Hackers are ramping up attempts to break into healthcare companies, putting additional pressure on an industry already struggling to manage the coronavirus pandemic. IT and Cyber Security Teams of healthcare organizations; They say it originated from ransomware, financial fraudsters, and hackers backed by nation-states.
It can be said that this situation has reached the highest levels with the Covid-19 pandemic. E.g; Great Plains Health announced that it normally blocks around 10,000 daily access attempts to its servers. After starting the first coronavirus antibody drug trials in November, hospital officials stated that this number has tripled on average. On some days, the trials reached 70,000 unauthorized attempts daily.
Data reported to the US Department of Health and Human Services show that more than 1 million people were affected by data breaches in healthcare facilities nearly every month last year.
In this article, we wanted to explain how hacking events, one of the most curious questions, occurred.
The following image shows vulnerability points for attackers in response to this question.
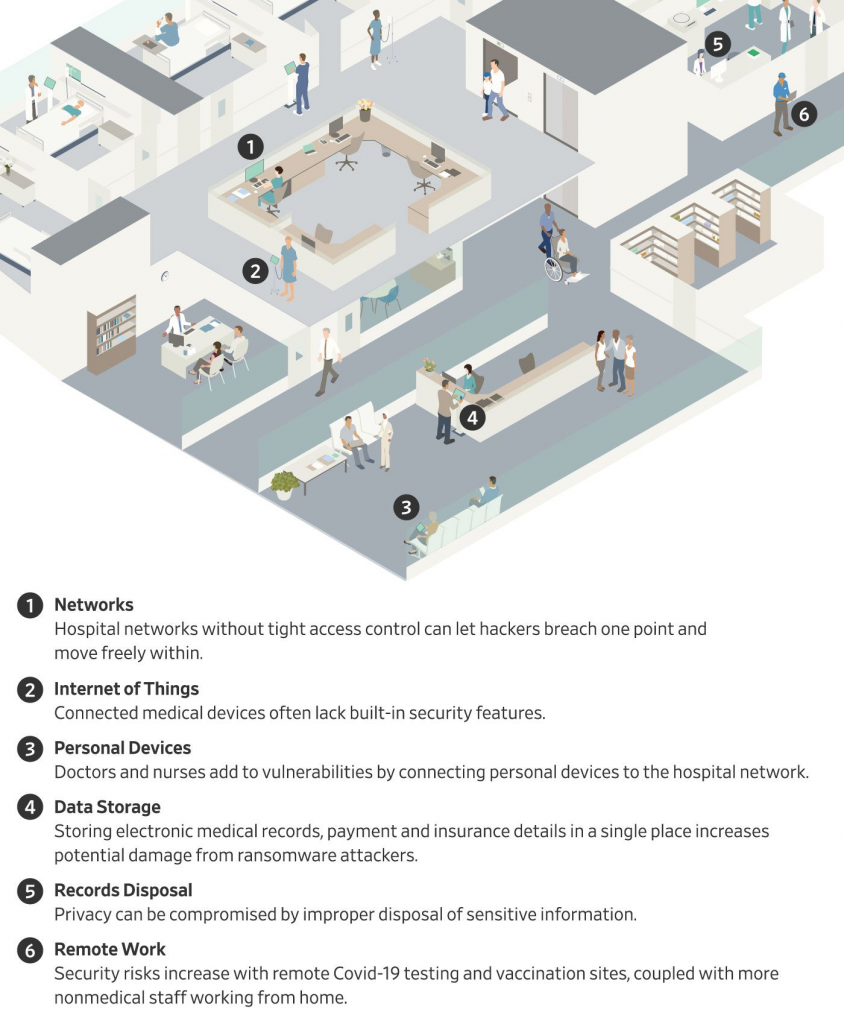

Death Due to First Cyber Attack in the World
On the night of September 11, 2020, the 78-year-old woman in severe condition suffering from aortic aneurysm was admitted to the Helios University Hospital in Wuppertal. He died here. So where is the hack in that?
The hacking case here developed as follows. Paramedics in Düselldorf, Germany, put the patient in an ambulance, then call the local university hospital to inform them about the situation and inform them of their arrival time. Meanwhile, the local university hospital states that the accident and emergency room is closed and unable to accept patients. Thereupon, the paramedics had to take the patient to a hospital 32 kilometers away from Wuppertal.
The police become suspicious of this tragic series of events and start an investigation. And the truth comes out ‘It was found that the hospital forced the ambulance to turn down due to the processes being halted as the hackers carried out a ransomware attack where they encrypt the data and then demand payment to unlock it. The attack has also forced the hospital to cancel hundreds of operations and other procedures, jeopardizing the digital infrastructure the hospital relies on to coordinate doctors, beds and treatment.

$20 million ransom demand from the Irish Department of Health
On 14 May 2021, the Irish Department of Health temporarily shut down all IT systems due to a “significant ransomware attack” and one of Europe’s busiest maternity hospitals was badly affected as most appointments were cancelled.
The ransomware used in the attack is Conti. It was developed by a cybercrime gang that is thought to be based in Russia and that provides rental services to other cyber attackers. The gang tried to contact the ministry via a chat available to everyone on the Dark Web. Messages sent to the chat showed that the gang demanded about $20 million in ransom, and also threatened to start selling data stolen during the attack, in a tactic known as “double extortion”.
The Irish government refused to pay the ransom and called on cybersecurity companies FireEye and McAfee to help, embarking on a grueling process to recover the systems.
The gang helped this process when they took the surprising step of providing healthcare with a decryption tool to unlock files encrypted by the ransomware. The criminals handed over the key for a week during which the outage continued, but did not leave their threats that if the ransom is not paid, we will offer the stolen data to the public for free.
Irish officials, after testing it, found the vehicle to be genuine, but warned that it ran poorly and slowly. The government said over the weekend that it had made “very steady progress”, thanks in part to a redesigned version of the vehicle, but warned that it would likely take weeks to recover the systems.
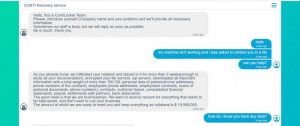
Judging by the information shared by cybersecurity researchers on dark web forums, criminals still continue to demand payment, threatening to publish private data online.
- Complementing health sector regulations such as HIPAA, HIMSS, SKS and JCI; Sustainability should be ensured by establishing an effective Information Security Management System (ISMS) and Personal Data Management System (KVYS).
- An adequately sized cyber security/information security team should be available. At many points, outsource resource use should be considered in the MSSP model.
- Information security awareness of employees should be kept at a certain level with regular trainings.
- Security policies should be updated, vulnerabilities should be closed with timely software fixes, installation management and vulnerability assessments.
- Strong passwords should be used to protect all external ports. Multi-factor authentication must be provided.
- Cyber incidents should always be prepared. For this, regular penetration tests and cyber incident drills should be conducted. In addition, investment should be made in next-generation AIR (Automated Incident Response) technologies that ensure that evidence (including remote workers) is always available at the time of the incident, and that makes incident response fast and effective.
- In remote connection, instead of VPN, which contains many threats, the next generation ZTNA (Zero Trust Network Access – Zero Trust Network Architecture) technology should be used.
- Investing in phishing simulation technologies should be made to protect against phishing attacks.
- CTI (Cyber Threat Intelligence) Service should be activated.
- A stronger and more autonomous cyber security setup should be put into use with DLP, EDR, EPP, XDR, SIEM, SOAR, NAC, IAM, PAM, etc. technologies.
- Critical information should be backed up regularly and an offline backup copy should be kept.
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












