Remote access program AnyDesk announced that it was subjected to a cyber attack in the first months of 2024 and its source code and private code signing keys were stolen. The attack puts millions of users at risk.
Attack Details:
On February 2, 2024it was announced that AnyDesk had recently suffered a cyber attack, giving hackers access to the company's production systems. Attackers managed to infiltrate AnyDesk's systems and obtained the source code and private code signing keys. These keys are used to authenticate AnyDesk's software.
Here are AnyDesk's explanations:
Following indications of an incident on some of our systems, we conducted a security audit and found evidence of compromised production systems. We immediately activated a remediation and response plan involving cybersecurity experts CrowdStrike. The improvement plan was successful. The relevant authorities have been notified and we are working closely with them. This incident is not related to ransomware.
We have revoked all security-related certificates and systems have been fixed or replaced as necessary. We will shortly revoke the previous code signing certificate for our binaries and have already started replacing it with a new one.
Our systems are designed not to store private keys, security tokens or passwords that can be used to connect to end user devices. As a precaution, we are revoking all passwords for our web portal my.anydesk.com and recommending that users change their passwords if the same credentials are used elsewhere.
To date, we have no evidence that any end user devices have been affected. We can confirm that the situation is under control and it is safe to use AnyDesk. Please make sure you are using the latest version with the new code signing certificate.
Honesty and trust in our products are of great importance to us and we take this very seriously.
https://anydesk.com/en/public-statement
Developments regarding the incident:
The cybersecurity firm said it found two threat actors, one of whom goes by the online alias “Jobaaaaa” and was advertising “a significant number of AnyDesk customer credentials for sale on Exploit[.]in” that could be used for “tech support fraud and mailing (phishing).” he stated.
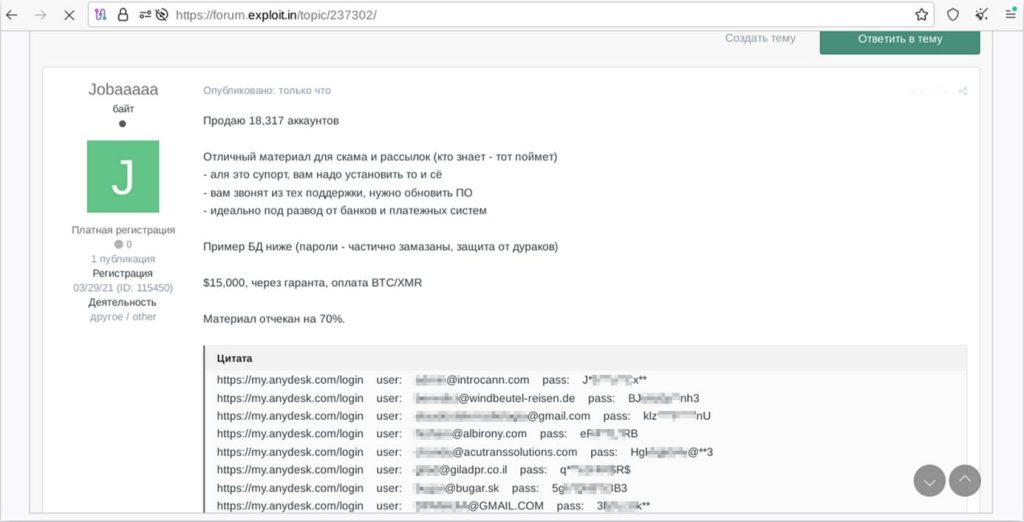
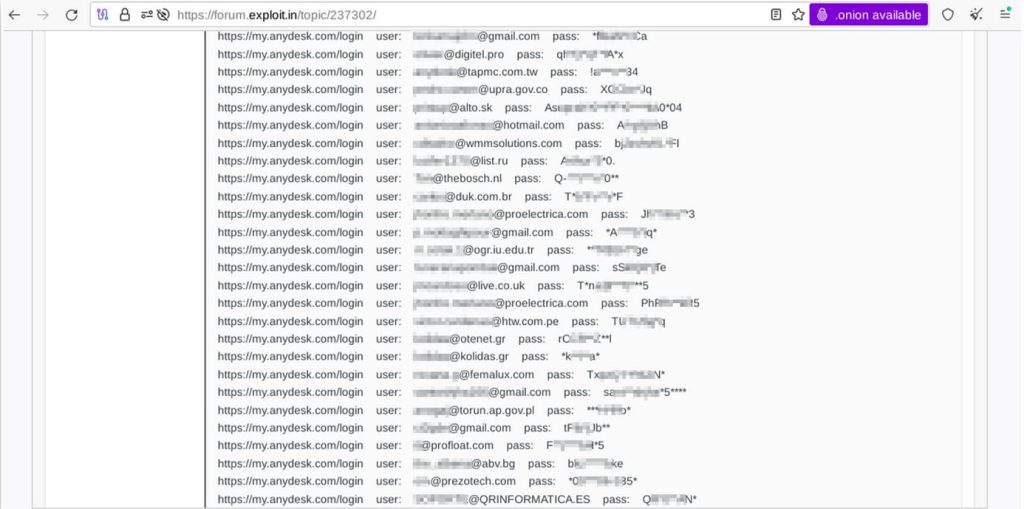
The samples provided by the threat actors involved compromised access credentials belonging to various consumers and businesses that provided access to the AnyDesk customer portal. As a security precaution, the threat actor sanitized some passwords. The threat actor offered 18,317 accounts $15,000 to be paid in cryptocurrency. He also agreed to settle a deal through escrow on Exploit. Resecurity reached out to most of the people identified as potential victims and confirmed that they had used AnyDesk products either recently or long ago. The threat actor did not share any additional information.
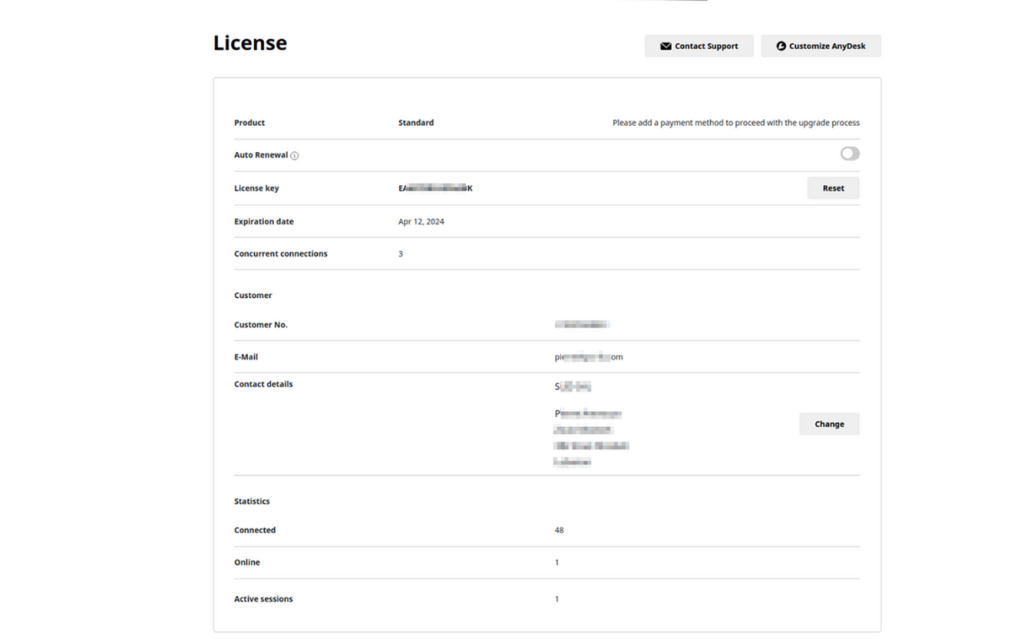
Notably, timestamps appearing in screenshots shared by the actor indicate successful intrusion dated February 3, 2024 (post-incident statement). Apparently, many customers still have not changed the access credentials or this mechanism is still ignored by the affected parties. The complexity of implementing appropriate remediation measures becomes even more important when serving a large customer base, and immediate execution of such procedures may not always be possible. In particular, this scenario can be used by threat actors who are worried about losing previously obtained access privileges. Therefore, proper planning and threat modeling required for effective remediation programs are vital. For example, through additional interactions with threat actors, Resecurity discovered that many of the exposed AnyDesk accounts listed on the Dark Web did not have 2FA enabled.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












