Cobalt Strike; In its most basic definition, it is a Java-based application that can be used for command and control within the scope of cyber attack simulations. Powershell Empire was developed by Raphael Mudge as a paid alternative to other existing command and control tools such as Metasploit (Meterpreter), PoshC2.
Since its launch in 2012, Cobalt Strike has become a popular platform for red teams and ethical hackers. It is robust and reliable software combined with innovative features such as DNS tunneling, lateral movement tools for privilege escalation, and PowerShell support. This tool has become a desirable option for organizations that want to test their cyber defenses. That all changed in late 2020 with the release of a GitHub repository tool that was like a compiled version of Cobalt Strike. Users claimed that the leaked platform worked similarly, if not identically, to the commercial version, and even circumvented the license check with a fake license. This made the software instantly available and very attractive to cybercriminals.
According to research, even before the leaked version was reported, 66% of ransomware attacks were found to use Cobalt Strike. For a while, the havoc wrought by the Cobalt Strike-like app seemed to have been forgotten.
But in August 2021, researchers at Intezer found a new attack tool, dubbed Vermilion Strike, similar to Cobalt Strike. This tool can emulate Cobalt Strike's ELF binary. EDR etc. They observed that it could not be completely detected and blocked by security tools.
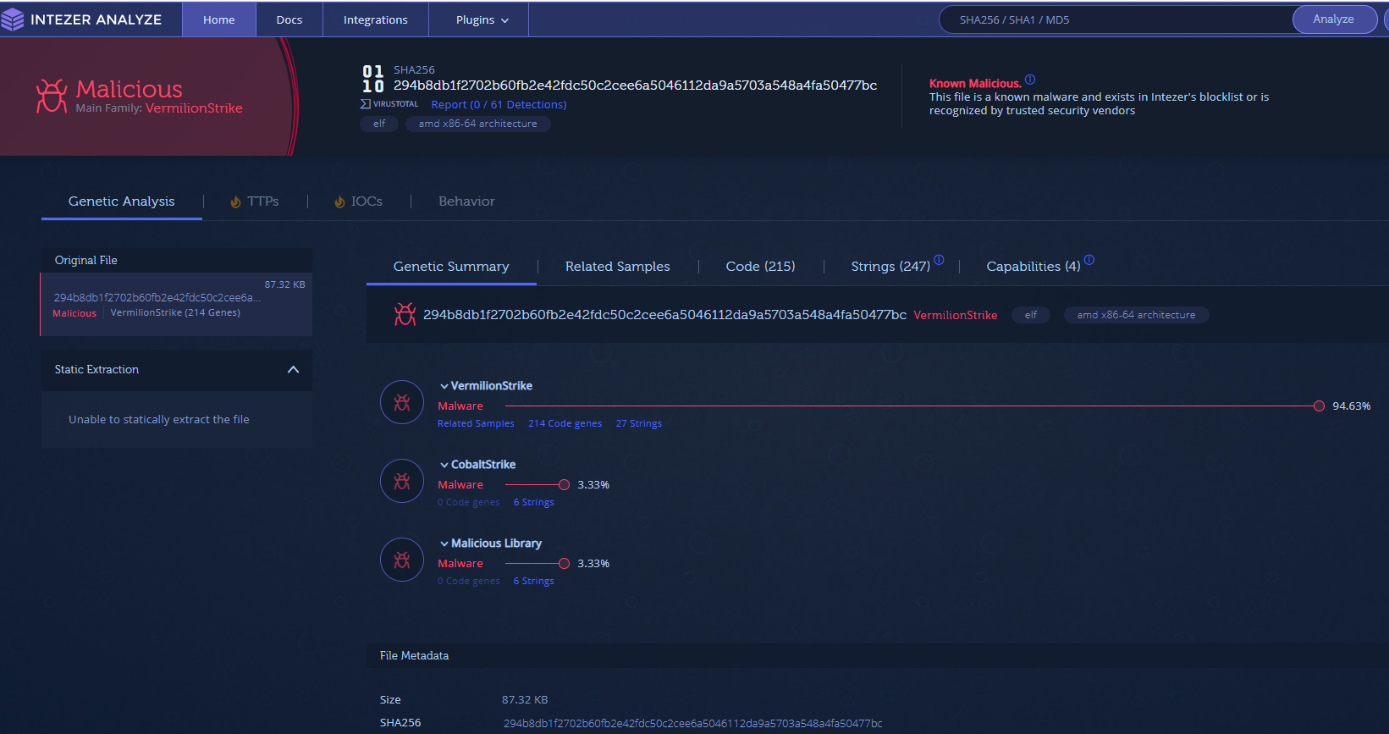
However, experts stated that the configuration format of Vermilion Strike is the same as Cobalt Strike and the tools used to import Cobalt Strike configurations can also be used to reveal the Vermilion Strike configuration.
Not only that, but this particular file shares strings with previously seen Cobalt Strike instances and triggers a set of YARA rules that typically detect hard-coded Cobalt Strike configurations.
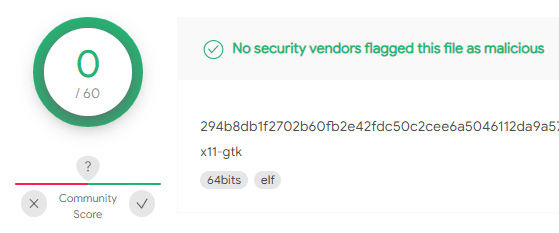
However, experts stated that the configuration format of Vermilion Strike is the same as Cobalt Strike and the tools used to import Cobalt Strike configurations can also be used to reveal the Vermilion Strike configuration.
Vermilion Strike of the detected Cobalt Strike ELF binary is currently completely undetected by anti-malware solutions.
Not only that, but this new Linux malware also features technical overlap, with Windows DLLs constantly showing the same developer.
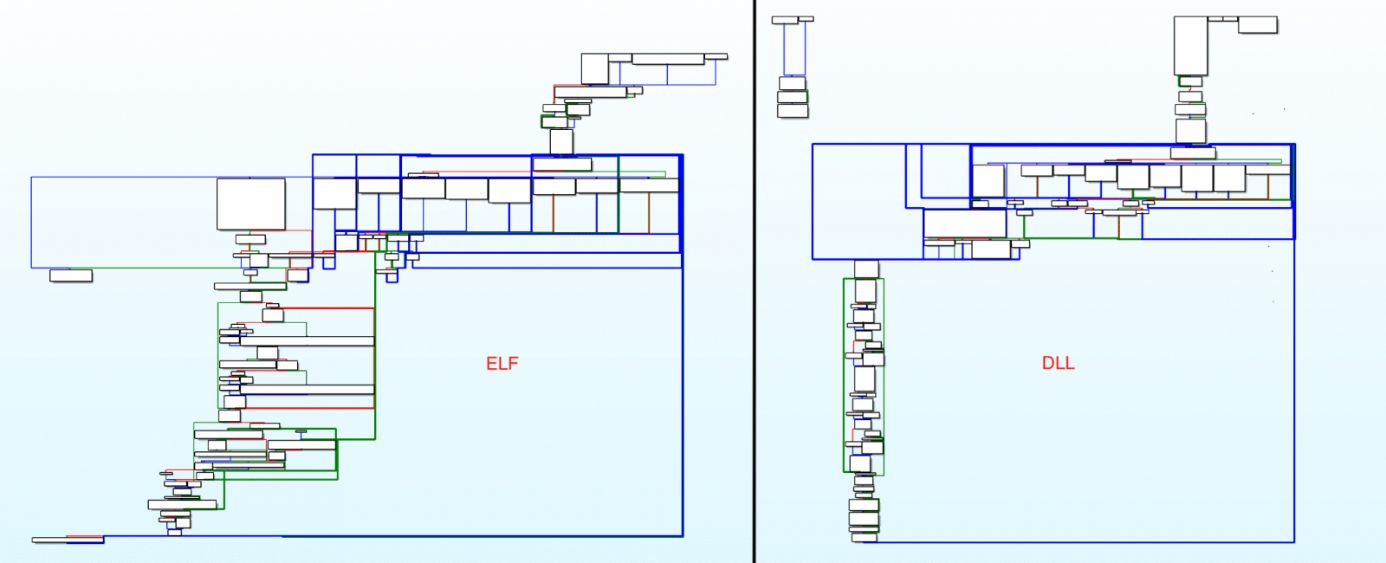
Such malicious acts continue to threaten and are likely to continue. The researchers noted that the continued growth and continued use of Linux servers on the Cloud continue to improve their toolkit so that APTs can navigate and remain unobtrusive in the current environment, claiming to invite other Black Hat hackers.
They also confirmed that this is the first Linux application designed for real attacks. Unfortunately, however, there is no specific information about the original attack vector used by threat actors to target Linux systems.
Conclusion:
In the developing world of cyber security technologies, we see that as natural selection, threat actors will always update and upgrade themselves.
Therefore, in the world of cyber security, our approach must always be a structure that sees the future, anticipates, keeps itself up-to-date, does not trust every security technology 100%, and brings excitement and suspicion together.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”TIKLAYIN” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen[/vc_cta][/vc_column][/vc_row]












