A new vulnerability has been disclosed in the WinRAR trialware file archiver utility for Windows that can be exploited by a cyber attacker to execute arbitrary code on targeted systems, highlighting how vulnerabilities in such software can be a gateway to a host of attacks.

The bug tracked as CVE-2021-35052 is affected by the trial version of the software running version 5.70. “This vulnerability allows an attacker to intercept and modify requests sent to the application’s user,” Positive Technologies’ Igor Sak-Sakovskiy wrote in a technical paper. Said. “This can be used to perform remote code execution (RCE) on a victim’s computer.” Sak-Sakovskiy noted that WinRAR research began after observing a JavaScript error generated by MSHTML (aka Trident), a custom browser engine for Internet Explorer that is used in Office to render web content within Word, Excel, and PowerPoint. The documentation causes the vulnerability to be discovered when the error window is displayed every three times when the application is started after the trial period has expired.
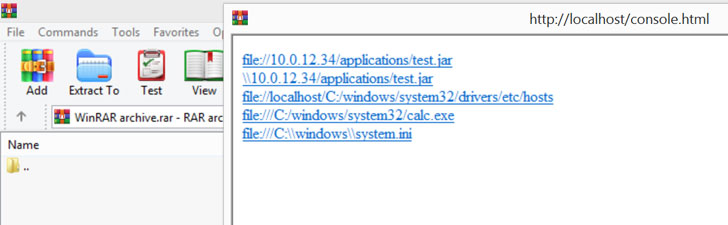
An attacker who already has access to the same network domain can launch ARP attacks to remotely launch applications, obtain local host information, and even run arbitrary code. “One of the biggest challenges facing an organization is the management of third-party software. Once installed, third-party software has access to read, write, and modify data on devices accessing corporate networks,” Sak-Sakovskiy said. “It is impossible to audit every application that can be installed by a user, and therefore policy is critical for managing the risk associated with external applications and balancing that risk against the business need for various applications. Mismanagement can have far-reaching consequences.”
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”TIKLAYIN” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]KVKK, ISO 270001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen[/vc_cta][/vc_column][/vc_row]












