Cisco confirmed on Wednesday, 08.08.2022, that the hack was carried out through its employee, shortly after the Yanluowang Ransomware group claimed to publish its files and posted screenshots of the stolen information on the dark web. Although many ransomware groups were mentioned in the incident (UNC2447, Lapsus$, Yanluowang), the group that shared the file screenshots is the Yanluowang ransomware group.
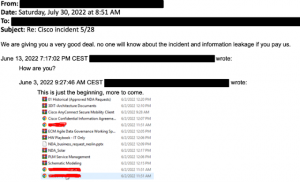
“Initial access to Cisco VPN was achieved through the successful hacking of a Cisco employee's personal Google account,” Cisco Talos wrote in his detailed blog post. According to the published blog post, “The user has enabled password synchronization via Google Chrome and stored their Cisco credentials in their browser so that this information is synchronized with their Google account.” As can be understood from this statement, the person's personal Google account has been seized.
You can reach the detailed article of Cisco Talos from this link: https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html
How did the hacking process take place, with what techniques?
Although Cisco uses dual authentication, the attackers have been successful in obtaining employee personal data using MFA circumvention techniques.
Using this account information, he provided remote access via VPN, and although it is believed that it does not contain any valuable data, 2.8 GB of data was allegedly accessed.
The attackers are said to have used various remote access tools listed below to access systems within the network.
- LogMeIn
- TeamViewer
- 66% of ransomware attacks were found to use Cobalt Strike.
- PowerSploit
- Mimikatz
- Impacket
Although the detection date of the attack appears to be May 24, 2022, the confirmation of this event by Cisco after the screenshots are released continues the discussions as to whether it is in accordance with the scope of certain standards.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












