What is Penetration Testing?
Penetration testing is a system control mechanism used to determine the security of systems and networks in attacks on systems, networks and devices to demonstrate how vulnerable a system or target is to an actual attack.
Importance of Penetration Testing and Test Types in Web Applications:
Web applications are one of the important elements that reflect the identity of an organization. Therefore, in penetration tests carried out to ensure corporate information security, the first thing to consider is the institution's web applications. Penetration tests performed on web applications can be classified in three different ways, depending on the scope of the test and the information presented to the expert. These classifications are: Black box penetration tests, white box penetration tests, and gray box penetration tests.
Black box testing is simply testing the application without knowing what kind of system works behind it. We test like a normal user. It is a test we do without knowing how the code behind the functions and units works. The important things in this test are inputs and outputs.
White box testing, just like its name, is a technique in which test scenarios are designed by looking through a white box and knowing the internal structure of the system. The main purpose of this method is to provide more benefits to the institution compared to the black box approach. It becomes easier to find vulnerabilities and the time it takes to take precautions decreases. At the same time, it allows the transaction to be completed without any wrong action or damage to the system.
Another type of penetration testing, gray box penetration testing, is a mixture of both black box testing and white box testing. In testing, while we have system data, tests are also carried out while the system is running. In this way, dynamic analysis is applied. Therefore, while the system is tested dynamically during operation, its internal structure is also examined by static analysis. In this way, a comprehensive penetration test is performed, taking into account both the source code and runtime behavior.
Web Penetration Testing Steps:
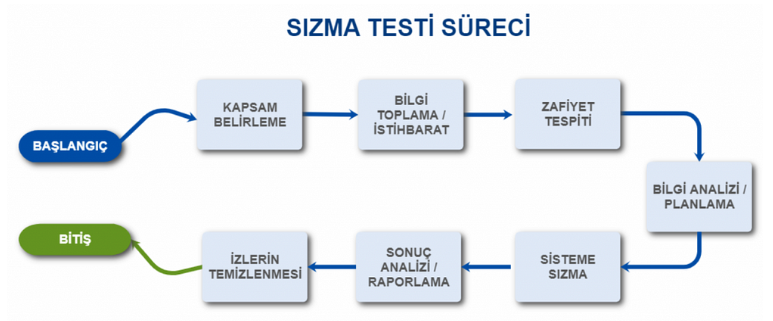
Pre-Agreement Interaction (Scoping):
Explanation of the methods and tools to be used in the test; our limits, the agreed time for the completion of the test, what will be tested and additional support for things not specified in the scope. Notifying the institution that will perform the test and obtaining approval.
Data Collection:
Information gathering phase (OSINT) is the process of obtaining all possible information about the target to conduct a comprehensive security assessment. In this process, information about the target company or system is collected using technical and non-technical methods on the internet. The purpose of this phase is to create the most appropriate rotation for the attack and to make a solid start once we find a way.
Vulnerability Scanning:
This phase uses automated tools to perform penetration testing to understand, contain, and then search for commonly known vulnerabilities in the target web application. The purpose of this stage is to detect vulnerabilities without damaging the target system by using automatic vulnerability scanning tools and to control these vulnerabilities using known exploitation methods. Scan results are verified by a penetration tester to eliminate false positives and false negatives. As a result of vulnerability detection and analysis, the probability and scenario of the target system being compromised are determined.
Exploitation:
Testing of the target system and its security is carried out by trying to exploit the vulnerabilities detected after vulnerability scanning. It attempts to bypass security measures to gain access to the target system and gain as much connection access as possible. Tests are performed on the target system by using or creating appropriate tools to exploit identified vulnerabilities.
After abuse:
It is necessary to determine the value of the information contained on the seized machine and to maintain control of the machine in order to use it for other targets in the network.
Reporting:
The report should include all technical details about the test and the assets and components agreed upon for testing. The agreed option for the scope should include the information obtained, the attack technique applied, the methods used, the degree of impact and risk, and suggestions on how to improve the system.
Cleaning:
During the cleaning phase, all applications used and installed on the system are removed while performing the penetration test.
Attacks analyzed in Web Application Penetration tests:
Cross-site Scripting (XSS) Attacks
SQL Injection Attacks
Broken Authentication and Session Management
File Upload Vulnerability
Cache Poisoning Vulnerability in Servers (Caching Servers Attacks)
Security Misconfigurations
Cross Site Request Forgery
Directory Traversal Attacks
Web Application Pentest Tips:
Team Training
When creating a team, recruiting competent people in their fields and then providing training to these teammates on the tips that need to be known within the scope is among the most important clues in terms of the progress and success rate of the work. This training will help employees understand security policies and procedures, be more responsive to detecting security vulnerabilities, and contribute more effectively to preventing security breaches.
Determining Scope
During the web application security testing process, it is a principle that must be strictly implemented, especially not to go beyond the scope previously determined and approved in writing by the customer or employer, and if necessary, to obtain approval from the employer.
Using Automation Tools
When starting security tests, it is important to get a quick start by using automation tools (such as Burp Suite, Nessus) to increase the efficiency of security tests and to identify basic security vulnerabilities that can be detected at the beginning. These tools offer automatic scanning and analysis capabilities, allowing us to more quickly identify potential threats that are difficult to detect manually.
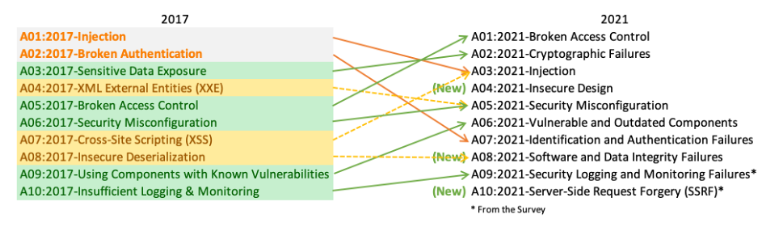
OWASP Top 10 Review
When beginning web application security testing, a critical step is to review the OWASP Top 10 list of the most common web application vulnerabilities identified by the Open Web Application Security Project (OWASP). This list identifies the most common security vulnerabilities faced by web applications and offers precautions to prevent these vulnerabilities from being exploited.
Checking Data Entry
During web application security testing, it is important to check data inputs. To give an example for data entries:
Data Entry Limits: It is necessary to test the limits of data entries and they should be limited to prevent a possible attack against overflow or boundary problems.
Special Characters: It is necessary to detect security vulnerabilities by adding special characters (“,’), for example, SQL injection characters.
Invalid Data: Evaluate how to deal with unexpected or invalid data.
Form Fields Manipulation: Testing the response of form fields by sending unexpected data types (php instead of img) or sizes.
Inappropriate Content Attempts: Inserting HTML or JavaScript codes for XSS vulnerabilities.
Sending Nonfunctional Data: Examining the application's response with empty or unnecessary data.
Long and Complex Inputs: Evaluating how the application responds to long and complex data.
These steps are some of the tips we should keep in mind before we start the test.
Tips For Reporting
Using Clear and Short Titles:
The title of the prepared report should clearly express the purpose and content of the report. It should be clear what the report is about by looking at the title.
Presenting a Summary:
A brief summary should be provided at the beginning of the report, providing readers with a quick overview. This summary should summarize the main findings and conclusions of the report.
Using Accurate and Objective Language:
When writing our report, our language should be clear, accurate and objective. We should also explain or, if necessary, define technical terms.
Originality and Sources:
We must indicate the sources of the data and information used in our report. This increases the credibility of our report.
Using Images:
We must make the data more understandable by using visual elements such as statistics, graphs, tables and diagrams. Visuals can reduce complexity and highlight important information.
Highlighting Key Points:
We can draw attention within the text by using bold or italics or colored text to highlight key findings and recommendations.
Using a Logical Structure:
We must organize our report in a logical structure. We must first cover the main issues and then explain these issues in more detail. In this way, we make it easier for readers to follow the report.
Presenting Technical Details in Good Balance:
While giving technical details, we must balance it with the target audience of our report in mind. We must be descriptive and understandable for more general readers, while providing in-depth information for technical experts.
Supporting with Concrete and Examples:
We must support a problem or suggestion with concrete examples and evidence. This helps readers understand and accept better.
Keeping Communication Channels Open:
At the end of your report, we should include your contact information so readers can ask any questions or get more information.
Conclusion and Summarization:
At the end of your report, summarize the main results and improvement measures. Remind readers of the overall importance of the report. In this way, we can write a report that is both efficient and understandable.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












