Microsoft warned on Tuesday of an actively exploitable zero-day affecting Internet Explorer, which is used to hijack Windows systems by exploiting Office documents.
This vulnerability, numbered CVE-2021-40444 (CVSS score: 8.8), is due to remote code execution in Internet Explorer, currently Microsoft's preferred browser engine for Office files, and MSHTML (which is used to render web content in Office files in-app). aka Trident). Applications affected by the vulnerability are specified as Word, Excel, and PowerPoint documents.
"An attacker can create a malicious ActiveX control for use by a Microsoft Office document that hosts the browser run engine. The attacker would then have to convince the user to open the malicious document by social engineering.
Microsoft's anticipated patch for this zero-day following completion of research is expected to release a security update as part of the release cycle or an out-of-band patch "depending on customer needs" on Tuesdays of every Month.
Meanwhile, Windows has announced that it requires users and organizations to disable all ActiveX controls in Internet Explorer to mitigate or prevent potential attacks.
To Change ActiveX Settings;
In Internet Explorer, select the Tools button, then Internet Options.
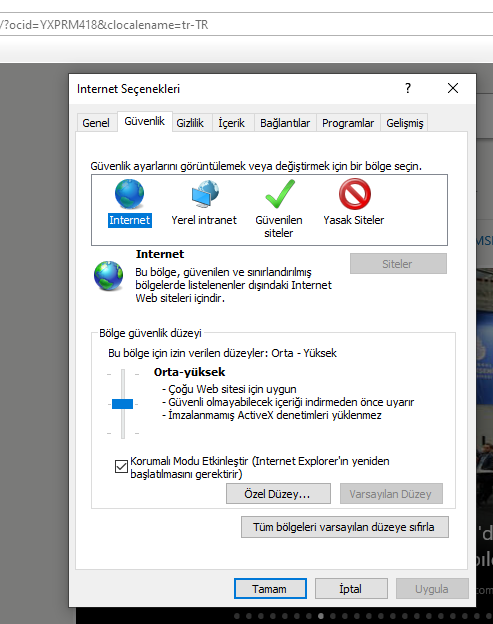
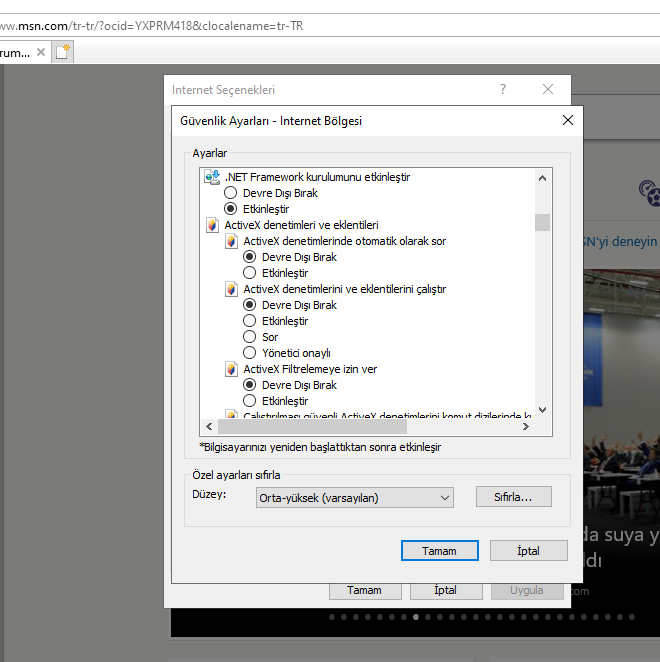
On the Security tab select custom level and under security ActiveX you can disable automatic ActiveX prompts by disabling all Activex plugins.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”TIKLAYIN” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen[/vc_cta][/vc_column][/vc_row]












