Work from home and Bring Your Own Device – The continued rise in BYOD trends has made digital authentication solutions even more important. Indeed, hardware and software solutions such as token, QR code, SMS, face recognition, fingerprint recognition or Single Sign-On are effective measures to be taken against the risk of leaking corporate data by remote unauthorized access. While nearly all of our employees are working from home, we have a right to know if the person accessing our systems is “really” our employee.
Network and internet access are key for almost all roles in organizations, but the risks posed by this requirement must be balanced. The main goal of every business is to provide secure and controlled network access that provides the right access to the right person at the right time without sacrificing security.
Single Sign-On should be positioned as a method of providing secure identity and role-based access to the network. It integrates with existing authentication systems such as Active Directory or LDAP, providing identity-based security for corporate users without inconveniencing users or creating additional work for network administrators. Digital Authentication solutions are built on the foundation of Single Sign-On, providing a wider range of user identification methods and adding greater scalability. These solutions are secure authorization solutions for corporate networks that identify users, query and verify access permissions of third-party systems, and forward this information to Firewall devices for use in identity-based policies.
Digital Authentication technologies provide transparent identification with multiple methods:
- Via Active Directory Domain Controller
- Integrating with SSO Mobile App that detects login/Login, IP address changes and session termination
- With FSSO Portal-based authentication with monitoring tools (Widgets) to reduce repetitive authentication needs
- RADIUS by monitoring account start records
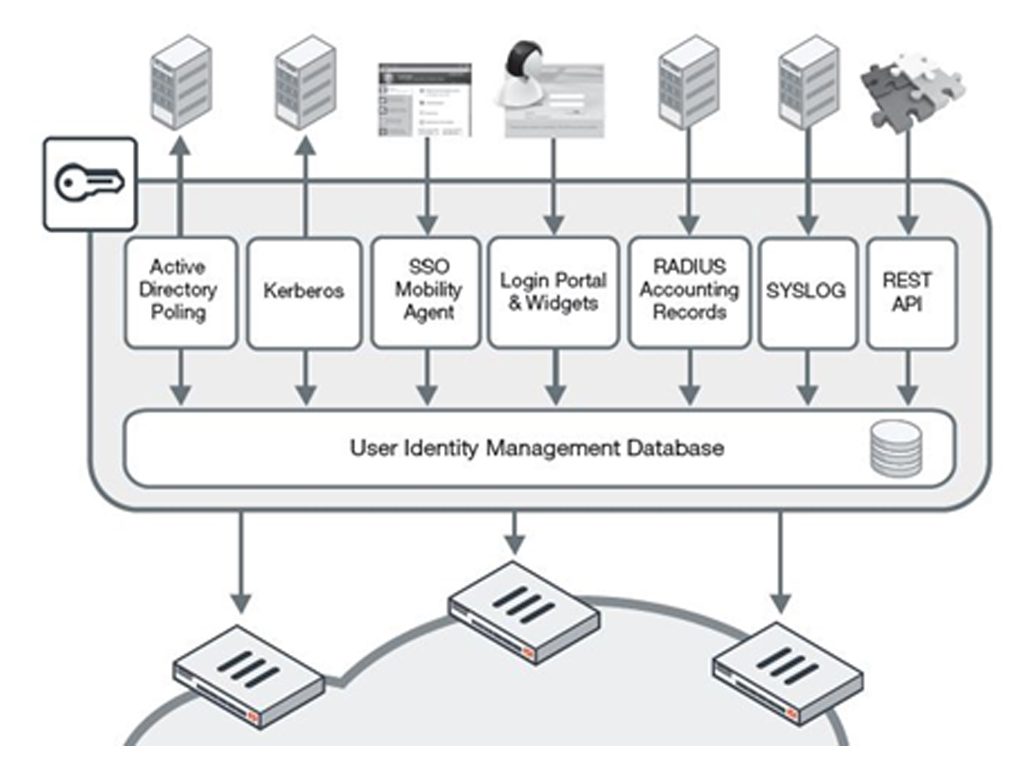
Digital Authentication integrates with third-party LDAP or Active Directory systems, communicating with Firewall to enforce group or role data and use in identity-based policies. These technologies are completely flexible and can use any or a combination of these methods. For example, in a large organization, AD polling or SSO Mobility Agent may be chosen as the primary method for transparent authentication with return to portal for non-domain systems or guest users.
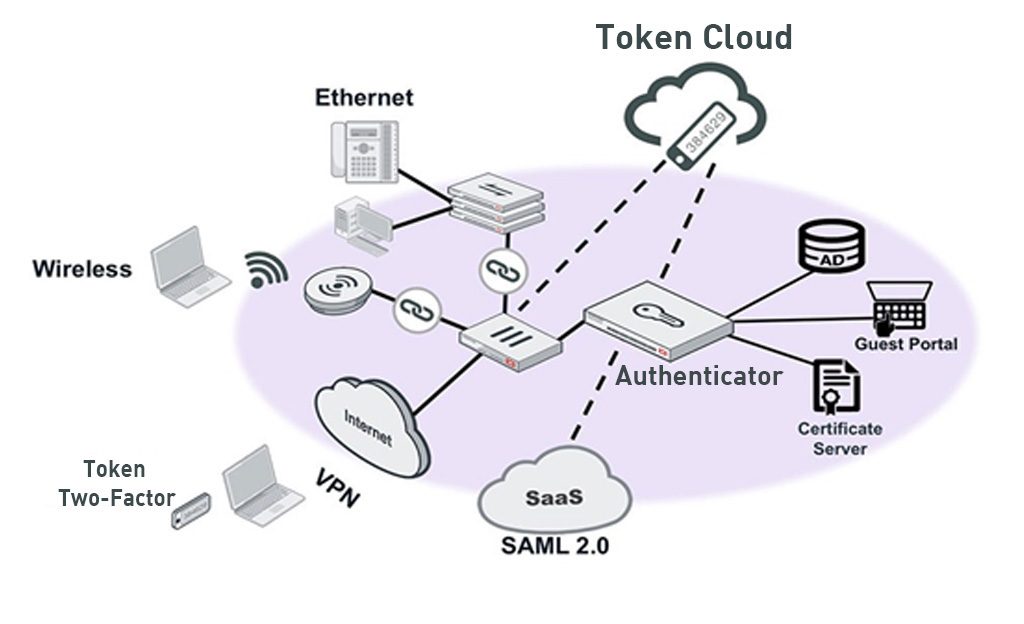
In summary, Digital Authentication solutions; With the effective authentication and access management structure they offer, they reduce the risk of unauthorized access to the network. In addition, it simplifies our processes by allowing us to keep records of access to internal data and applications, control, make corrections, and allow/deny access according to each user's account rights.
Working with User Identity Management, existing authentication and Single Sign-On systems; It strengthens the security infrastructure by providing scalable Multi-Factor Authentication, RADIUS, LDAP and 802.1X Wireless Authentication, Certificate management and Single Sign-on.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












