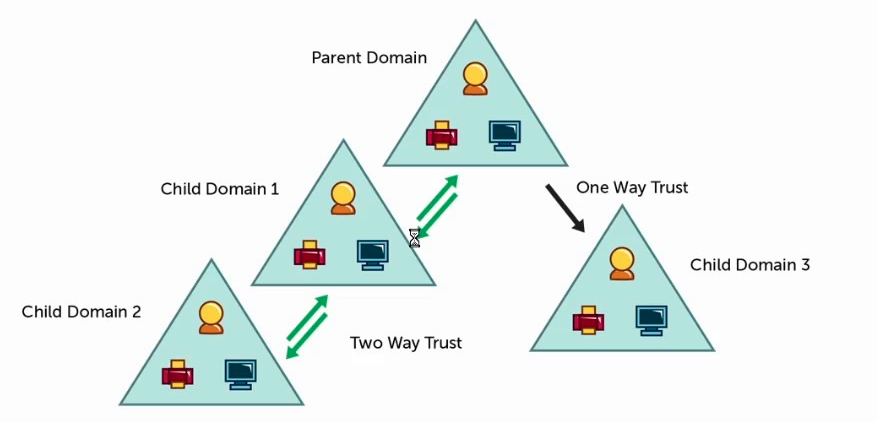
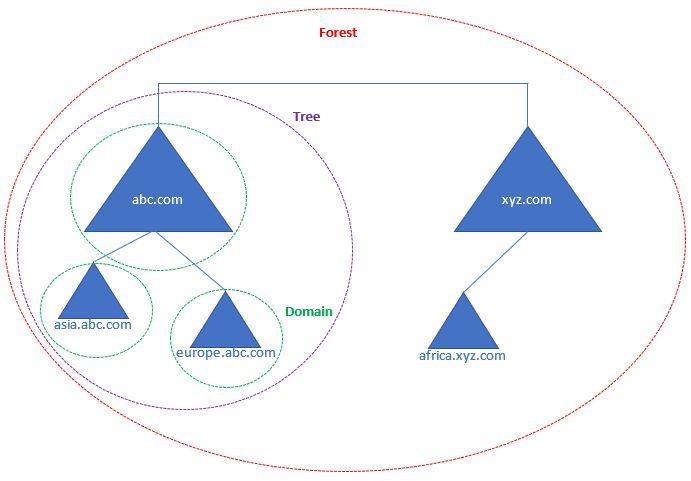
Also known as a set of computers sharing the same database. Each Domain has a unique name and the Domain name must consist of at least two parts, not Turkish characters and must be unique. The first established domain is the root domain, and each domain that continues just below it in the form of a tree structure is named Child domain. However, when you add a new domain under the child domain, it can now qualify as Parent domain when compared to the domain added later. A tree structure with more than one domain structure under the same name is called Tree. This structure is Parent and Child consists of domains.
Aynı veritabanını paylaşan bilgisayarlar bütünü olarak da bilinmektedir. Her bir Domain benzersiz bir isme sahiptir ve Domain adı en az iki kısımdan oluşmalıdır, Türkçe karakter olmamalı ve benzersiz olmalıdır. İlk kurulan domain kök domaindir ve hemen altına ağaç yapısı şeklinde devam eden her domain Child domain olarak adlandırılır. Ancak child domain altına yeni bir domain eklediğinizde artık kendisi de sonra eklenen domain ile karşılaştırıldığında Parent domain olarak nitelendirilebilir. Aynı isim altında birden fazla domain yapısının olduğu ağaç yapısına Tree denir. Bu yapı Parent ve Child domainlerden oluşur.
Multiple Tree to the structure Forest is called. Forest is the outermost layer in the logical structure.
- Enterprise Admin: Located in the first established domain. He is the most authoritative.
- Global Catalog: Contains all DC information and is the first DC global catalog It is known as .
- Forest Root: It is the domain in the first established Forest structure.
Organizational Unit (OU): These are the units that allow to organize the objects in the domain. User accounts, group accounts, computer accounts, printers, shared folders are contained and organized within this unit. Such an arrangement also simplifies the authorization phase. Thus, the edits you make will affect only the associated unit, not all users under the “Users” folder. In addition, thanks to such an arrangement, personal authorizations can be made within the units.
Authorizations on Active Directory
Domain Admin within a domain cannot interfere with other domains. Enterprise Admin is the only one who can interfere with all domains . If hackers took over a Domain Admin account during the infiltration, it means that they can only operate on the associated domain and their authority remains only in that domain. If wants to manage the whole forest structure and also wants to expand its privileges, it must succeed in entering the Enterprise Admins group.
Important Ways to Protect Your Organization Against Cyber Threats and Attacks
- Identity groups (distribution lists, security groups, Microsoft 365 groups) in on-premises.
- Active Directory and cloud environments. Microsoft 365 tools (like SharePoint and Yammer).
- Channels on business communication platforms such as Microsoft Teams.
Groups are indispensable to the functioning of an organization. Distribution lists and channels form the network in an organization, while security groups protect assets and resources from unauthorized access. Yet they are vulnerable to social engineering threats and attacks.
Attack methods for distribution lists have evolved. Officially, threats were largely content-centric (where the email contained a malicious link or attachment). Today, research shows that almost 90% of email attacks manipulate the sender identity to trick recipients and launch social engineering attacks.
What Does the Zero Trust Security Model for Groups in Active Directory, Azure AD, and Microsoft 365 Mean?
Solution methods for distribution groups are considered simple.
- Authenticate, then filter. This is about disallowing delivery of messages unless they come from a sender who can be authenticated and has explicit permission to deliver messages to this group.
How to implement Zero Trust Security via GroupID?
- An effective way to implement a zero trust security model in your identity management environments (Active Directory, Azure AD, and Office 365) is to integrate GroupID by Imanami into your IT infrastructure.
GroupID offers a convenient and powerful approach to apply zero trust security to distribution lists and security groups, thus preventing identity-based attacks and hackers.
With GroupID, the zero trust security model can be implemented as follows:
- Authenticate users sending email to a group.
- Filter users who can email a group.
- Protect it like a fortress in group membership.
- Manage with workflows.
- Simplify group approval.
- Simplify verifying group permissions.
- Use easier-to-use security options.
- Authenticate users sending email to a group.
- The best way to identify a sender is to require authentication when communication starts.
- In GroupID, you can enable the "Authentication to send mail" setting in the group properties to block emails from users that cannot be authenticated in the domain the group is in. This ensures that group members only receive email from trusted senders.
Zero trust security is primarily based on 100% certainty about the identities of trusted senders. To achieve this paradigm, GroupID helps you design a mechanism to identify trusted senders. Once you do that, you can mark or block the corresponding email without the risk of blocking it.
Using GroupID, you can apply the following restrictions to an Active Directory group in your Identity framework.
- Allow the group to receive email only from group owners or members, or both.
- Allow group to receive email from specific users and groups.
- Block emails from specific users and groups.
- For GroupID Dynasties you only need to manage these settings for parent Dynasty as it can be controlled by inheritance to be passed on to all subgroups.
As a result, GroupID treats all unknown entities such as domains, sending services, and contacts as untrusted entities unless you allow them.
Both authentication and filters are built into the collaboration platform (Exchange on-premises and Exchange online / MS 365). The magic of GroupID is that it exposes these IT-focused and often forgotten features to group owners who are often unaware that these controls reside with the messaging provider. In this way GroupID gives them access to these backend features they would otherwise never see.
Protective walling in Active Directory, Azure AD, and Office 365 group membership:
- 1.498 / 5.000 Çeviri sonuçları Çeviri sonucu Because security groups allow access to resources and even classified information, it is imperative to be vigilant about their membership. Manual methods are very slow and inefficient; IT is overloaded with membership change requests and human error occurs. GroupID's precise approach to secure memberships is easier and more accurate, as group membership is automatically checked by a query.
- In GroupID, you can create powerful LDAP queries to enable dynamic memberships for security groups, distribution lists, and Office 365 groups. GroupID has a custom query designer that provides an easy-to-use interface for building complex queries. Simply specify the type of object (groups, computers, users, messaging system recipients, etc.) to be returned by your query, and add attributes (such as department, company, location, and more) as filters. Boost speed even more with an external data source where GroupID connects to the data source and queries the index server for matching records. Moreover, you can write scripts to manipulate the query results.
This query is defined once and programmed for autorun. Queries the index and updates the group membership with records that meet all its rules. This way, groups are automatically updated when directory information changes, allowing administrators to easily manage large groups without having to manually add or remove members.
Manage with workflows:
While directory groups contribute to corporate effectiveness, IT administrators should carefully monitor group membership for accuracy and security.
Since memberships can be changed with any change in a group's query, what security does GroupID have to offer?
- Workflows come to the rescue by subjecting all changes to audit and approval, thus promoting a truly zero-trust security model in your on-premises and hybrid cloud identity environments.
A workflow in GroupID is built on:
- Object (group, user, person) to which the workflow applies
- Event (add, edit, delete)
- Active Directory, Azure AD, Exchange, or GroupID attribute to monitor
- User(s) to submit the workflow request for approval
- This flexible approach to creating workflows allows you to track changes made to objects based on any event and attribute. Based on this, you can define workflows that control changes in a group's query. GroupID's historical tracking functionality also logs changes to group attributes and memberships.
All of this combined allows you to achieve zero-trust security enforcement in your on-premises and hybrid identity environments.
Simplify group approval:
Re-examine your awareness of your Active Directory and Azure AD groups by asking yourself the following questions.
- Do you have orphan groups (orphan groups)?
- Are there groups that exceed their goals?
- Do groups have members who should no longer be part of those groups?
Periodic group approval is key to answering these questions. Zero trust security practices, including the following, are a block in the chain, where group owners review and confirm that certain aspects of a group's configuration are correct and up-to-date.
- Group Membership – Nested groups are authenticated as users and/or members. They represent the current user group using the group's assigned permissions.
- Group Permissions – Assigned permissions are verified. It should be limited to what group members have to perform their duties.
- Group attributes – Different attributes of a group are validated, such as description, email, and expiration policy.
- Group Entity – The necessity of the group for business is verified. Groups that do not have a valid purpose should be deleted or disabled.
- In GroupID, administrators can force group owners to review and verify an expired group's properties and membership before renewing it. During confirmation, members can be removed from group membership instantly or deactivated after a certain day and then removed.
Simplify verifying group permissions:
To protect your data, you must first understand where it is, who has access to it, and how access is granted. Without this knowledge, zero trust security can remain a dream.
- Active Directory authorization management can help you efficiently manage access to data such as file servers and other resources.
- It also assists you in SharePoint environments for internal users and users outside of your organization who need access to these resources.
GroupID Entitlements allow you to achieve this goal with ease. Use for:
- Discover 'file shares' from domain-joined file shares.
- Analyze the permissions on each folder and file.
- View reports on cascading entitlements from inheritance.
- Interact with data in drill-down reports that show perspective from the resource authorization view and the authorized user view of resources.
- With this level of insight, it's easy to implement a zero-trust security model. You can ensure that access to sensitive data is private.
- Permissions are the lowest possible value to perform a role or function.
Easier to use security options:
GroupID has a lot more to offer when it comes to a truly zero-security security model.
- GroupID can identify orphan groups and ensure that each group has an owner. With support for multiple owner and group approvals, GroupID supports groups with no foreign members.
- Active Directory, Azure AD, and Office 365 groups can contain temporary members, so users who need temporary access are automatically removed from the group when the need is over.
- Access to physical resources and information assets can be limited by setting expiration dates for groups.
Conclusion:
Organizations always want the safest paths and safest architectures for themselves. Our belief is precisely in this direction that every institution, regardless of small or large, should achieve the best of everything, as they wish. AD etc. It is a critical issue to constantly monitor the security for environments, to constantly review the rules you write, and to keep these rules up to date. Pentests at the 'T' moment will give you a screenshot of that moment. However, automating and supervising this will keep you up-to-date and protect you about the security of such structures in your institution.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.