Information security processes are an important issue in today's digital world that enables businesses to identify and implement many security controls they need to protect their digital assets. Among these security controls, data encryption and key management have a very important place. At this point, HSM (Hardware Security Module) devices play an important role in ensuring the security of digital assets and emerge as an element that must be included in the information security strategies of businesses.
In this article, we will discuss the importance of HSM devices in information security processes and the contribution they provide to information security processes, together with their strong encryption and key management features. In addition, we will examine the issues regarding these devices in our legal legislation and talk about the features that HSM devices must have from the perspective of the CB DDO Information and Communication Security Guide.
As it is known, HSM devices can be used effectively and securely in many information security processes such as data encryption, key management, certificate management, virtual private network (VPN) security and data integrity control. The cryptographic security features provided by HSM devices in these processes are of critical importance for the protection of digital assets. Because the moment when we are weakest is when a process we think is safe is actually not safe enough.
In this article, you will find information that will provide significant benefits for businesses and security experts looking for a suitable HSM solution for the implementation of information security processes. Let's start by talking about the sectors where HSM devices are widely used, their basic functions and the data they protect.
HSMs are widely used in many industries as they are devices used for secure data processing and cryptographic key management.
Service Providers: HSM devices can be used very effectively for large numbers of invoices and e-seal transactions, especially in institutions and organizations that serve a large number of subscribers, such as energy distribution companies or telecommunication companies. With the high processing capacity of HSM devices, many invoices or documents can be sealed or signed at the same time.
Financial Services: Banks, financial institutions, payment processors and other financial service providers can use HSMs to protect critical financial data. HSMs are also used in transactions that require many security measures, such as credit card transactions, ATM transactions, authentication and database encryption.
Public and Government Agencies: Government agencies, military agencies, and other public organizations use HSMs to protect sensitive data. For example, HSMs can be used in areas such as authentication, digital signatures, and e-government applications.
Healthcare: The healthcare industry uses HSMs to secure hospital systems, electronic health records, prescriptions, and medical data. Cryptographic operations are carried out through HSMs for the confidentiality and integrity of patient data.
Retail and E-commerce: Retail industry and e-commerce companies can use HSMs to ensure the security of credit card transactions and customer information. Payment gateways, POS (Point of Sale) systems and online payment transactions are secured through HSMs.
Telecommunications: The telecommunications sector can use HSMs in areas such as user authentication, encryption, virtual private networks (VPN). Operations such as security of mobile communication networks, SIM cards and secure messaging are supported by HSMs.
Although HSM devices perform many important functions in information security processes, some of their basic functions are as follows;
Key Management: HSMs handle secure key creation, storage, use and destruction. Cryptographic keys are generated, stored and managed securely within the HSM. This function protects keys from unauthorized access and ensures the security of key management processes.
Cryptographic Operations: HSMs provide a secure environment for performing cryptographic operations. For example, cryptographic operations such as symmetric and asymmetric encryption, digital signature and key exchange operations can be performed within the HSM.
Secure Data Storage: HSMs can be used for secure storage of sensitive data. For example, confidential data such as user passwords, passwords, authentication credentials can be protected within HSM.
Authentication and Authentication: HSMs can be used for operations such as user authentication, access control, and authorization. This functionality supports ensuring secure login, authentication and authorization processes.
Timestamp: HSMs can provide secure timestamp services. Particularly in situations where date and time information must be securely recorded and used, this function can be used to verify and document a specific time.
Remote Access and Secure Communication: HSMs create secure communication channels and make remote access secure by using secure network protocols and encryption methods for secure remote access and secure communication.
HSM devices can be used to protect a wide variety of types of data. Common types of data that can be protected by a general-purpose HSM device include:
Passwords and Credentials: HSM devices can be used to secure sensitive confidential data such as user passwords, passwords, and authentication credentials. Such data is securely stored and processed within HSM.
Cryptographic Keys: Private keys, symmetric and asymmetric keys, digital certificates, and other keys used in cryptographic algorithms can be protected within the HSM. Keys are stored securely in HSM, and key creation and use are handled by HSM.
Cryptographic Signatures: HSMs can be used to create and verify digital signatures. Digital signatures are used in scenarios such as ensuring data integrity, authentication and secure communication, and HSMs ensure the security of these transactions.
Financial Data: HSMs are used by financial institutions to protect sensitive financial data such as credit card data, PIN (Personal Identification Number) information, financial transactions and payment data.
Health Data: HSMs can be used in the healthcare industry to secure electronic health records, medical images, and other sensitive health data. Protection of this data is very important in terms of meeting confidentiality and integrity requirements.
Licenses and Certificates: HSMs can be used to securely store and use important licenses and certificates, such as software licenses, digital certificates, license keys, etc.
While performing the functions mentioned above, HSM devices must provide cryptography-specific security measures (tamper detection, red-black separation, etc.). The security and compliance of HSM devices are generally checked and/or certified based on standards and audit processes. Some commonly used methods are:
International Standards: HSM devices are generally designed and manufactured in accordance with internationally accepted standards. These standards include standards such as FIPS 140-2/3 (Federal Information Processing Standard), Common Criteria (ISO/IEC 15408), PCI DSS (Payment Card Industry Data Security Standard), ISO/IEC 19790-24759. FIPS 140-2/3 (Federal Information Processing Standard), Common Criteria (ISO/IEC 15408), PCI DSS (Payment Card Industry Data Security Standard), ISO/IEC 19790-24759.
Security Assessment and Certifications: Independent security assessment organizations examine HSM devices, evaluate their security and issue compliance certificates. For example, documentation such as the Common Criteria certification or the FIPS 140-2/3 (CMVP,CAVP) certification indicates that the HSM device complies with security standards. You can obtain information about the security of the HSM device by checking these certificates and security assessment reports.
Security Reviews and Audits: Security reviews and audits can be performed to detect security vulnerabilities and check compliance of the HSM device. These reviews are usually carried out by independent security experts or audit firms. If vulnerabilities, vulnerabilities, or incompatibilities are detected, corrective measures may need to be taken to address these issues.
Corporate Policies and Standards: The security policies and standards determined by your organization are also important for the security and compliance of the HSM device. These policies and standards include specific rules on issues such as HSM device usage, configuration, access controls, and security policies. You can use internal audit processes to verify that the HSM device complies with these policies and standards.
Management Controls and Monitoring: The security of the HSM device must be constantly monitored through management controls and monitoring processes. This includes ensuring that the HSM device is configured correctly, updates are applied regularly, access controls are maintained, and its events are monitored. Regular audits, monitoring and updating processes should be implemented to ensure HSM device security and compliance.
Our Legal Legislation on Cryptography, Information and Communication Security Guide
Measures deemed appropriate to be taken in order to facilitate access to information, reduce and neutralize the security risks brought about by the digitalization of infrastructures and widespread use of information management systems, and to ensure the security of critical types of data that may threaten national security or lead to disruption of public order, especially when their confidentiality, integrity or accessibility is compromised. It has been determined in general terms by the Presidential Circular No. 2019/12. As a result of this Circular, theInformation and Communication Security Guide, which includes different security levels to be implemented in public institutions and organizations and businesses providing critical infrastructure services, within the framework of national and international standards and information security criteria, has been prepared by relevant public institutions and organizations under the coordination of the Presidency Digital Transformation Office. It was prepared with the contributions of organizations and approved on 24.07.2020.
Local and National Crypto Systems
There are many articles in both the Circular No. 2019/12 and the Information and Communication Security Guide regarding the use of cryptographic systems and the security features they must have. For example, in the Circular, the risks that foreign crypto systems may have were taken into consideration, and in its 11th article, a clear will was expressed to encourage the development of domestic and national crypto systems and to carry out confidential communications of institutions through these systems.
In addition, with this basis taken from the Circular, the use of local and national crypto systems is emphasized in the Crypto Applications Security (4.4) Section of the Information and Communication Security Guide.
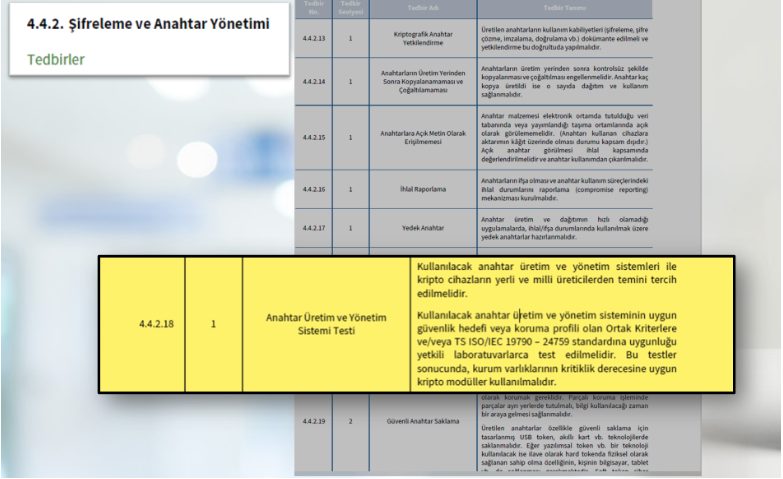
At this point, "...supply should be preferred." Although the statement is sometimes interpreted as not being a definitive provision, it is very clearly stated in the Guide in which cases domestic and national products should be preferred. If there is a local and national product that meets the security requirements, choosing this product is actually a legal requirement.
While many frameworks, standards or regulations implemented for information security today emphasize the use of internationally accepted cryptographic mechanisms and a secure key management system from a general perspective, details about these systems are not entered, with one exception. This exception is the Information and Communication Security Guide.
When we examine the Information and Communication Security Guide from the perspective of crypto systems, we see that a total of 59 measures directly or indirectly point to crypto systems. While 25 of these measures require the use of crypto systems for the protection of assets and information security, 29 measures define the security features that these crypto systems must have. 5 measures have been defined for both crypto system use and crypto system security features.
In addition, the Regulation on the Procedures and Principles of Coded or Encrypted Communication within the Electronic Communication Service of Public Institutions and Organizations and Real and Legal Persons published by BTK states that "national crypto devices designed and produced in Turkey in coded or encrypted communication systems used by public institutions and organizations" It is stated that its use is essential.
As can be seen, special importance is given in our national legislation to the use of domestic and national devices, if possible, in crypto systems where critical data is processed.
In light of the issues we mentioned in our article, no matter which sector we operate in, it may be a legal obligation to use an HSM device, and in this case, we will need to take the following factors into consideration when choosing the right HSM device.
Security Standards: It is very important that the HSM device complies with security standards. Security standards include international certifications such as FIPS 140-2/3, Common Criteria (ISO/IEC 15408), PCI-DSS/PCI-HSM 3/4, ISO/IEC 19790-24759. These certifications confirm that the HSM complies with a certain level of security and standards.
Capabilities and Features: It is important to determine the features that the HSM should provide to suit your needs. These include factors such as key storage capacity, transaction speed, supported encryption algorithms, ability to generate random numbers, multi-user support and integration capabilities. The HSM should have features that suit your usage scenarios.
Use of Domestic and National Devices: It would not be a correct approach to consider the use of local and national devices only as an effort to develop national technology. When we look at it from a security perspective, the systems that foreign countries will first focus on in their espionage activities will naturally be crypto systems where confidential data is processed. We should never forget that we cannot guarantee that there is no backdoor in a foreign device whose design we do not know. In addition, local and national crypto devices will eliminate dependence on foreign countries in these systems that are intolerant to interruptions and will ensure control of strategically important data.
Performance: The performance of the HSM is important for its ability to support high-speed transactions and operate with low latencies. An HSM with sufficient performance should be chosen according to your workload.
Compatibility: The HSM device must be compatible with the application, platform or system you choose. In particular, compatibility with systems that need to be integrated should be tested and verified.
Scalability: It is important that the HSM device can adapt as your needs grow. To meet increasing demands in the future (such as switching to post quantum algorithms), a scalable HSM device should be chosen.
User Experience: Factors such as the HSM's ease of use, management tools, and user interface should also be considered. Users must be able to manage and use the HSM effectively.
Provider and Support: It is important that the HSM provider is reliable and has a strong reputation. Factors such as the provider's ability to provide long-term support and maintenance services, its ability to solve your problems as soon as possible when needed, and its ability to provide updates should be evaluated.
Cost: The cost of the HSM device should match your budget. However, you should be careful to choose not just an option that is lower in cost, but one that has the features and safety standards that best suit your needs.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]












