Today, with the increase in remote working and the transition of institutions to remote working or hybrid working, it is more important for organizations to want to manage their network security more effectively.
NAC, which stands for Network Access Control, is the process of restricting unauthorized users and devices from accessing a corporate or private network. NAC ensures that only authenticated users, authorized devices and complying with Security policies can enter the network.
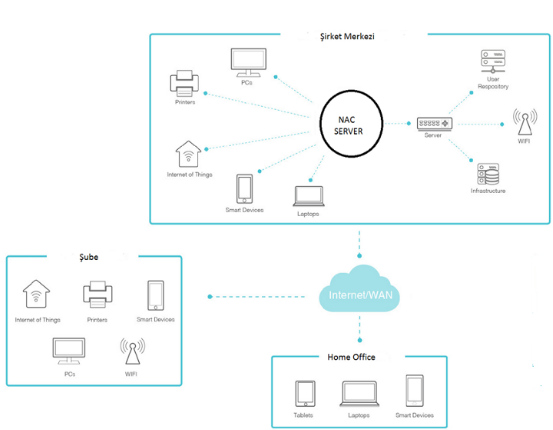
The automated capabilities of a NAC solution are a huge advantage, reducing the time and associated costs associated with authenticating, authorizing users and determining that their devices are compliant.
Aware of the increase in endpoint usage, cybercriminals continue to design and launch sophisticated campaigns that exploit security vulnerabilities in corporate networks.
The area protected by the NAc is intended to prevent attacks that may come from the outer layer of the network, that is, it does not deal with attacks that may come on the WAN and the internet or data that may come from inside. It prevents attacks against the system by countering “zero-day” attacks. In the above image, we see the NAC and the peripherals in the outer layer.
NAC solutions can be configured to detect any unusual or suspicious network activity and respond with immediate action, such as isolating the device from the network to prevent possible spread of the attack.
So what are the advantages of this network access control for us?
- Control of users entering the company network
- Control of access to applications and resources that users intend to access
- Allowing guests to access the network when needed
- Grouping employees by workplace and creating role-based access policies
- Protect against cyber attacks by deploying systems and controls that detect unusual and suspicious activity
- Incident response automation
- Generate reports and insights on enterprise-wide access attempt
In addition to these advantages, when we list the important features that a NAC solution should have, the following items appear:
- Policy Cycle Management: Adjusting policies applied across devices as users across the organization change.
- Profiling and Visibility: Authentication, authorization and profiling. Preventing unauthorized users from accessing
- Guest Network Access: Allowing an organization to manage temporary users, devices, and authenticate through a self-service portal.
- Security Status Audit: Evaluation and classification of security policy compliance according to user, device, operating system and other criteria
- Incident Response: Reduce the number of cyber threats by establishing policies that isolate devices
- Bidirectional Integration: Integration with other security point products and network solutions.
In the Installation Process:
- The control of the network architecture should be examined in detail, and inventories should be made in detail.
- The company’s way of doing business should be well understood and a NAC architecture that would disrupt basic functions should be avoided.
- NAC policies and who has access to what point should be communicated from the General Manager to the lowest employee.
- After the NAC is established, the device inventory determined by the NAC should be compared with the devices in the company’s own inventory, and action should be taken regarding the missing or excess devices.
- NAC policies should be changed according to each newly added device group or new ways of doing business, and employees should be notified.
- Since IT-Network, Software and Security units will be separate in large-scale companies, the unit that writes and controls NAC policies should work closely with all teams. Otherwise, employees who are far from the company’s headquarters may not access system resources from time to time, and there may be problems.
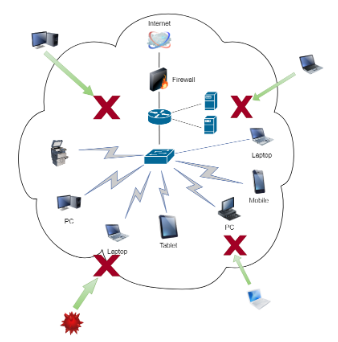
The fact that the network is too wide increases the possibility of risk. Therefore, instead of finding different solutions for each component, it is a more effective approach to evaluate them at a single point and determine policies. As a result, NAC solution for large networks is indispensable and cannot be thrown into the background.
Source:
NAC (Network Access Control — Ağ Erişim Kontrolü) Nedir? | by Ali Tas | Medium
What Is Network Access Control (NAC) ? | Fortinet
Top Network Access Control (NAC) Solutions for 2022 (esecurityplanet.com)
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.
Today, with the increase in remote working and the transition of institutions to remote working or hybrid working, it is more important for organizations to want to manage their network security more effectively.
NAC, which stands for Network Access Control, is the process of restricting unauthorized users and devices from accessing a corporate or private network. NAC ensures that only authenticated users, authorized devices and complying with Security policies can enter the network.

The automated capabilities of a NAC solution are a huge advantage, reducing the time and associated costs associated with authenticating, authorizing users and determining that their devices are compliant.
Aware of the increase in endpoint usage, cybercriminals continue to design and launch sophisticated campaigns that exploit security vulnerabilities in corporate networks.
The area protected by the NAc is intended to prevent attacks that may come from the outer layer of the network, that is, it does not deal with attacks that may come on the WAN and the internet or data that may come from inside. It prevents attacks against the system by countering “zero-day” attacks. In the above image, we see the NAC and the peripherals in the outer layer.
NAC solutions can be configured to detect any unusual or suspicious network activity and respond with immediate action, such as isolating the device from the network to prevent possible spread of the attack.
So what are the advantages of this network access control for us?
- Control of users entering the company network
- Control of access to applications and resources that users intend to access
- Allowing guests to access the network when needed
- Grouping employees by workplace and creating role-based access policies
- Protect against cyber attacks by deploying systems and controls that detect unusual and suspicious activity
- Incident response automation
- Generate reports and insights on enterprise-wide access attempt
In addition to these advantages, when we list the important features that a NAC solution should have, the following items appear:
- Policy Cycle Management: Adjusting policies applied across devices as users across the organization change.
- Profiling and Visibility: Authentication, authorization and profiling. Preventing unauthorized users from accessing
- Guest Network Access: Allowing an organization to manage temporary users, devices, and authenticate through a self-service portal.
- Security Status Audit: Evaluation and classification of security policy compliance according to user, device, operating system and other criteria
- Incident Response: Reduce the number of cyber threats by establishing policies that isolate devices
- Bidirectional Integration: Integration with other security point products and network solutions.
In the Installation Process:
- The control of the network architecture should be examined in detail, and inventories should be made in detail.
- The company’s way of doing business should be well understood and a NAC architecture that would disrupt basic functions should be avoided.
- NAC policies and who has access to what point should be communicated from the General Manager to the lowest employee.
- After the NAC is established, the device inventory determined by the NAC should be compared with the devices in the company’s own inventory, and action should be taken regarding the missing or excess devices.
- NAC policies should be changed according to each newly added device group or new ways of doing business, and employees should be notified.
- Since IT-Network, Software and Security units will be separate in large-scale companies, the unit that writes and controls NAC policies should work closely with all teams. Otherwise, employees who are far from the company’s headquarters may not access system resources from time to time, and there may be problems.

The fact that the network is too wide increases the possibility of risk. Therefore, instead of finding different solutions for each component, it is a more effective approach to evaluate them at a single point and determine policies. As a result, NAC solution for large networks is indispensable and cannot be thrown into the background.
Source:
NAC (Network Access Control — Ağ Erişim Kontrolü) Nedir? | by Ali Tas | Medium
What Is Network Access Control (NAC) ? | Fortinet
Top Network Access Control (NAC) Solutions for 2022 (esecurityplanet.com)
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












