In today's web application world; WordPress web applications, which are practical at the installation stage, appealing to many people in terms of use, and have a less costly structure compared to the architectures of their own lane in economic size, bring many security weaknesses in terms of using Third (3rd) party plugins and ready-made themes. Therefore, there are some points that can be tested and taken security measures at a basic level, both in terms of the pentester and in terms of security management of your WordPress site.
These;
1. XML-RPC is a WordPress feature that allows data transfer by working as HTTP's kind of transport mechanism and XML's encoding mechanism.
- Using the xmlrpc.php file, the attacker can try hundreds of different passwords and usernames using just one command. In this way, it can disable security tools that can usually detect and prevent brute force attacks.
- By using the pingback feature in Xmlrpc.php, attackers can turn this into a DDoS attack. It can provide an almost unlimited number of IP addresses.
To avoid the mentioned security vulnerabilities, simply disabling this file will provide protection up to a point.
2- oEmbed is designed to eliminate the need to copy and paste HTML code from the site hosting the media you want to upload. It supports videos, images, text and more.
- /wp-json/oembed/1.0/embed?url= author usernames etc due to mishandling of authors' names, which allows the web application to obtain sensitive information through a request. information can be obtained.
Either this feature must be disabled or configured correctly.
3- Dompdf.php Dompdf is essentially a CSS 2.1 compatible HTML layout and rendering engine written (mostly) in PHP. It is a style driven builder. Downloads and reads external style sheets, inline style tags, and style properties of individual HTML elements. It also supports most HTML attributes.
- Multiple plugins can cause Dompdf unauthenticated Local File Inclusion (LFI) vulnerability.
Therefore, dompdf.php must be configured correctly.
4- As it is known, REST is a kind of service that processes HTTP requests. Thanks to this service, operations such as changing, updating, deleting the web resource can be performed using the standard functions of HTTP. Today, many mobile applications and wordpress applications provide their relations with the data layer with REST APIs.
- Sensitive data can be disclosed via rest api's such as //example.com/wp-json/wp/v2/users. For example, usernames can be captured via the wp-json/wp/v2/users api.
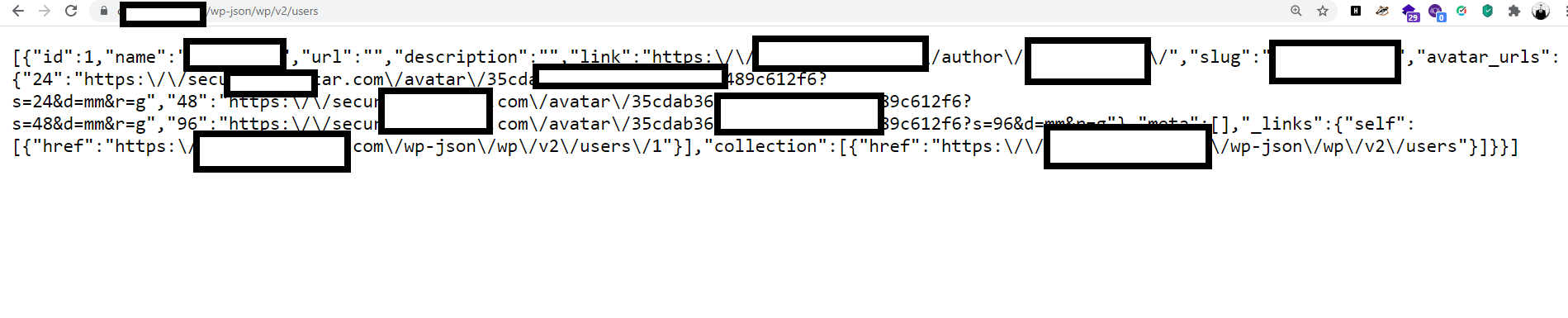
To remove all default REST API endpoints you need to add the following code:
‘’<?php remove_action(‘rest_api_init’, ‘create_initial_rest_routes’, 99); ?>’’
5. If the target wordpress site has the register feature enabled (disabled by default), calling the register link directly will get you into the site.
- Login is provided using https://wordpresssite/wp-login.php?action=register.
In order to prevent this, it should be checked whether the register feature is active or not.
6- It comes with a built-in code editor that allows you to edit your WordPress theme and plugin files directly from your WordPress admin area.
- When attackers access this area, it can pose a security risk because they could inject malicious php code there. That's why we recommend turning it off.
You can do this easily by adding the following code to your wp-config.php file.
define( ‘DISALLOW_FILE_EDIT’, true );
7- In non-essential directories such as /wp-content/uploads/, PHP file execution should be disabled to avoid code execution vulnerability.
8- Directory browsing can be used by hackers to find out if you have any files with known vulnerabilities so they can exploit those files to gain access.
Find the .htaccess file in the root directory of your website. After that, you need to add the following line at the end of the .htaccess file:
After adding Options -Indexes, don't forget to save the .htaccess file and upload it back to your site.
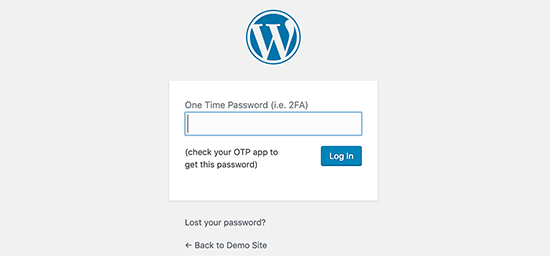
9- Wp-Admin login form screen should not be named as predictable. Login attempts should be limited and two-factor authentication should be introduced. You can also add additional password protection on the login form page at the server-side level, which will effectively block these requests.
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












