Miter ATT&CK Framework is a knowledge base that shows the techniques, tactics and procedures that show the actions that attackers can take to the system in the cyber world. Miter ATT&CK (Adversarial Tactics, Techniques and Common Knowledge), which has been developed by Miter since 2013, was born out of the need to systematically categorize the behavior of attackers.
In order to solve the cyber security incident in question, it is necessary to classify the activities of the attackers in the current system. Attackers will change their attack methods so that they are not detected by the current security measures. Security teams involved in resolving the cyber incident will also need to improve their approach to the incident.
It is used to determine the risks against the actions that the attacker can take in line with his target, to make the necessary improvements and plans, and to check the accuracy of the security measures taken.
MITER ATT&CK consists of several different matrices.
- Enterprise ATT&CK: It consists of techniques and tactics applied to Windows, Linux or MacOS systems.
- Mobile ATT&CK: It includes tactics and techniques applied to mobile devices.
- Pre-ATT&CK: It includes tactics and techniques that include the work of the attackers before they enter the system.
The matrix in the image below contains the techniques and tactics of Enterprise ATT&C. It also contains information about Windows, MacOS, Linux, PRE, Azure AD, Office 365, GoWorkspare SaaS, IaaS, Network, Containers.
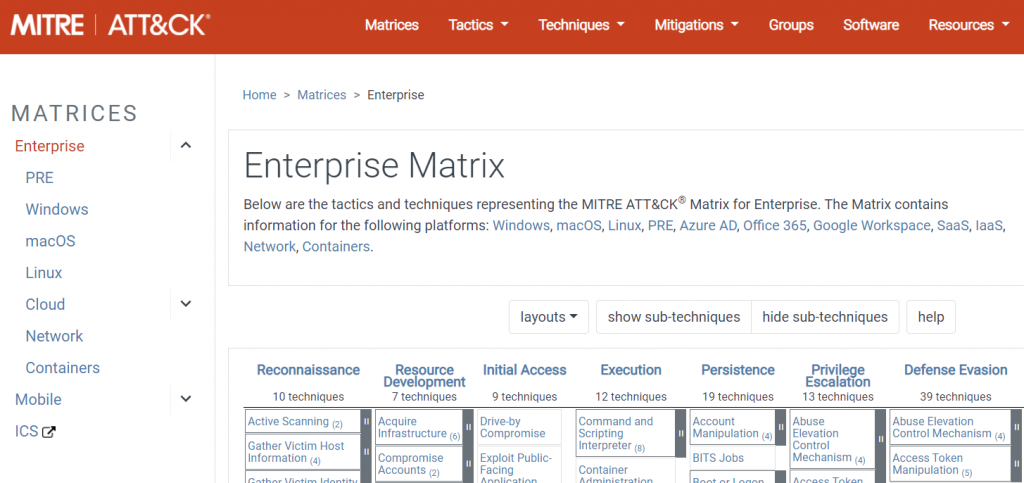
You can access the entire Enterprise Miter ATT&CK matrix here.
Enterprise ATT&CK
The techniques are as follows;
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
- Reconnaissance (Keşif)
It is the stage where the attacker tries to collect all the information that he can use in the actions he will take in the system. In this phase, it will collect active and passive information about the system in line with its objectives.Passive Information Gathering; It is a method of collecting information about the target system from services on the internet or using websites to get information without providing direct access to the target system.Active Information Gathering; It is the technique of collecting information by direct access or scanning to the target system. An attempt to collect information without permission because the system is interacted with is considered as a cybercrime pursuant to Article 243 of the Turkish Penal Code. Active information collected system information; It may contain sensitive data of the information system such as infrastructure and personnel information.
- Resource Development
Resource Development is the stage where it consists of techniques that enable attackers to create resources that they can use to support their goals. These resources include supporting the infrastructure necessary to support the attacker's control of the system, server and network services, and account operations. - Initial Access (İlk Erişim)
It consists of techniques that use various input vectors to gain initial access in a network or system. At this stage, the attacker gains access by exploiting vulnerabilities of various systems such as spear phishing and public web servers. - Execution (Yürütme)
It consists of techniques that cause the attacker to execute code on a local or remote system. Techniques that run malicious code are often paired with techniques from all other tactics to achieve broader goals such as exploring a network or leaking data. - Persistence (Kalıcılık)
It is the phase in which various techniques are used by the attacker in order not to end his access to the system he has accessed and to continue his progress in the system. For example, with a malicious software it infects the system, it can enable the attacker to gain authority in the system at every start of the machine, change the identity information and take actions to prevent the existing access. - Privilege Escalation (Ayrıcalık Arttırma)
It includes techniques aimed at increasing the current authority of the attacker in the system accessed. It will need some authorization and permissions for the actions it aims to take in the system it is in. At this point; will exploit system weaknesses, misconfigurations, and vulnerabilities. - Defense Evasion (Savunmadan Kaçınma)
It includes techniques that enable the attacker to circumvent the security measures taken for the system. Among the techniques used to evade defense in this phase are; uninstall/disable security software or hide/encrypt data and scripts. SYSTEM/root privilege
local admin authority
User account that appears to have administrative access
User accounts that have access or function to a particular system are some examples of elevated privileges. - Credential Access (Kimlik Bilgileri Erişimi)
It is the stage in which techniques to steal confidential access information such as the attacker's account username and password information are used. While trying to obtain attacker information, it aims to obtain credential dump with keylogging, Brute Force attack, attacks to password manager areas. At the same time, it is possible to use MFA deactivation, stealing website cookie information and network sniffing methods in line with its target. - Discovery (Keşif)
It is the stage that consists of the techniques that the attacker will use to obtain information about the system and network he is targeting. It is the phase in which the attacker examines and discovers the existing accounts, security software and system information in the system. - Lateral Movement (Yanal Hareket)
It includes techniques that allow the attacker to progress through the network in line with their goals. To perform the Lateral Movement, it is possible for the attacker to set up their own remote access tools, using legitimate credentials with local network and operating system tools that may be more confidential. SSH and RDP protocols hijacking, Windows remote management, remote service session hijacking are possible. - Collection (Toplama)
Saldırganın hedef sistemde belirlemiş olduğu kritik bilgileri elde etmesi ve bu bilgileri topladığı evredir. Elde edilen kaynakları arasında çeşitli sürücü türleri, tarayıcılar, ses, video ve e-posta bilgileri bulunmaktadır. Yaygın toplama yöntemleri arasında ekran görüntüsünü ve klavye girişlerini alma da yer almaktadır. Bu bilgileri; Winzip, 7Zip ve WinRAR gibi çeşitli yazılımlarla, elde ettiği dosyaları sıkıştırarak dosyanın taşınabilirliğini kolaylaştırmaktadır. Ayrıca saldırganın, lokal sistemlerden ve Sharepoint gibi paylaşım noktalarından da bilgileri elde etmesi mümkündür. - Command and Control (Komut ve Kontrol)
It is the stage in which the attacker obtains the critical information determined in the target system and collects this information. Among its obtained sources are various types of drivers, browsers, audio, video and email information. Common collection methods include taking screenshots and keyboard inputs. This information; With various software such as Winzip, 7Zip and WinRAR, it compresses the files it obtains and facilitates the portability of the file. It is also possible for the attacker to obtain information from local systems and sharing points such as Sharepoint. - Exfiltration (Sızma)
It consists of techniques that an attacker will use to steal data obtained from systems. To this end, the attacker packs, compresses or encrypts data to avoid detection. - Impact (Etki)
It consists of techniques used by attackers to disrupt usability or compromise integrity by manipulating operational processes. by the attackers; It is used to achieve goals such as destroying, corrupting, and preventing access to data.
Source
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












