A new phishing campaign is targeting organizations in Eastern European countries with the Remcos RAT malware, with the help of an old Windows User Account Control bypass discovered more than two years ago.
The use of fake trusted directories to bypass Windows User Account Control is prominent in the attack, as it has been known since 2020 but continues to be effective today.
Watch out for bills!
Phishing campaign emails are sent from top-level domains that match the recipient's country and are often disguised as invoices, tender documents, and other financial documents.
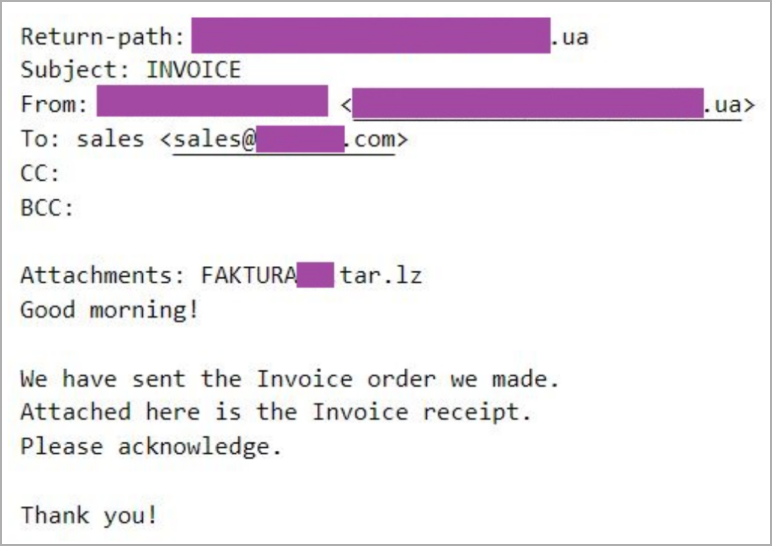
Sample email from the campaign (SentinelOne)
You can go to the technical details of the news from Bleeping Computer.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












