An unpatched design flaw in Microsoft Exchange's implementation of the autodiscover protocol has leaked nearly 100,000 login names and passwords for Windows domains worldwide.

In the technical report of Guardicore's Amit Serper; Autodiscover is a serious security issue because if an attacker can control such domains or have the ability to 'sniff' traffic on the same network, HTTP basic authentication can capture domain credentials.
Also, if the attacker has DNS poisoning capabilities at scale, leaked passwords and passwords are leaked when creating a large-scale DNS poisoning campaign based on these Auto-Discover TLDs [top-level domains]. It can be used systematically in DNS attacks thanks to its user information.
What is Autodiscover?
Autodiscover allows users to use only a combination of email address and password to set up email clients and retrieve other predefined settings, allows users to configure applications such as Microsoft Outlook with minimal user input.
Where Exactly Does Weakness Come From?
The vulnerability discovered by Guardicore is that web requests for Autodiscover domains go outside of the user's domain, and in the same top-level domain stated that it was a weakness found in the particular Autodiscover implementation based on the POX (“plain old XML”) XML protocol that caused the leak.
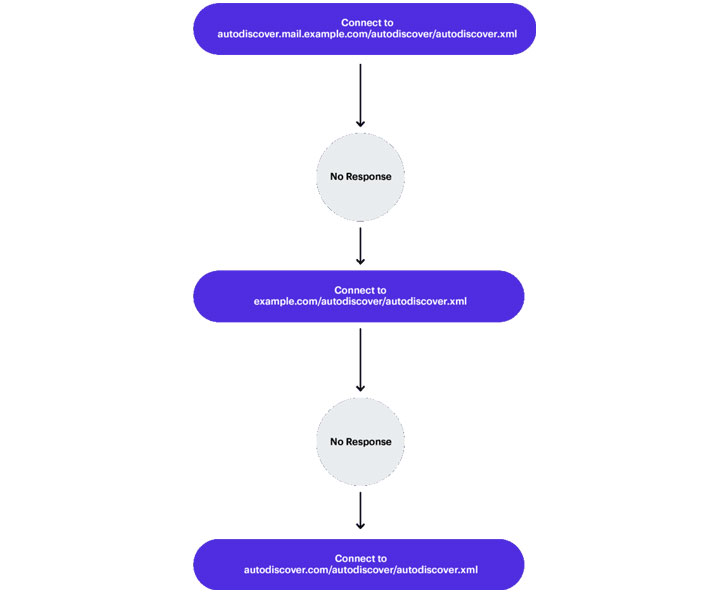
Suppose a user has an email address “[email protected]”.
In this example, the email client, the following email domain, a subdomain, and the path string starts a "back-off" algorithm that fails.
- https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- https://example.com/Autodiscover/Autodiscover.xml
- https://example.com/Autodiscover/Autodiscover.xml
The “back-off” mechanism is the main feature of this leak. Because it always tries to resolve the Autodiscover partition of the domain and it always fails. So, the result of the next attempt to generate Autodiscover URL will be:
'https://Autodiscover.com/Autodiscover/Autodiscover.xml.' This means that the person who owns Autodiscover.com will receive all requests that fail to reach the original domain.
In the worse case scenario, the researchers developed an "ol switcheroo" attack that involves a request to the client to a weaker authentication scheme (i.e. HTTP Basic authentication) instead of secure methods such as OAuth or NTLM, and requesting the email.
The domain of this attack type relies on sending and receiving credentials in clear text.
Conclusion
To reduce leaks from Autodiscover, Exchange users are recommended to disable basic authentication support and add a list of all possible Autodiscover.TLD domains to a local hosts file or firewall configuration.
Attackers will often try to get users to send their credentials to them by applying a variety of techniques, whether through technical or social engineering. However, this event brought us a protocol aimed at streamlining the IT department's operations related to e-mail client configuration;
It shows that passwords can be leaked outside the organization without anyone in the IT or security department knowing. In this case, we understand the importance of correct segmentation and Zero Trust.
This article is for information purposes and has been prepared to increase awareness against Exchange attacks and to take measures in this direction.
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












