The human factor is the weakest point of security systems.
A negligence by the users can nullify all the security measures of the system. For this purpose, measures regarding Personnel Security are defined in section 3.5 of the Information and Communication Security Guide in order to inform users about information security, threats and attacks that the systems may be exposed to, to recognize security elements and to train them on safe use.
As you know, institutions have been given a 24-month compliance period as of July 27, 2020, the publication date of the Information and Communication Security Guide. In the first year audits, the preparatory work related to the Institutions audit activities should be started at the end of the 24-month period at the latest. must be carried out.
We wanted to draw your attention to the measures on personnel security numbered days before public institutions and organizations and businesses providing critical infrastructure services complete their compliance work within the scope of information and communication security.
The purpose of this security measure main title is to determine the list of measures and audit questions addressed within the framework of personnel security. The sub-headings of security measures covered under the main heading of "Personnel Safety" are listed below.
 GENERAL SAFETY PRECAUTIONS
GENERAL SAFETY PRECAUTIONS
- Conducting Security Investigations
- Definition of Acceptable Use Rules of Assets
- Defining the Clean Table Clean Screen Policy
- Including Information Security Issues in Contracts
- Implementation of Social Media Usage Policy
- Defining the Disciplinary Process for an Information Security Breach Incident
- Defining Roles, Responsibilities and Minimum Competencies
- Termination or Change of Employment Responsibilities
- Notification of Confidentiality Requirements to Staff
The control method in the measures is interview and review.
3.5.1.1 Conducting Security Investigations
During the recruitment phase, ensuring the accuracy of academic information and past work experience for all candidate personnel, taking into account legal regulations and job requirements.
It is checking the validity of the references and the certificates owned and making a criminal record inquiry.
Examples of Questions to be Asked During the Audit;
- How is the validity of the academic information and certificates declared by the personnel applying for the job checked?
- Are criminal records, past work experiences and related references checked within the scope of verification controls?
- How and where are the evaluation results for validation checks kept?
3.5.1.2 Definition of Acceptable Use Rules of Assets
Determining an acceptable use policy of corporate assets
It is the commitment of the institution personnel and contractors to comply with these rules.
Examples of Questions to be Asked During the Audit;
- Has an acceptable use policy of assets been established?
- Has the acceptable use policy of assets been communicated to institution personnel and contractors?
- Are corporate personnel and contractors committed to complying with the acceptable use policy of assets?
3.5.1.3 Defining the Clean Table Clean Screen Policy
It is the definition and implementation of a clean desk clean screen policy covering physical media, portable information/data storage media and other information processing facilities.
Examples of Questions to be Asked During the Audit;
- Has a clean desk clean screen policy been defined that covers physical media, portable information/data storage media and other information processing facilities?
- How is the clean desk clean screen policy communicated to staff and contractors?
- Is the process to be operated in case of violation of the clean table clean screen policy defined?
3.5.1.4 Including Information Security Issues in Contracts
Information security responsibilities should be specified in the contracts made with personnel and contractors before they are provided with access to the institution's assets.
Examples of Questions to be Asked During the Audit;
- Are information security issues included in the content of contracts made with newly recruited personnel and contractors?
- Is it regularly checked that the requirements related to information security are adequately addressed within the scope of the contract content?
3.5.1.5 Implementation of Social Media Usage Policy
Creating a social media usage policy
In this context, it is ensured that the personnel do not share confidential data and communication over social media.
Examples of Questions to be Asked During the Audit;
- Has a social media usage policy been established?
- What topics are covered in the content of the social media usage policy?
- How is it ensured that the confidential data is not shared by the personnel on social media?
3.5.1.6 Definition of Disciplinary Process for Information Security Breach Incident
In order to manage information security breach incidents, relevant laws, employment contracts, etc. It is the definition and implementation of a disciplinary process, taking into account the elements.
Examples of Questions to be Asked During the Audit;
- Relevant laws, employment contracts, etc. for the personnel/contractor who committed the information security breach. Is there a disciplinary process established by taking these factors into account?
3.5.1.7 Identification of Roles, Responsibilities and Minimum Competencies
Considering the definition and requirements of the job performed by the personnel of the institution, the information security role, responsibilities and minimum competencies that the relevant personnel must have within the institution are defined and put into writing.
Examples of Questions to be Asked During the Audit;
- Considering the definition and requirements of the job performed by the personnel of the institution, are the information security roles, responsibilities and minimum competencies that the personnel must have within the institution defined?
3.5.1.8 Termination or Change of Employment Responsibilities
New information security responsibilities and duties to personnel/contractor whose employment responsibilities have changed; The personnel/contractor whose employment is terminated should be informed about the information security responsibilities that will continue after the termination of employment.
Examples of Questions to be Asked During the Audit;
- Are the provisions that will be valid after the termination of employment included in the personnel and contractor contracts?
- How are the information security responsibilities to be complied with notified to the relevant personnel/contractor after the termination of employment or the change of employment conditions?
3.5.1.9 Notification of Confidentiality Requirements to Staff
Taking into account the information security requirements of the institution, documents such as policies, procedures and instructions that the personnel or contractors must comply with are communicated to the relevant personnel/contractor.
The content of the relevant documents is to be updated in case of changes in information security requirements.
Examples of Questions to be Asked During the Audit;
- Have the information security policies, procedures and instructions that the personnel or contractors must comply with have been defined and communicated?
- Do the relevant documents meet the information security requirements of the institution?
- Are documents updated in case of any change in information security requirements?
EDUCATION AND AWARENESS ACTIVITIES
- Giving Awareness Trainings
- Providing Trainings on Detection and Reporting of Incidents
- Performing Talent Needs Analysis
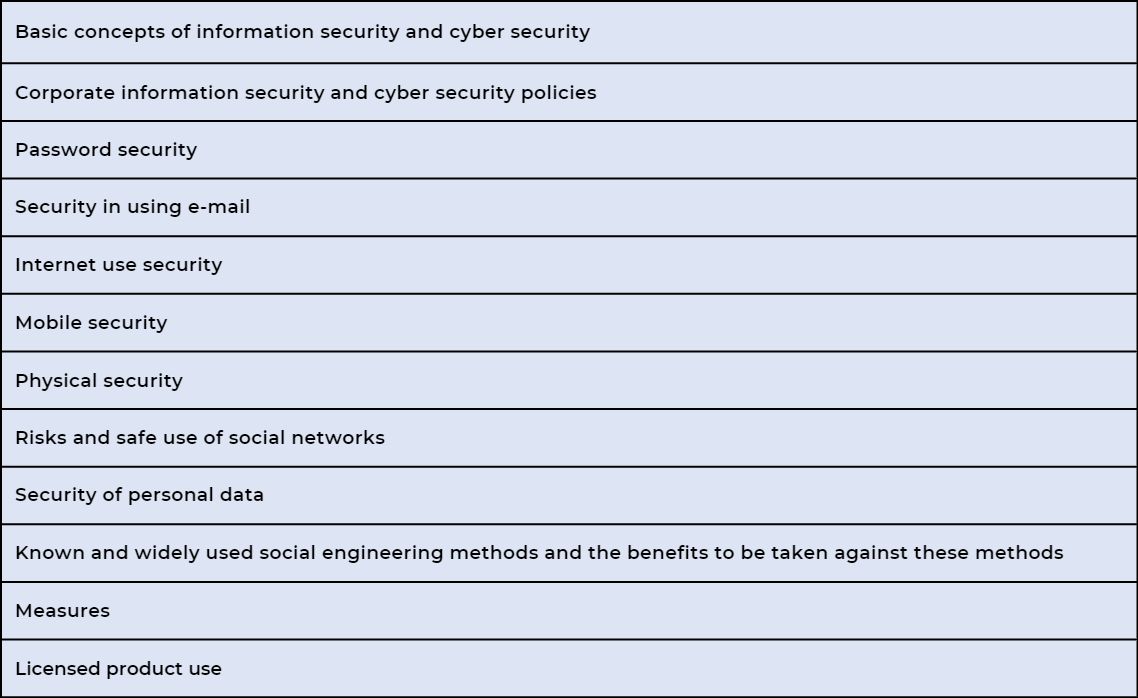
3.5.2.1 Providing Awareness Trainings
To all institution personnel at regular intervals;
It is very important to provide information security and cyber security awareness trainings in a way to include basic and current issues such as the ones mentioned in the table above.
Measurements for the effectiveness of awareness training (pre- and post-training written exam, social engineering attacks, etc.) should be made and actions should be planned in line with the measurement result.
Examples of Questions to be Asked During the Audit;
- Are information security and cyber security awareness trainings given to the personnel of the institution?
- What topics are covered in the training content?
- Is the training content updated periodically?
- How is the effectiveness of training evaluated?
3.5.2.2 Providing Trainings for the Detection and Reporting of Incidents
Information security and SOME personnel should be trained on cyber incident or information security breach incident detection and reporting.
Examples of Questions to be Asked During the Audit;
- Is information security and SOME personnel provided with training on how to detect and report a cyber incident or information security breach incident?
- What topics are covered in the training provided?
3.5.2.3 Performing Talent Needs Analysis
Talent needs analysis should be done for personnel working in the field of information security and cyber security.
In line with the outputs of talent needs analysis, a training roadmap should be drawn up and put into practice.
Examples of Questions to be Asked During the Audit;
- Are talent needs analyzes conducted for personnel working in the field of information security and cyber security?
- Is a training roadmap prepared for the personnel, taking into account the analysis results?
- Are regular trainings given to the employees of the institution in line with the training roadmap?
SUPPLIER RELATIONS SECURITY
Supplier Relations Security measures within the scope of personnel security in the Guide;
- Identification of Information Security Policy in Supplier Relations,
- Confidentiality Commitment in Demo and Proof of Concept Studies,
- Addressing Information Security in Supplier Contracts,
- Supply Chain Security,
- Determination of Acceptance Criteria,
- Determination of Communication Methods,
- Management of Product/Service Changes Supplied by the Contractor,
- Clarification of Main Contractor and Subcontractor Responsibilities,
- Monitoring of Supplier Services,
- Establishing the Supply Chain Monitoring Process is explained under headings.
Definition of Information Security Policy in Supplier Relations
Definition of Information Security Policy in Supply Relations with measure number 3.5.3.1 is briefly defined as "A policy should be defined and implemented in order to ensure the protection of corporate assets accessed by suppliers, to reduce the risks related to suppliers' access to the organization's information assets, and to meet information security requirements". .
In the Guide, this measure; Interview and review methods have been proposed for auditing, and also,
- “Is a policy defined in order to meet information security requirements in supplier relations?
- What aspects does the information security policy include? Suggested audit questions.
Confidentiality Commitment in Demo and Proof of Concept Studies
Confidentiality Commitment measure in Demo and Proof of Concept Studies with measure number 3.5.3.2; Confidentiality agreement containing the responsibilities of the third party should be prepared and signed in demo and proof-of-concept (PoC) studies conducted with third parties, taking into account the needs of public institutions and organizations and businesses providing critical infrastructure services. It can be defined as the periodic review of the content of the relevant undertaking.
In the Guidelines, interview and review methods have been proposed for the control of this measure, and also,
- “In demo and proof-of-concept (PoC) studies with third parties, is a confidentiality agreement signed by third parties?
- Is the undertaking prepared in accordance with the information security requirements of the institution?” Suggested audit questions.
Addressing Information Security in Supplier Contracts
Handling of Information Security in Supplier Contracts with measure 3.5.3.3; It can be defined as adding the information security requirements to the contracts to be signed with each of the suppliers that can access, operate, store, transmit or provide the information technology infrastructure components of the institution, which can be accessed by public institutions and organizations and businesses providing critical infrastructure services.
In the Guidelines, interview and review methods have been proposed for the control of this measure, and also,
- “Are information security requirements added to contracts with suppliers?
- What are the information security requirements in the contracts?” audit questions are suggested.
Supply Chain Security
The Supply Chain Security Measure with measure number 3.5.3.4 is briefly “The risks associated with the supply chain for the supplied information and communication technologies products and services should be taken into account in the contracts made with the contractors and the relevant security requirements should be added to the contract contents. In this context, a written document must be obtained from the persons and/or organizations to work with, stating that supply chain security will be ensured.
In the Guidelines, interview and review methods have been proposed for the control of this measure, and also,
- An audit question in the style of “Do the contracts with the contractors include provisions for supply chain security?” has been suggested.
Determination of Acceptance Criteria
Determination of Acceptance Criteria with measure 3.5.3.5; It is defined by specifying the requirement as “In order to verify that the supplied product has been delivered within the desired safety criteria, acceptance criteria must be determined, monitoring and verification methods must be defined and agreed with the contractor”.
In the Guidelines, interview and review methods have been proposed for the control of this measure, and also,
- “Are the acceptance criteria for the product to be supplied determined?
- What method is followed in order to verify that the supplied product has been delivered in accordance with the desired safety criteria?” audit questions are suggested.
Determination of Communication Methods
The measure of Determination of Communication Methods with measure number 3.5.3.6 should briefly be defined as “Who to contact, how to contact, which rules will be valid, for informational purposes throughout the supply process including the warranty process or any possible abnormal situation, and it should be defined with the contractor and the contractor. should be agreed upon”.
Interview and review methods have been proposed for the supervision of this measure specified in the Guidelines.
- “Is it defined how to contact and which rules will apply about any possible abnormal situation throughout the supply process including the warranty process?” audit question is suggested.
Management of Contractor-Supplied Product/Service Changes
Management of Changes in the Product/Service Provided by the Contractor with measure number 3.5.3.7. Taking this assessment into account, the requirements should be reflected in the contract with the contractor, and how such change situations will be handled should be clearly defined.
Interview and review methods have been proposed for the supervision of this measure specified in the Guidelines.
- “How is the management of the changes experienced within the scope of the service and product supply process provided by the contractor?
- Are there any requirements regarding the management of product/service changes in the contracts made with the contractor? audit questions are suggested.
Clarification of Main Contractor and Subcontractor Responsibilities
Measure 3.5.3.8 Clarification of Main Contractor and Subcontractor Responsibilities is stated in the Guide “The main contractor is required to provide the products and services supplied during the procurement period. if it uses a subcontractor; The main contractor's and subcontractor roles and responsibilities are documented, and the commitment that the subcontractor will comply with the information security requirements throughout the procurement process should be taken from the main contractor.
Interview and review methods have been proposed for the supervision of this measure specified in the Guidelines.
- “In case the main contractor uses subcontractors during the procurement; Is the commitment taken from the main contractor, where the roles and responsibilities of all relevant parties are defined and the subcontractor guarantees that the information security requirements will be fulfilled?” audit questions are suggested.
Monitoring of Supplier Services
Monitoring of Supplier Services with measure 3.5.3.9 can be defined as the periodic review and documentation of suppliers in order to ensure that information security requirements are met.
Interview and review methods have been proposed for the supervision of this measure specified in the Guidelines.
- “Are supplier services regularly reviewed to ensure that information security requirements are met?” audit question is suggested.
Establishing the Supply Chain Monitoring Process
Establishment of Supply Chain Monitoring Process with measure number 3.5.3.10 is in the Guide "In order to guarantee compliance with the security requirements by the contractor; Throughout the supply chain, traceability of the status of critical components for the service/product supplied should be ensured.” defined as.
Interview and review methods have been proposed for the supervision of this measure specified in the Guidelines.
- “Can the status of critical components for the service/product supplied be monitored throughout the supply chain?” audit question is suggested.
You can find the entire guide here: https://cbddo.gov.tr/SharedFolderServer/Genel/File/bg_rehber.pdf
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]