Introduction
It is becoming more and more difficult to detect and prevent cyber security threats that are increasing day by day by updating themselves. It takes a long time to prevent and control data breaches that have increased after the attacks. Almost every company needs effective process management for network security, detecting, analyzing, mitigating and preventing cyber threats. A formal organizational structure that will provide this process management should be established and made sustainable.
The operations center that will provide this process management is the Security Operations Center (SOC).
Let us now examine the concept of SOC in detail.
What is Security Operations Center (SOC)?
SOC, which stands for Security Operations Center in Turkish, is a central unit responsible for monitoring and analyzing an organization's security posture. This unit includes identifying cyber threats, responding and managing security incidents. A typical SOC is a large team of security analysts, engineers, and other personnel who use a combination of manual and automated tools to manage security incidents.
The personnel of the SOC team should actively monitor all threats 24/7 and take quick action in case of an attack.
“What exactly does a SOC do?” For those wondering the question, the duties of SOC services are listed below:
- Reduces response time to stop the cyber attack as soon as possible.
- Prevents minor security incidents from turning into major data breaches by reducing the impact of cyber attacks.
- Tracks all IT assets and maintains security visibility by implementing real-time monitoring. Informs the company of risks through frequent reporting so that the company can make informed cybersecurity decisions.
- Informs the company of risks through frequent reporting so that the company can make informed cybersecurity decisions.
- Follows the latest threat trends in the industry to prepare for emerging security threats.
Security Operations Center Core Components
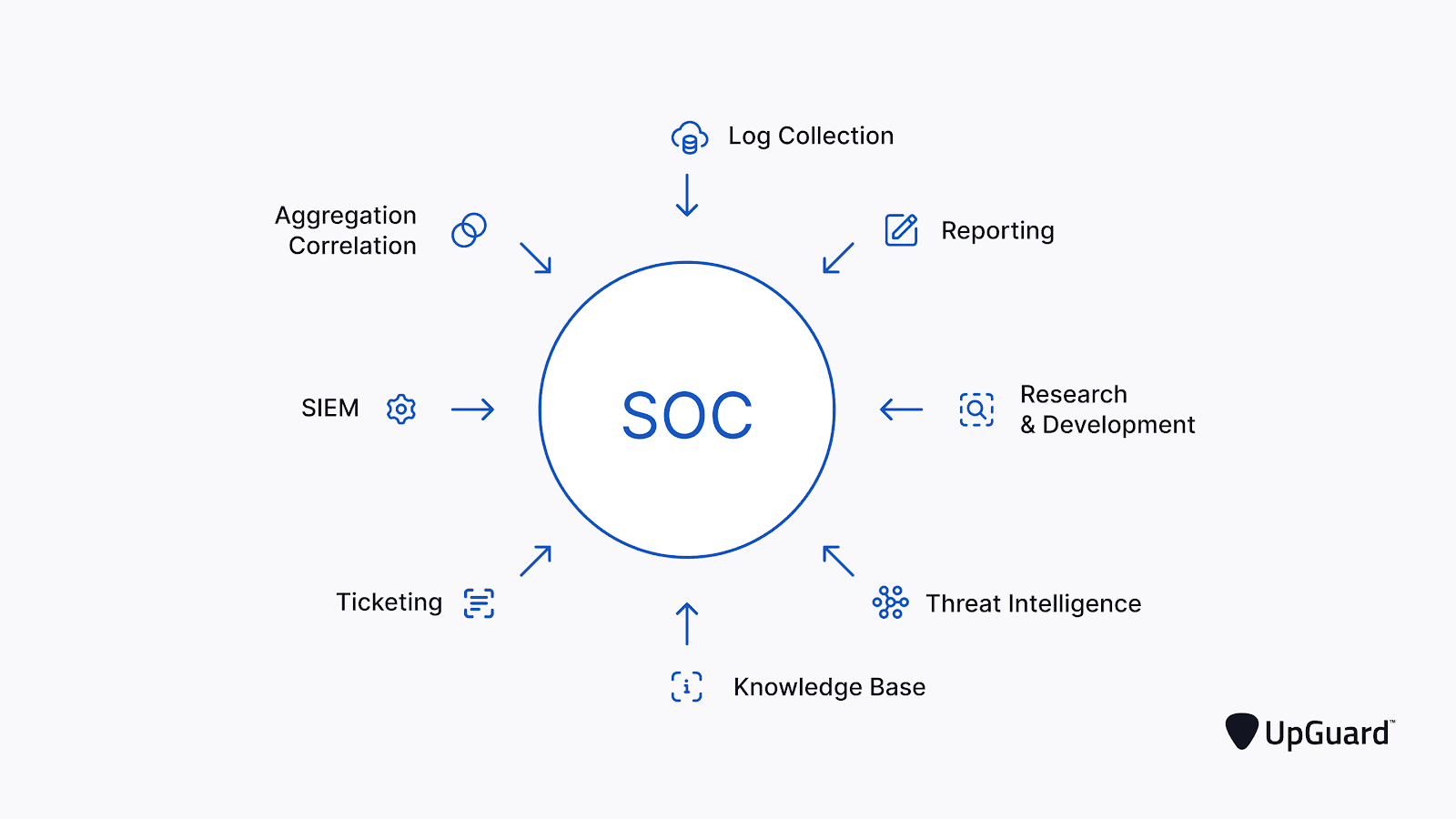
Once the scope of the SOC has been defined, its infrastructure must be designed. Multiple technological components are correlated with each other. Some of the mentioned security solutions are listed below with details;
Firewall: Prevents malicious intruders from accessing a network over the Internet by blocking unauthorized access.
Intrusion Detection System (IDS) / Intrusion Prevention System (IPS): The intrusion detection system (IDS) monitors a specified network and sends an alert when malicious network/system activity is detected.
An intrusion prevention system (IPS): It offers the same monitoring and detection capabilities as an IDS, but can prevent intrusions as they occur.
Governance, Risk, Compliance (GRC) Tool: Ensures that an organization's operations comply with applicable rules and regulations such as GDPR, CPAA, HIPAA, PCI DSS.
Endpoint Detection and Response (EDR) Tool: The Endpoint Detection and Response (EDR) tool provides endpoint security for networked devices.
SIEM: Network devices, servers, domain controllers, etc. collects security data from information systems.
Log Management System (LMS): Centralizes data from various network endpoints by collecting and storing log files in a single location.
Vulnerability Scanner: Checks networks, computers, and applications for known vulnerabilities. Helps vulnerability management by identifying new vulnerabilities.
Penetration Testing: Penetration testing is reported by revealing existing system, network, and application vulnerabilities and the way in which a threat actor can exploit them.
Application Security Tool: Provides software applications with full lifecycle protection against external threats.
SOAR Tool: It provides the collection and analysis of data of security events.
User and Asset Behavior Analytics: Identifies regular network usage trends to establish the expected behavior pattern and detects anomalous behavior to highlight suspicious activity, particularly insider threats.
Threat Intelligence Platform: Collects and organizes threat intelligence data from a variety of sources and formats.
Types of Security Operation Center
There are 7 different types of SOCs classified according to their location and personnel.
These;
Private (Self-directed) SOC: Model located within the company and managed by internal personnel.
Distributed (Co-Managed) SOC: Hybrid model consisting of a mix of in-house SOC analysts working with a third-party managed security service provider (MSSP).
Managed SOC: Model managed by a third-party MSSP as full control.
Multifunctional SOC (SOC / NOC): It is a special SOC model that works with personnel performing both SOC and NOC (Network Operations Center) functions.
Virtual SOC: A special SOC model, usually managed by part-time employees or an MSSP that responds to major security incidents and alerts.
SOCaaS (SOC as a Service): An outsourced cloud-based SOC model that organizations can use for full or partial SOC functionality.
The Challenges of Building a Security Operations Center
As a result of research, some common challenges to effectively implement SOC have been identified by cybersecurity experts, these are;
- Amount of Overhead: Many companies use a variety of tools to provide the SOC team with the necessary data. Although these vehicles vary according to the SOC service they receive, they are usually found in their own infrastructure. In this respect, SOC can cause security operations to become costly and complex.
- Incoming Alerts: Your SOC team can add multiple tools to obtain more data and aim to receive alerts. Asking relevant analysts to respond to too many threat notifications can cause threat fatigue. These warnings can sometimes waste the time and energy of the team with the FPs they give.
- Qualified Personnel: Many IT managers complain that it is difficult to find the qualified personnel required for the SOC analyst role. Some SOC teams are understaffed and their personnel do not have the appropriate skills to respond quickly to threats.
Security Operations Center Team Roles
SOC personnel follow a hierarchical structure determined by the level and area of expertise of each team member. There are four tiers of team members in the overall SOC hierarchy.
These layers are listed below:
Tier 1 -Analysts
They are the front line responders to SIEM alerts. Performs prioritization to prioritize security issues that need to be escalated to
Tier 2 -Analysts
It handles security alerts raised by Layer 2 analysts, such as security breaches. They have a higher level of expertise than Tier 1 analysts, including advanced forensics, threat intelligence, and in-depth malware detection experience. After identifying the root cause of any cyberattack, Tier 2 analysts plan and execute remediation efforts.
Tier 3-Analysts
Tier 3 analysts have additional skill responsibilities to Tier 2 analysts. For example, threat hunters are quite proficient at identifying any network vulnerabilities using advanced threat detection tools. Other Tier 3 analysts include:
- Forensic analysts
- Compliance auditors
- Cyber security analysts
Tier 4 -SOC Manager
Layer 4 is the highest level of the SOC hierarchy. SOC managers have the specialist knowledge of a Tier 3 analyst with additional leadership and management skills. They are responsible for applications such as:
- Overseeing the activities, performance and training of the entire SOC team,
- Leading the response plan during major security incidents,
- Facilitate communication between the SOC team and the wider organization,
- Supporting regulatory, industry and operational compliance,
Advantages of Security Operations Center
Other advantages of SOC, which is a main mechanism for organizations to prevent and respond to cyber threats, are listed below:
- Advanced incident response time and management application,
- Decreased time difference between consensus and perception,
- Uninterrupted security monitoring and evaluation process,
- Gathering security resources, software and hardware assets for holistic approaches,
- Optimized collaboration and communication for effective reactive and proactive responses,
- Cost savings by preventing damage caused by security incidents,
- Increased security,
- Providing enhanced security for sensitive data,
- Ensure compliance with government regulations and industry standards.
The Importance of Security Operations Center
Building a good SOC team is essential for almost any organization. It is very important that a robust SOC is active 24/7 and that the workflow is managed smoothly. The policies and procedures that guide the organization's employees should be an integral part of the SOC team. It is an ongoing and active process to serve the team and the organization as a whole in the best possible way. Monitoring and analyzing the work of the security operations center helps organizations prioritize and better assess their security needs.
Conclusion:
Although there are some difficulties in establishing the SOC team in organizations, if we want to be protected from cyber threats and data breaches with the majority, we should create the SOC team. Thanks to the SOC team created, we provide cyber threat protection during active and proactive working hours, and we provide an organized security measure without skipping any step thanks to the expert analysts placed gradually. At the same time, SOC will provide the requested up-to-date reporting in case of any problems or inspections.
In short, thanks to SOC, every employee and manager in the organization will work with peace of mind in an organization with a low risk level.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












