A phishing attack has been detected by Cyber Watchdog Armorblox that impersonates popular crypto wallet MetaMask to bypass Microsoft 365 defense.
MetaMask is one of the most widely used crypto apps, which allows users to store and exchange cryptocurrencies, interact with the blockchain, and host Apps built on a decentralized network powered by a blockchain distributed ledger. Detected a phishing attack.
By circumventing Microsoft Office 365, Armorblox researchers said in a June 23 blog post that this email attack targeted multiple organizations in the financial industry.
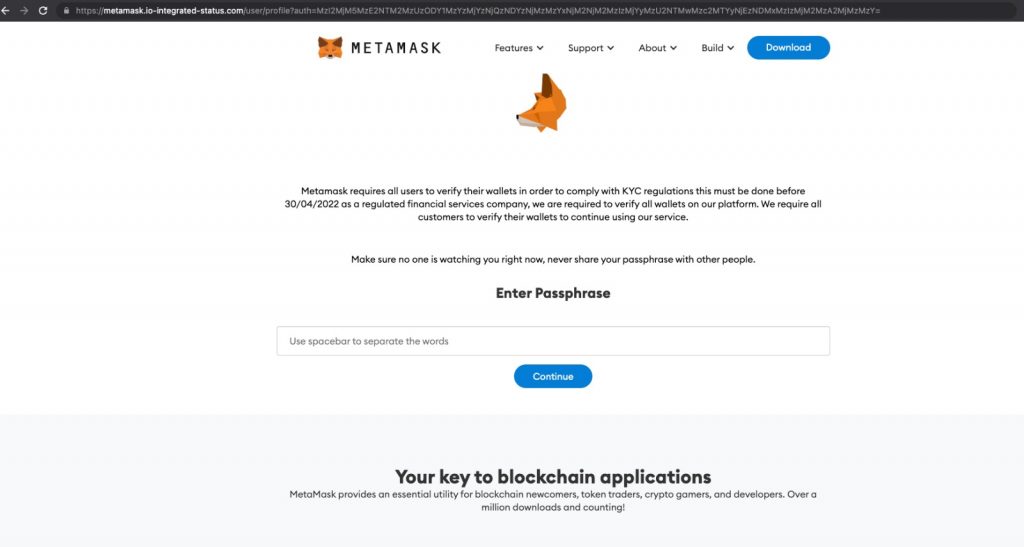
The researchers said the email attack appeared to be a MetaMask verification email. However, when victims clicked on the link, they were redirected to a fake MetaMask verification page. The email body forged a know-your-customer verification request and claimed that non-compliance would result in restricted access to the MetaMask wallet. The email asked the victim to click the “Verify Your Wallet” button to complete the wallet verification, but they were then sent to a fake landing page where unsuspecting victims were tricked into providing their credentials.
“The email body forged a KYC (Know Your Customer) verification request and claimed that non-compliance with regulations would result in restricted access to the MetaMask wallet,” Armorblox said, detailing a classic social engineering tactic that puts pressure on the victim. “Even though the attackers sent this email from an invalid domain, the threat still bypassed Microsoft email security,” he added. “This socially engineered attack impersonated a well-known brand, designed to create a sense of trust in the end user. To get the victim to comply and leak sensitive data, the attackers added language to both the body of the email and the fake landing page expressing a sense of urgency, making it known that time is of the essence.”
 Summary of Techniques Used
Summary of Techniques Used
This email attack used a number of techniques to bypass traditional email security filters and pass unsuspecting victims' eye tests.
Social engineering: The email title, design, and content were intended to instill a sense of trust and urgency in victims. Trust was built by impersonating a well-known brand (MetaMask) and creating a sense of urgency through the language used in both the email and the fake landing page. The context of this attack also benefits from the curiosity effect, a conscious bias that refers to our innate desire to resolve uncertainty and learn more about something.
Brand impersonation: The email contains HTML styles and content disclaimers similar to the MetaMask brand. While MetaMask does not require KYC verification, the colors and branding elements used in both email and landing pages are close enough to endanger the end user.
Guidance and Advice
1. Enhance local email security with additional controls
The email highlighted in this blog has passed the native email security. For better protection and coverage against email attacks (whether it's spear phishing, business email security, or phishing attacks like this one), organizations should augment their built-in email security with layers that take a significantly different approach to threat detection. Gartner's Email Security Market Guide covers new approaches vendors introduce in 2021, and Armorblox highlighted this in their 2022 Email Security Threat Report.
2. Pay attention to social engineering tips
Because we receive a lot of emails from service providers, our brains are trained to execute desired actions quickly. Much easier said than done, but use these emails as rationally and methodically as possible. Have an eye test that includes examining the email, sender name, sender email address, language in the email, and any logical inconsistencies in the email.
3. Review multi-factor authentication and password management
If you haven't already, use these hygiene best practices to minimize the impact of leaking credentials:
- Enable multi-factor authentication (MFA) on all possible work and personal accounts.
- Do not use the same password on multiple sites/accounts.
- Use password management software to store your account passwords.
- https://www.armorblox.com/blog/metamask-crypto-phishing-attack/
- https://www.scmagazine.com/news/email-security/credential-phishing-attack-spoofs-cryptocurrency-app-metamask-targets-financial-industry
- https://www.bleepingcomputer.com/news/security/metamask-phantom-warn-of-flaw-that-could-steal-your-crypto-wallets/
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.













