Forensic Informatics; It is the whole of the examination process that ensures that the digital evidence is prepared to be presented in an understandable way in cybercrime cases without destroying its integrity and harming it by using scientific methods in order to illuminate the crime. It also interacts with the cyber security field, as it is used in cybercrime cases to gather evidence in accordance with legal procedures. The main purpose of forensic computing is to reveal the connection between the examination of traces and digital evidence and the event in computer crimes where computers are examined for harmful or illegal situations.
It is called Computer Forensics in English and means Computer Criminalistics in Turkish. However, it is called Forensic Informatics in our language. As in criminalistics, he searches for answers to 4N1K questions on digital evidence, and apart from mobile phone, computer and usb memory examinations in our country; It includes many types of examinations besides computer examination such as spyware detection, shorthand, decryption on evidence.
In the incident response phase, the devices that are thought to contain evidence are scanned in accordance with the forensic analysis process and the data bearing evidence is obtained. Incident response phase also includes the operations of examining a live system by running commands on it. Incident response steps are generally in order; It progresses in the form of detecting the infiltration method, determining the steps of the attack, obtaining evidence in accordance with the forensic process and standards, closing the gaps.
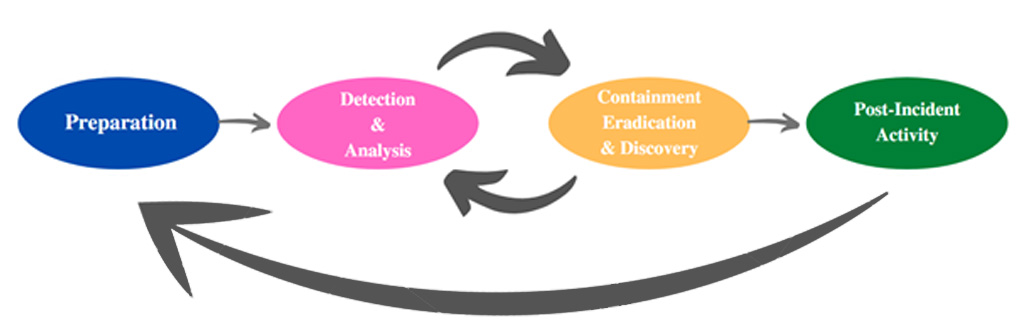
One of the most important issues in the incident response process is to detect the infected device and isolate it from other devices. Thus, the damages that may occur are minimized and the time and cost to return to the normal process are reduced.
The solutions used in case of a possible event are of great importance. The solutions used to speed up the incident response process (taking quick action) are also of great importance in keeping the process under control. It is also important to have a trigger feature in the solutions used, which will speed up the investigations of SOC analysts and responding to the event. With Trigger generating alarms for the solutions it is integrated with, SOC analysts can be instantly informed of the attack that occurs quickly.
In order to make the best investigations on the isolated device, the product used can be integrated with SIEM/SOAR/EDR products quickly, and the trigger feature creates positive effects on analysts' examinations and makes their work easier.
Solutions that can be considered as "Tactical" in Forensic Informatics, where speed, integration and advanced trigger features are enabled with these integrations, come to the rescue of experts and SOC managers and employees. The need for image acquisition in traditional Forensic Informatics is not required in tactical solutions, and therefore the desired areas can be examined in depth in a very short time. Time and resources are saved for preliminary reporting and review by collecting necessary evidence from extremely important files such as Browser, Registry, Eventlogs, Content, Prefetch, Clipboard, DNS Cache and RAM content.
Stay safe..
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












