Endpoint protection has always been a very important area of cybersecurity because of the sensitive data held at the endpoints. The importance of working from home has increased even more. Company employees working remotely can no longer take advantage of the full cybersecurity shields of the corporate network. In these new conditions, new generation endpoint protection solutions that can significantly reduce the attack surface, can react automatically, make automatic decisions and have self-healing features come to the fore.
Let's take a look at some statistics for 2019 while we are getting into the subject:
- 30% of all attacks are zero-day attacks.
- 76% of successful attacks on endpoints are zero-day attacks.
- 56% of institutions were affected by Cryptolocker and derivative attacks.
Just by looking at these figures, it is impossible to provide endpoint protection with old generation anti virus solutions. Even anti-virus solutions that work based on signatures or use simple-level heuristic algorithms can cause harm, let alone benefit, by creating an "empty sense of protection" in users. For example, an employee, assuming that the content of every e-mail from a trusted person is reliable, can click on the link in the e-mail, infecting his own computer with a fresh Cryptolocker malware and then infecting all the computers in the network. When Cryptolocker finishes its job silently, that is, encrypts all data on computers and shares bitcoin wallet information, companies may have to choose between "returning from the latest backup" or "depositing the desired amount of bitcoin into the hacker's account".
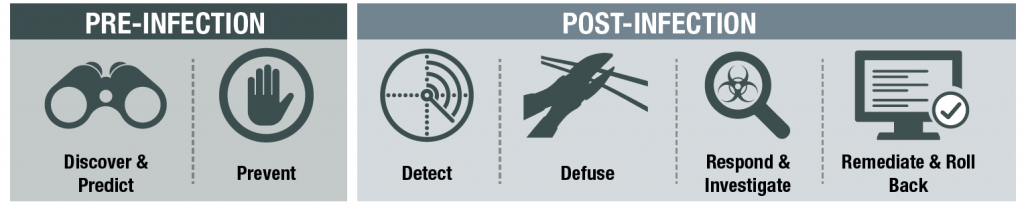
So what exactly do we mean when we say next-generation endpoint protection?
Essential devices we need to protect:
- Laptop
- PC
- Mobile Phone
- Tablet
- Presenter
The main pests we need to be protected from:
- Viruses
- Malware
- Ransomware
- Spyware
Key tasks for next-generation endpoint protection to undertake:
- Predict – Forecast
- Prevent – Block
- Detect- Reveal
- Defuse – Neutralize
- Respond & Investigate – Respond & Investigate
- Remediate & Roll back – Cure & Roll back

Our main goal in endpoint protection is to build the strongest fortress possible on our devices. These strong fortresses can be built with next-generation endpoint protection solutions. But keeping in mind that no fortress is impenetrable or impenetrable, we must continue to consider our cybersecurity strategy holistically and increase our cybersecurity maturity level day by day.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












