Pegasus is spyware developed by Israeli cyber weapons firm NSO Group that can be secretly installed on mobile phones running most versions of iOS and Android. This software is a software developed outside of the traditional hacking methodologies where you just need to answer the incoming call to infect your phone. Pegasus is the software that allows to control all the features of the leaked phone with a remote control.
The work called “Pegasus Project”, created with the coordination of Forbidden Stories and Amnesty International, has been published in the world media by Aristegui Noticias, Daraj, Die Zeit, Direkt 36, Knack, Forbidden Stories, Haaretz, Le Monde, OCCRP, Proceso brought together investigative journalists from PBS Frontline, Radio France, Le Soir, Süddeutsche Zeitung, The Guardian and the Washington Post.
With the software called Pegasus, this team has identified more than 50,000 phone numbers with the names of journalists, politicians, businessmen, human rights activists, lawyers and other dissidents "selected as potential targets" in more than 11 countries since 2016.
The research, which started as a result of the data leak, was carried out and reported by 16 media outlets, including The Washington Post, the Guardian and Le Monde.
It is stated that the leak covered more than 50,000 mobile phone numbers.
According to the news in The Guardian, one of the media organizations participating in the research, among the journalists targeted globally, there are names working in organizations such as CNN, The New York Times, Al Jazeera, Le Monde and Bloomberg.
The result of the research shows that the software is concentrated on a total of 10 countries in the list of states where it is used. These countries; Azerbaijan, Bahrain, Hungary, India, Kazakhstan, Morocco, Rwanda, Mexico Saudi Arabia and the United Arab Emirates.
As a matter of fact, although incidents similar to these claims have been brought to the agenda since 2016, the fact that no significant steps have been taken has brought along the questions, "Did the fact that the company producing the software in question was based in Israel, right of immunity?"
Discussion groups have been opened on this spying case on dark web forums. Hackers in these conversation groups say that the incident was with the support of Israel's National Intelligence Agency 'Mossad' organization and that Mossad has always supported such companies and hacker groups.
Example Comment;
Attack Evidence
19 July 2020 Tamer Almisshal Attack
Tamer Almisshal is a well-known investigative journalist on Al Jazeera's Arabic-language channel, where he broadcasts the program “ما خفي أعظم” (translated as “this is just the tip of the iceberg” or “the hidden is bigger”). ). Almisshal's program includes the involvement of the UAE, Saudi and Bahraini Government in the coup attempt in Qatar in 1996, the Bahraini Government recruiting a former Al Qaeda agent for an assassination program, the Saudi murder of Jamal Khashoggi, and the UAE Royal Family's involvement in the coup attempt. is a journalist who has deciphered the ties between Sheikh Mansour Bin Zayed Al-Nahyan, a powerful member of the public, and UAE businessman BR Shetty's healthcare empire, which collapsed in 2020 due to allegations of fraud and confidential debt disclosure.
Almisshal was worried that his phone might be hacked, so in January 2020 he allowed Citizen Lab researchers to install a VPN app to monitor metadata associated with internet traffic. In this way, he took a precaution of his own.
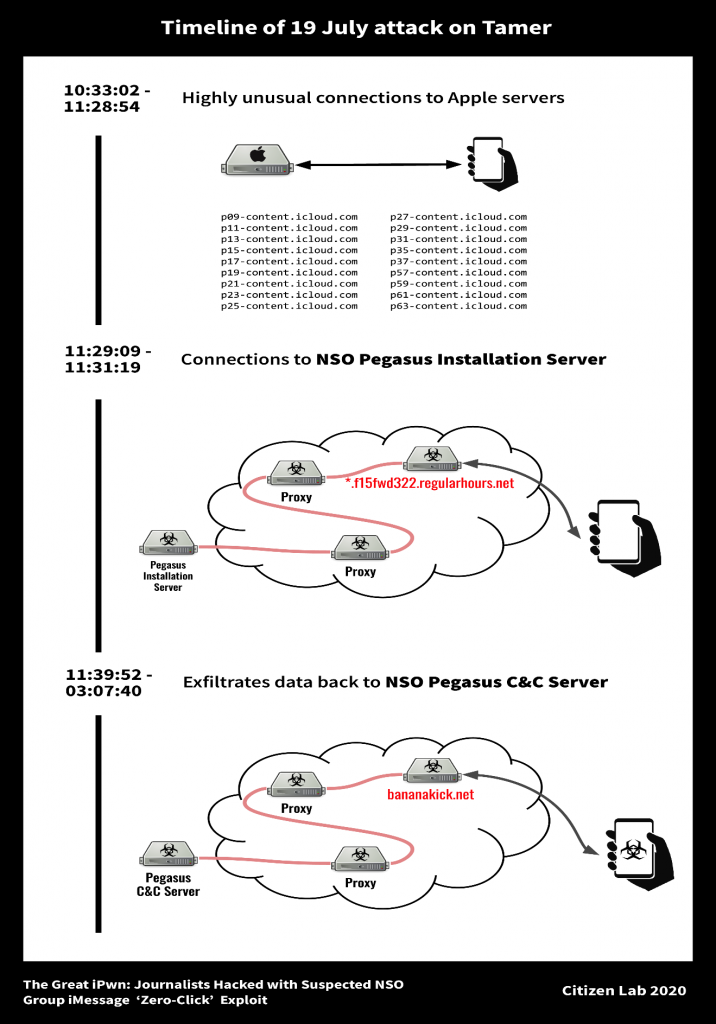
As can be seen in the figure above, it has been determined that Tamer has started to be listened to and followed by mobile forensic analysis methods.
Detection Suggestion
With the Open Source Mobile Verification Toolkit (MVT), you can detect whether your phone is infected or not.
Information about NSO Group's Pegasus spyware is available to detect devices on the same network that have been compromised. This information is published in a repo that is the result of a lot of research done by Amnesty International Security Lab and other partners. This repo and MVT tool are available at the links below.
github.com/AmnestyTech/investigations/tree/master/2021-07-18_nso
Source
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”TIKLAYIN” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen[/vc_cta][/vc_column][/vc_row]












