Social engineering is the process of identifying weaknesses in human behavior and abusing them by manipulating them.
Although it is a difficult situation for an attacker to infiltrate the targeted system and access critical information, it is possible for him to achieve his goal by performing this process with social engineering. It is mainly used to describe human relationships or people’s carelessness.
In social engineering attacks, the target can be individuals or employees of any system. Attackers will collect information about the person or institution and use it in line with their goals. Then, the scenario is processed and the attack steps are completed.
These attacks target people's weaknesses and fears. Although it is obvious that a critical question directed to the target person will not be answered under normal conditions, it will be possible to reach the answer with social engineering methods. In this regard, the attacker will act to deceive the target person by making his work legitimate.
Social Engineering Methods
- Shoulder Surfing:

Shoulder surfing is a type of social engineering attack based on observing the action and learning information that may be confidential at the time of the user login process performed in public areas. A person may be exposed to shoulder surfing while logging into banking, e-government, and hospital systems, as well as a social engineering attack while logging in to social media and entering the password of his computer in the office. In short, it is a situation that can be encountered in every moment of daily life. In order to prevent this situation; It is recommended that you do not enter any of your data that may be confidential in public areas and that you take physical security in this regard.
- Dumpster Diving:
Garbage mixing is one of the social engineering attacks to be applied to people. Even if a person renders materials containing data that they think have lost their functionality, it can be very useful for a social engineering attacker. This process; There may be notes thrown into the trash in the physical environment, draft reports, credit card slips, various receipts and transcripts. In the digital world, this technique; It can be obtained from areas such as an idle computer hardware, various data storage units that have lost their functionality, and deleted drives. All these methods; They are a method that will allow the attacker to obtain detailed information about the person they are targeting. In this context, in order not to be exposed to any garbage mixing attack, the data should be stored in a masked manner and destroyed by appropriate methods if necessary.
- Trojan horse:

A Trojan horse (trojan) is malicious software that usually appears to be legitimate software but actually runs maliciously in the background. It is frequently used in social engineering attacks because it is not understood to be harmful at first sight. Trojan; After infecting the system, it can infect the machine, self-replicate in the background and cause critical data to be stolen.
Maltego
One of the tools used in social engineering attacks is the Maltego tool. Maltego is a compatible tool for Windows and Mac that comes preinstalled on Linux systems. It has the feature of actively and passively collecting information.
The Maltego tool is run through the Kali Linux operating system. By searching Maltego from the search engine, the tool is entered.
In order to use the tool, you must be a member from the specified area. After the necessary member transactions, the following screen will welcome you.
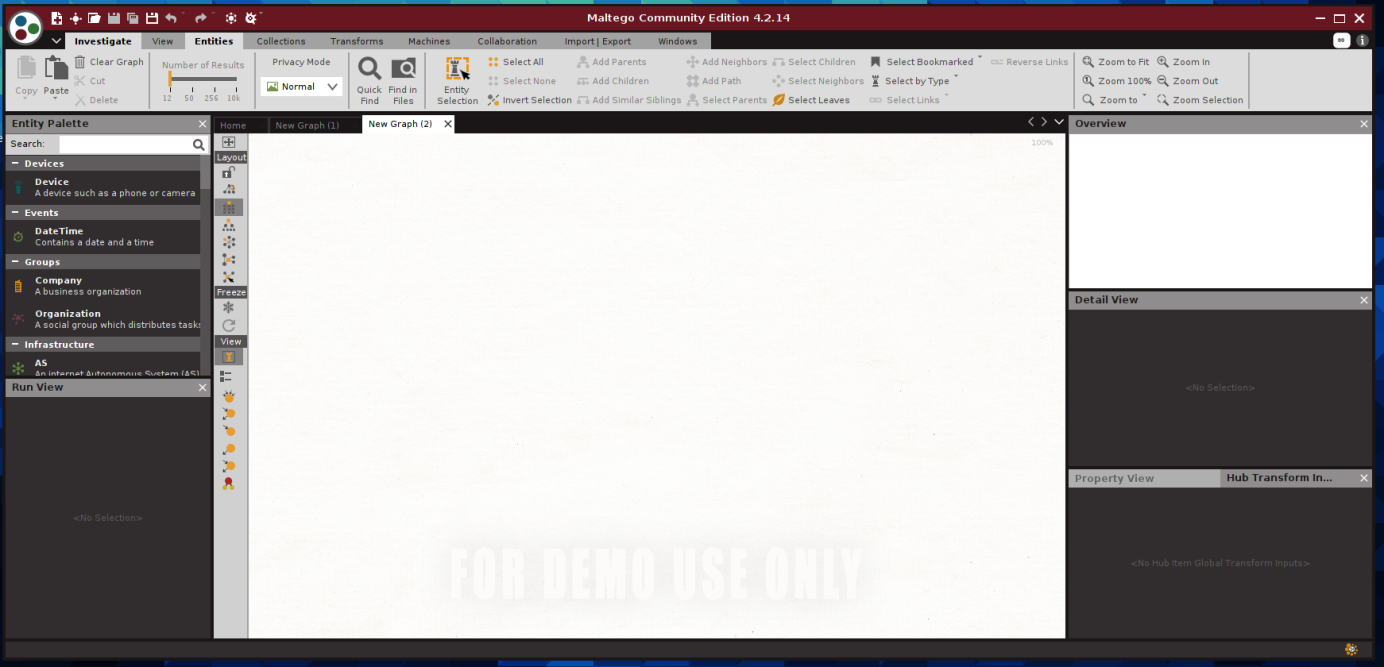
There are various fields on the left side. From here,
- Domain names
- Whois information
- IP address
- Network Detection
- Email address collection
- Telephone, fax numbers
- It is possible to search and collect information for social networks.
To obtain information about a website; Select the "Domain" field on the left side and add it to the empty field with the help of drag-and-drop. Double-click on the "paterva.com" field that appears on the screen and type the address of the website you want to collect information from. The address “sans.org”, the site from which we want to collect information, has been added to the specified field.
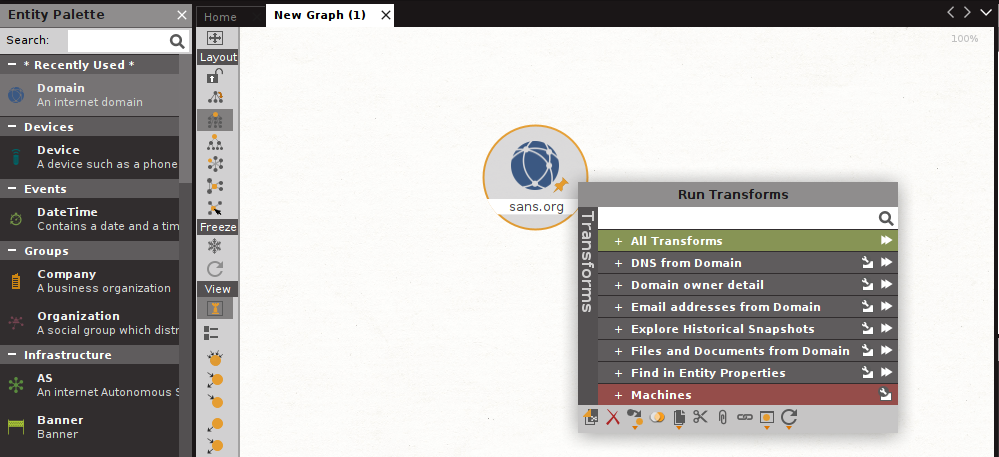
Right click on the field and select “All Transforms”. Data collection begins by clicking the "Run" button in the "Required input" window that opens. It is possible to reach detailed information about the domain by making a detailed examination on the outputs obtained.
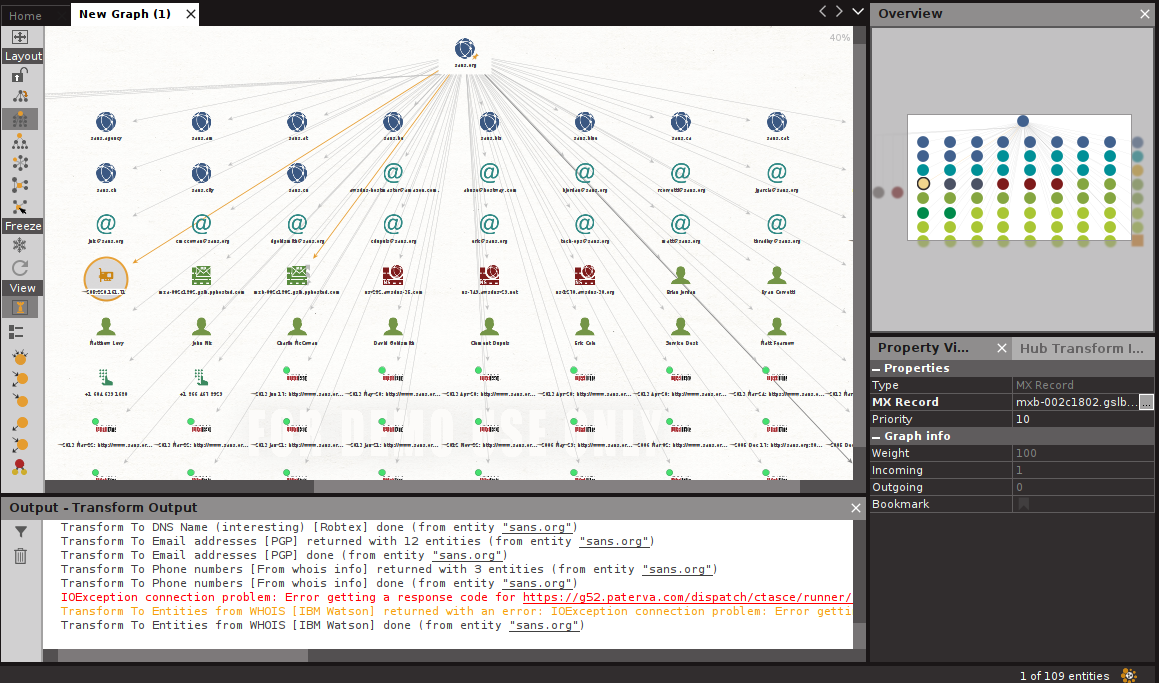
The information that can be obtained with the diagram on the screen appears. With the vehicle; domain, e-mail, IP address, contact, phone number, MX and NS records information are accessed. Mail Exchanger is a DNS record that supports mail servers running mail addresses belonging to the domain name. If it is Name Server, it is necessary to add the information that the domain name is the name server to be used in the query. You can also customize the resulting graphic with the buttons on the left side area.
As a result, detailed examinations can be made about the subject that you want to learn about, and it is possible to access detailed information with the Maltego tool.
Solutions to Prevent Social Engineering Attacks:
- A professional attacker can minimize your suspicion by making the attack appear perfectly legitimate. In such a case, you can confirm the situation from the necessary people and systems, and you can minimize the risks by verifying the requested data in this way.
- During a possible case; When communicating with the attacker, you are told that you need to hurry and if there are various requests from you, you should answer these requests by questioning.
- You should manage the incoming requests in a cold blooded manner, and if he/she wants you to share data, you should tell the other person in an explanatory and clear manner that it is not appropriate to share the mentioned data.
- Attackers can often choose when people take breaks or are not focused on their work. You should be more cautious in the actions you take.
- It is recommended that you carefully read incoming mail and messages. It should not be forgotten that the weakest link of cyber security is defined as the human factor.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












