With the May 2019 update by Microsoft Windows, the Windows Sandbox feature was added. Windows Sandbox allows us to create a virtual Windows 10 via Virtualization Technology so that you can test programs and applications that you suspect, do not trust in Windows, where it allows you to work with suspicious files and programs.
The minimum system requirements for Windows Sandbox are as follows;
⦁ Windows 10 Pro or Windows 10 Enterprise operating system.
⦁ Processor with AMD64 or Intel® VT architecture.
⦁ At least 4GB of RAM
⦁ At least 1 GB of free disk space.
To activate the Windows Sandbox feature;
Virtualization technology must be activated on your machine. To check if the virtualization feature is active;
⦁ cmd opens.
⦁ Run by typing “systeminfo.exe” command
⦁ All of the Hyper-V Requirement must be “Yes”.
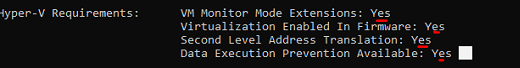
If it is not “Yes”, it is understood that the virtualization technology is not active. To activate it, the “Virtualization Technology” feature must be activated by entering the BIOS section.
After the virtualization technology is activated;
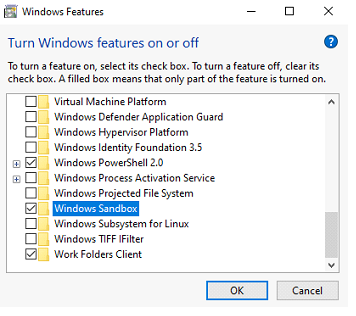
Control panel > Programs > Programs and features > Turn Windows features on or off > Windows Features
In the "Windows Features" window that opens, find the Windows Sandbox feature and ✓
sign is discarded and exit is done by pressing the “OK” button.
After saying “OK” we need to restart our computer to run Sandbox.
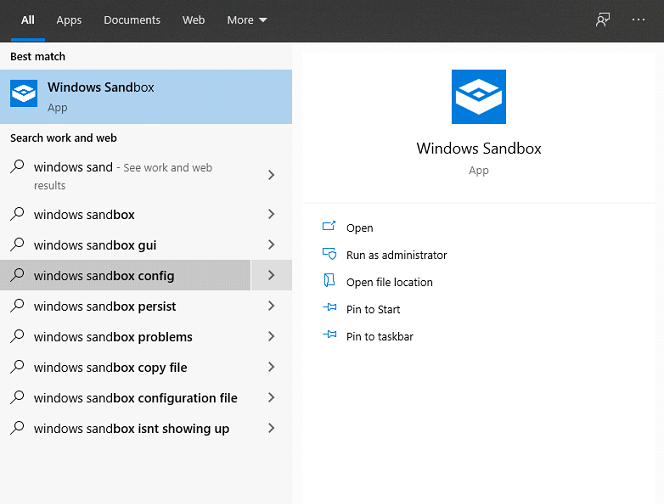
To run it, type "Windows Sandbox" in the search section and click on the result.
Sandbox Keylogger Test
Keylogger, which can also be called spyware or monitoring software, is simply the name given to software that monitors every click you make on the keyboard. The attacker can see what you type on the keyboard and secretly track your movements. This may lead to the theft of personal data.
The keylogger is run on the virtual machine of Windows. In our virtual machine, the keylogger was able to track our keyboard entries, but it did not infect our real machine.
Lessons to learn:
We should not run a suspicious link or file that comes to our e-mail address on our own computer. It can be opened using Windows Sandbox. If the attack is real, we are protected from risk since we do not run it on our own computer. When we close the Sandbox, its contents are completely reset so that we can eliminate it without being affected by the incoming attack.
Source
answers.microsoft.com
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












