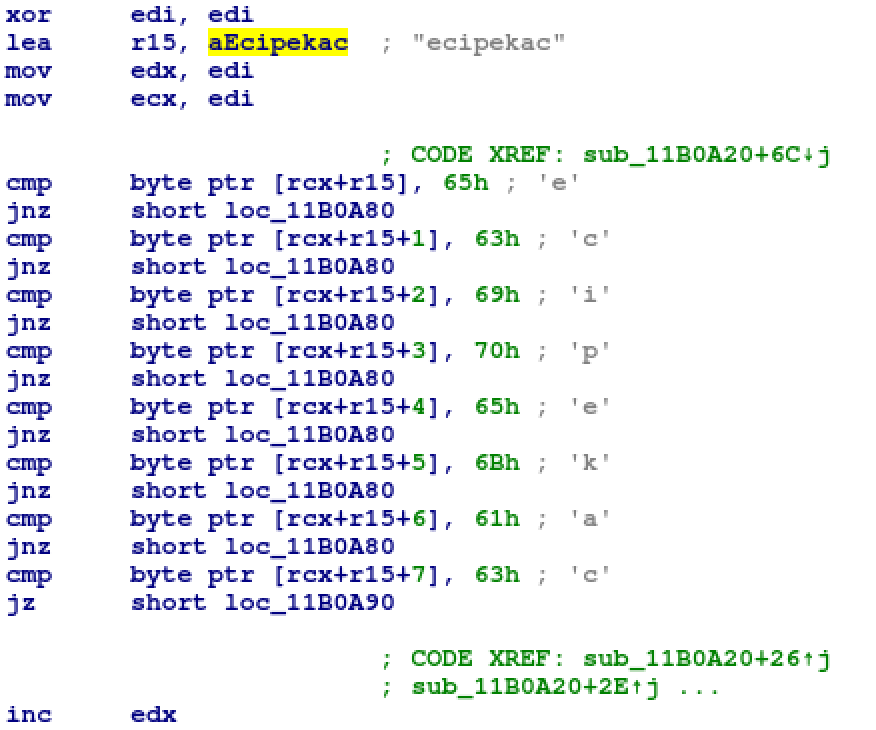
Hardcoded unique string “ecipekac”
Ecipekac uses a new and complex loading scheme. It uses the four files listed below to load and decrypt four fileless loader modules one after the other to finally load the final load into memory.
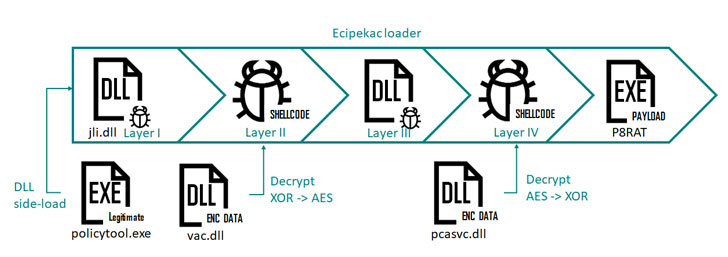
Ecipekac infection stream
The files are:
| File name | MD5 Hash | Explanation |
| policytool.exe | 7e2b9e1f651fa5454d45b974d00512fb | exe for DLL loading |
| jli.dll | be53764063bb1d054d78f2bf08fb90f3 | Ecipekac Layer I installer |
| vac.dll | f60f7a1736840a6149d478b23611d561 | Ecipekac Layer II installer |
| pcasvc.dll | 59747955a8874ff74ce415e56d8beb9c | Encrypted Ecipekac Layer IV loader (shellcode) |
While the primary purpose of P8RAT and SodaMaster is to download and execute payloads from an attacker-controlled server, Kaspersky's research did not yield any clues as to exactly what the malware provided on target Windows systems.
Interestingly, the third payload, FYAnti, is a multi-layer installer module that goes through two successive layers to deploy the last-stage remote access Trojan (Trojan) known as QuasarRAT (or xRAT).
Ecipekac: Tier I installer
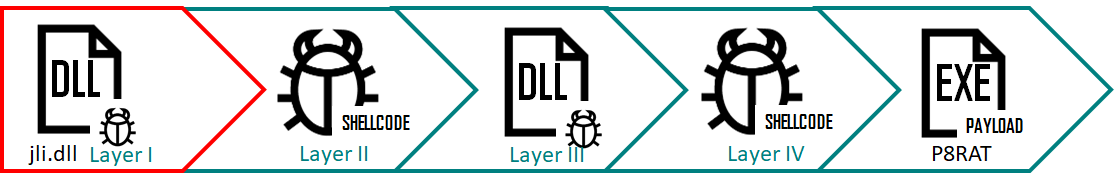
Layer I of the Ecipekac infection stream
The Ecipekac I .layer installer maliciously uses policytool.exe, a legitimate application normally packaged in the IBM development package for Eclipse, to load a malicious DLL named “jli.dll” into the current directory via the DLL sideloading technique. The 'Jli.dll' file acts as the first layer of the Ecipekac installer. This DLL has several export functions, but they all refer to a similar function with the main load feature. The installer reads 0x40408 bytes of data from the end of another DLL ('vac.dll'). The data size 0x40408 is derived from a hard-coded value of 0x40405 and is incremented until it is divided by eight.
| MD5 | f60f7a1736840a6149d478b23611d561 |
| SHA1 | 5eb69114b2405a6ea0780b627cd68b86954a596b |
| SHA256 | 3b8ce709fc2cee5e7c037a242ac8c84e2e00bd597711093d7c0e85ec68e14a4c |
| Connection time | 2033-11-13 08:50:03 |
| File type | PE32+ executable (DLL) (GUI) x86-64 for MS Windows |
| Compiler | Connector Version: 14.13, OS Version: 10.0 |
| File size | 681544 (666KB) |
| File name | vac.dll |
| data embedded at 0x66240 (size: 0x40405) |
00066240: febe d990 66de 1bc9 75b7 dc2c 3e1f 3ef2 00.066.250: 78d0 0005 5c27 A511 C122 bdf4 15e7 052c 00.066.260: af72 7e08 064c f7b9 70f0 57bf 250a 3b4d [..skipped ..] 000a6630: ee4b b1f2 294d eea1 290E aba2 6954 130 ° F ‘ 000a6640: 1267 9ab3 f8 00 0000 |
The DLL file 'vac.dll' is signed with a valid and legitimate digital signature, although it has changed in the file. At first glance, the validity of the digital signature indicates that the file was not modified after it was digitally signed.
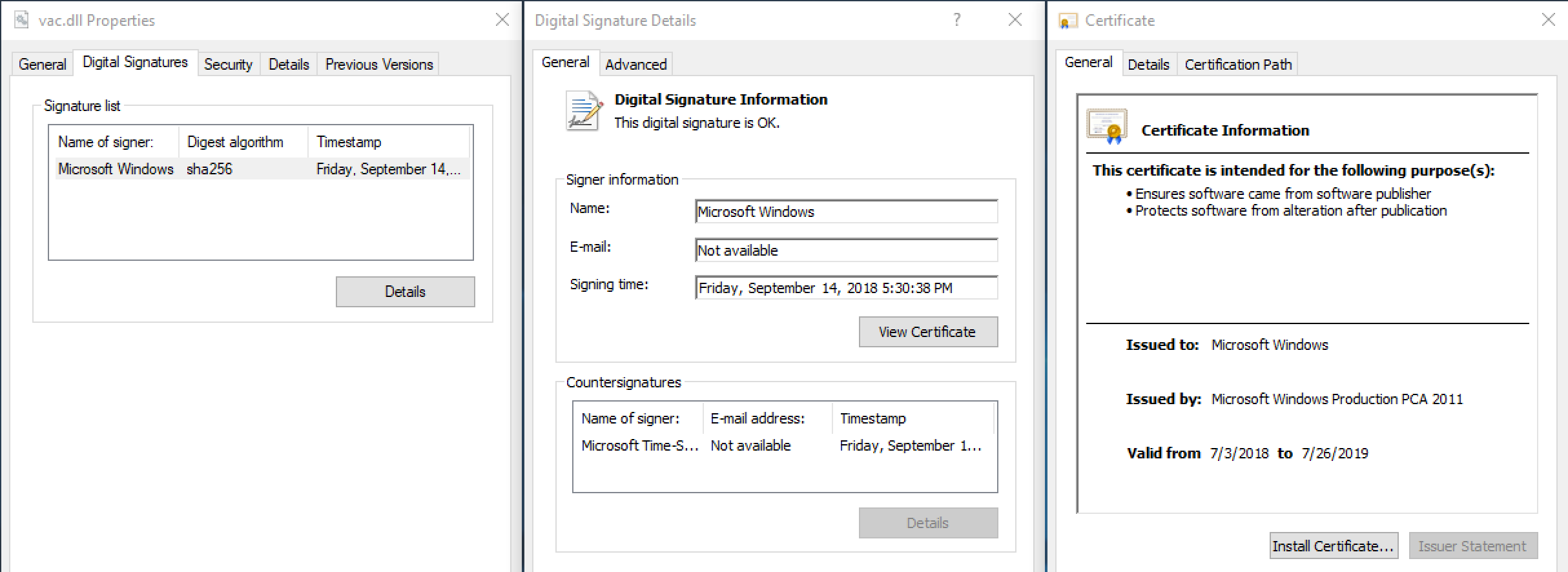
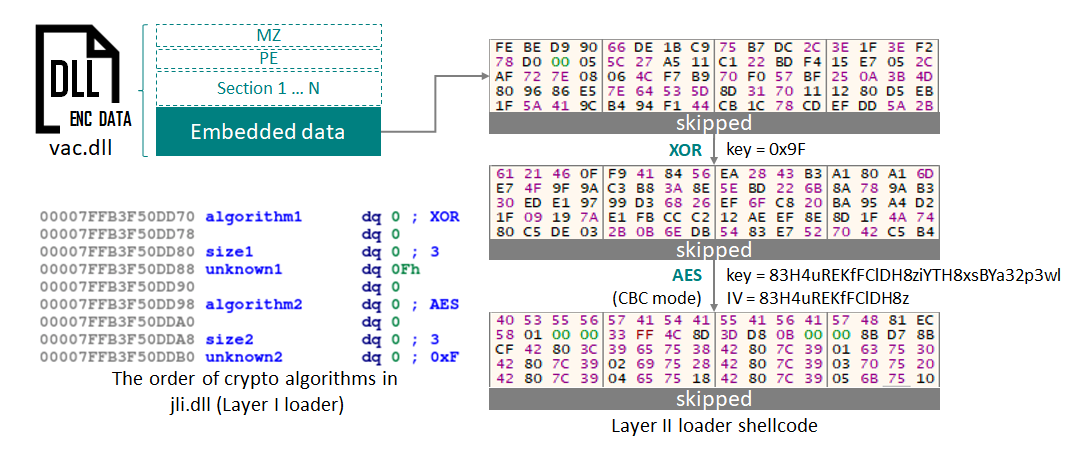
It resizes the certificate table in the digitally signed 'vac.dll' and adds its own data to the certificate table so that it does not affect the digital signature. This technique was published in BlackHat 2016 as MS13-098. The layer I loader decrypts the layer II loader shellcode from the embedded data in 'vac.dll'. Various crypto algorithms are used, such as XOR, AES, and DES. The order and combination of algorithms and decryption keys differ from one instance to the next.
Decryption flow on first installer
For example, in the example shown above, the order of encryption algorithms is a single-byte XOR using hardcoded key '0x9F', followed by AES key '83H4uREKfFClDH8ziYTH8xsBYa32p3wl' and IV key '83H4uREKfFClD . An interesting feature of Ecipekac is that attackers have implemented these encryption algorithms in their own code instead of using the Windows API. The attackers also made minor changes compared to the original app. For example, they deliberately referenced the third byte of the AES key as shown in the code below in the function related to the AES algorithm.
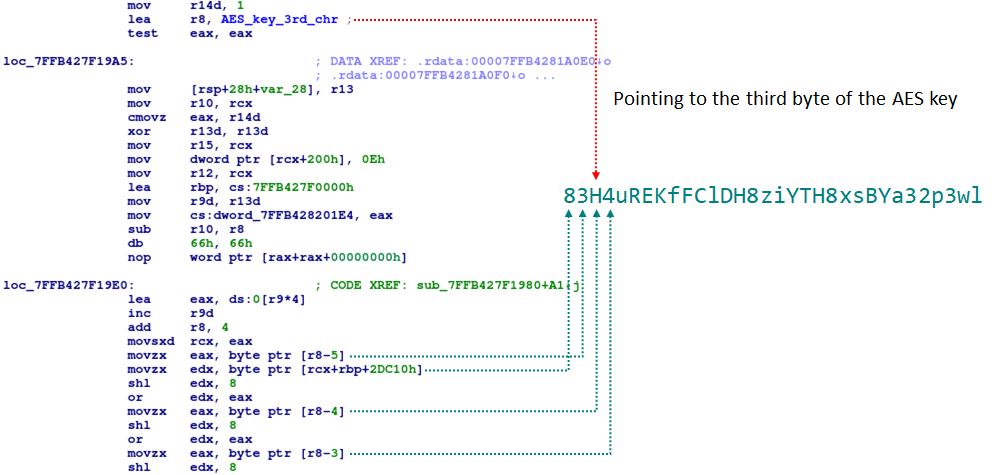
A small change in AES functionality
In addition to the aforementioned AES algorithm, the attackers also modified the DES algorithm.
Ecipekac: Layer II Installer Shellcode
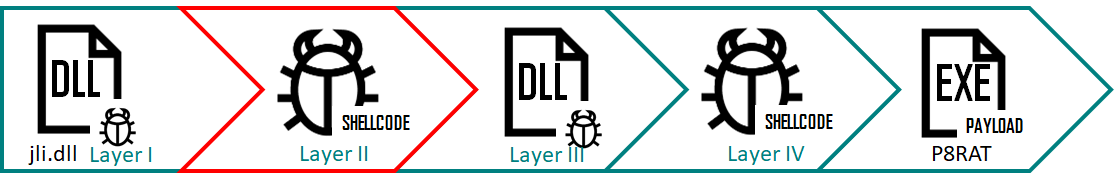
Layer II of the infection stream using Ecipekac
The Ecipekac Layer II loader is a simple shell code that contains the data of the next layer DLL in irregular chunks. First, the shellcode checks for the string "ecipekac" in this dataset. It then reconstructs and loads each piece of embedded data into allocated memory in the correct order to generate the original code of the DLL as shown below.
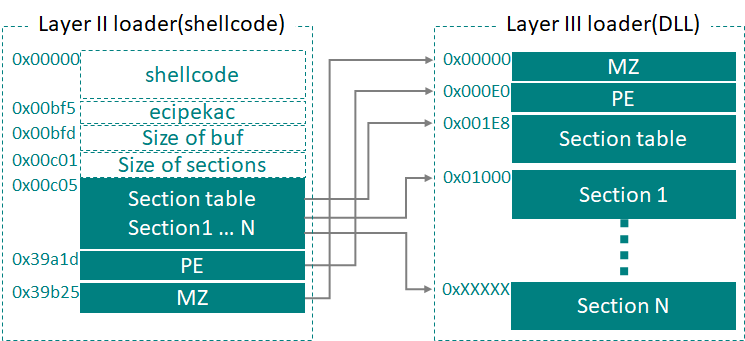
Reconfiguration for memory split PE BLOB
It then calls the entry point of the loaded DLL, which is the third layer of Ecipekac. According to our research, the magic sequence used in this module is not just "ecipekac" in any case. Instead, it has been observed that “9F 8F 7F 6F” and “BF AF BF AF” are used in a few examples.
Ecipekac Layer III installer DLL
Layer III of the infection stream using Ecipekac
The method of installing the next layer of the third layer resembles the first layer. It reads encrypted data from the end of 'pcasvc.dll' signed using a digital certificate as in 'vac.dll'.
| MD5 | 59747955a8874ff74ce415e56d8beb9c |
| SHA1 | 0543bfebff937039e304146c23bbde7693a67f4e |
| SHA256 | a04849da674bc8153348301d2ff1103a7537ed2ee55a1588350ededa43ff09f6 |
| Connection time | 2017-02-24 15:47:04 |
| File type | PE32+ executable (DLL) for MS Windows (console) x86-64 |
| Compiler | Connector Version: 14.13, OS Version: 10.0 |
| File size | 733232 (717KB) |
| File name | pcasvc.dll |
| 0x87408’de gömülü veriler (boyut: 0x2BC28) | 00087408: 98e4 1def 8519 d194 3c70 4e84 458a e34c 00087418: b145 74da c353 8cf8 1d70 d024 8a54 8bde [.. atlanan ..] 000b3010: 2c1b 6736 8935c d55d 08090 0829 5dfc 735bd35 9000b000 : 44bd35000b30000 |
Crypto algorithms are again single-byte XOR and AES CBC mode. This time it is used to decrypt the fourth loader shellcode from the embedded data of 'pcasvc.dll'. However, the sequence of algorithms is in reverse order relative to the first layer. Hard-coded keys are also different. “0x5E” is used as the XOR key, while the AES key and IV are “K4jcj02QSLWp8lK9gMK9h7W0L9iB2eEW” and “K4jcj02QSLWp8lK9” respectively.
Ecipekac: Layer IV Installer Shellcode
Layer IV of the infection stream using Ecipekac
During the investigations, three different types of shell codes were found that were used as the fourth layer of Ecipekac.
Layer IV loader shellcode – procedure of first type first shellcode behaves same as Ecipekac Layer II shellcode. the only difference is the embedded PE, which in this case is Ecipekac's final charge. The payload of the first type of shellcode is either "P8RAT" or "FYAanti loader". An analysis of these loads is presented in the following sections of this report.
Layer IV loader shellcode – second type shellcode is completely different from other loader types. This shellcode has a unique data structure shown in the table below.
| Ofset | Sample Data | Explanation |
| 0x000 | 90 90 90 90 90 90 90 90 | Number to check before proceeding with data processing. |
| 0x008 | 0x11600 | Size of encrypted data |
| 0x00C | A9 5B 7B 84 9C CB CF E8 B6 79 F1 9F 05 B6 2B FE | 16 byte RC4 key |
| 0x01C | C7 36 7E 93 D3 07 1E 86 23 75 10 49 C8 AD 01 9F 6E D0 9F 06 85 97 B2 [skipped] |
Payload encrypted by RC4 (SodaMaster) |
This shellcode verifies the existence of the magic number “90 90 90 90 90 90 90 90” at the start of this data structure before starting to decrypt a payload at offset 0x01C using RC4 with the 16-byte key “A9 5B 7B 84”. “9C CB CF E8 B6 79 F1 9F 05 B6 2B FE”. The decrypted payload is “SodaMaster”.
Layer IV loader shellcode – the third type of Final Shell code is a Cobalt Strike stager. Several different Cobalt Strike phased shellcodes have been confirmed to be used since October 2019. Additionally, some of the observed Cobalt Strike staging examples include a setting in the HTTP header of their malicious communications to disguise them as common jQuery requests to avoid detection by security products.
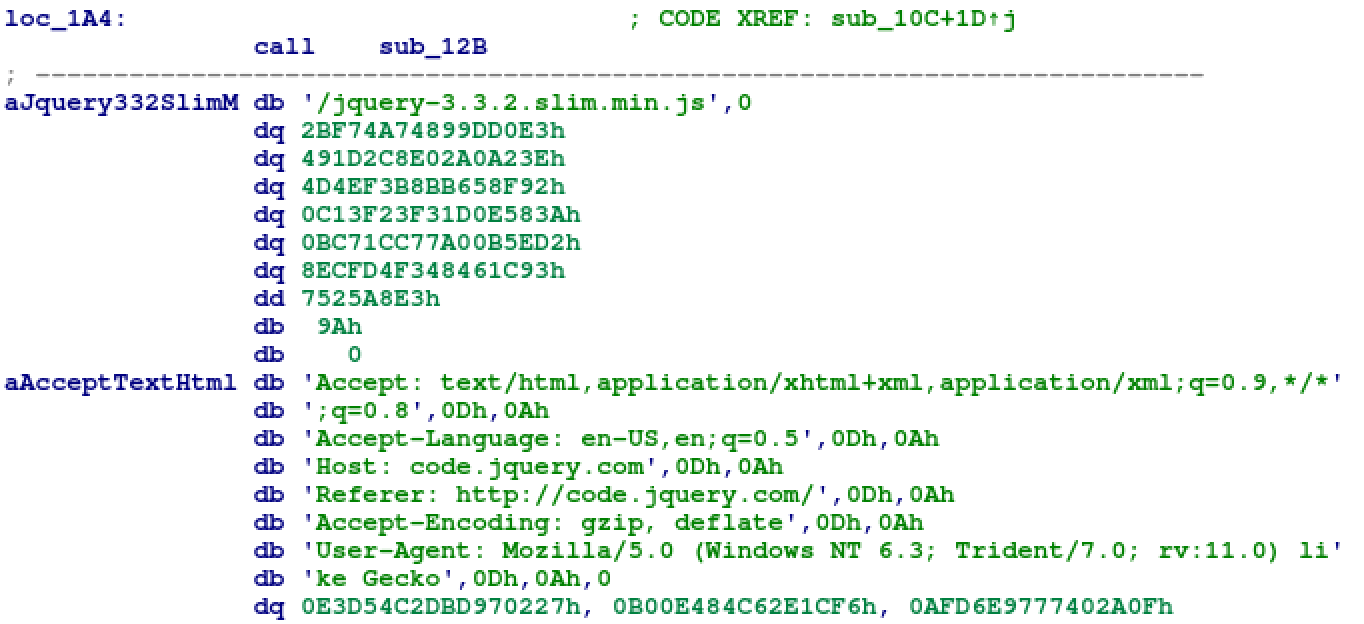
Hard-coded HTTP header to impersonate the jQuery request
The actual encoded C2 used in the HTTP header for C2 communication emulating jQuery requests was “51.89.88[.]126” with the corresponding port 443.
Attribution of Attack:
Based on the research conducted by the researchers, it is considered with great confidence that the APT10 threat actor is behind the “A41APT” campaign.
This reference is based on the following points;
First, the hardcoded URL “www.rare-coisns [.] com” from an x86 SodaMaster sample was also specified in accordance with the geographic location of the VirusTotal sender in relation to the effectiveness of APT10 targeting the finance and telecommunications sectors of Turkey.
Second, the A41APT campaign has similarities with the APT10 events described in a Cylance blog post. These include Ecipekac Loader of the FYAanti loader using the CppHostCLR technique and QuasarRAT which is used as the final load of FYAanti. Also, as noted in the Symantec blog post, the CppHostCLR technique for injecting the FYAanti installer .NET installer and QuasarRAT was similar to the activities of the APT10 group discovered by BlackBerry.
Cylance threat research team. Finally, there are some similarities and common TTPs to those outlined in the previous TIP report on APT10 activities;
- Manual implementation of hash or crypto algorithms with some modifications by malware developers instead of Windows APIs.
- Crypto keys, part of crypto keys, key generation, mutex names etc. Using computed hashes (in whole or in part) for some properties such as
- Using the DLL sideloading technique to run a load in memory.
- Using PowerShell scripts for persistence and also for lateral movement.
- Using exe to remove logs to hide their activity.
- Sending victim machine data such as username, hostname, PID, current time and other attributes. (It is not specific to APT10 backdoors and is fairly common in most backdoor families.)
- It replaced the implants shortly after security researchers published their analysis of the actor's activities and TTPs.
- Targets primarily Japan, as well as overseas branches or organizations associated with Japan
However, some interesting differences have been observed in the A41APT campaign and previous events;
- Unlike previous malware samples used by APT10 such as LilimRAT, Lodeinfo and ANEL, P8RAT and SodaMaster do not contain a malware version number.
- As for the virus infection vector, the failure to identify any leading phishing emails in this A41APT campaign, which is quite common in APT10 attacks.
In general, APT10 is considered a large group of APTs running multiple simultaneous campaigns, and understandably TTPs differ from one campaign to the next. The differences mentioned here for the A41APT campaign are thought to represent a normal variation of TTP that would be expected in the case of such a large APT group.
Results
The A41APT campaign is seen as one of APT10's long-running events. This attack campaign introduced Ecipekac multi-layered malware and its payloads, which includes different unique fileless malware such as P8RAT and SodaMaster.
The most important aspect of Ecipekac malware is that outside of multiple layers, encrypted shell codes are inserted into digitally signed DLLs without affecting the validity of the digital signature. Some security solutions cannot detect these implants when this technique is used. Based on the main features of the P8RAT and SodaMaster backdoors, these modules are thought to be downloaders responsible for downloading other malware, which unfortunately has not been obtained so far as a result of research.
Kaspersky researcher Suguru Ishimaru; “The campaign's operations and implants are highly confidential, making it difficult to track the threat actor's activities,” he said.
Source:
symantec-enterprise-blogs.security.com
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












