Information and Communication Security Guide Uygulama Süreci Şekil 5’te tanımlanmıştır. Süreç; planlama, uygulama, kontrol etme ve önlem alma ile değişiklik yönetimi alt süreçlerinden oluşmaktadır.
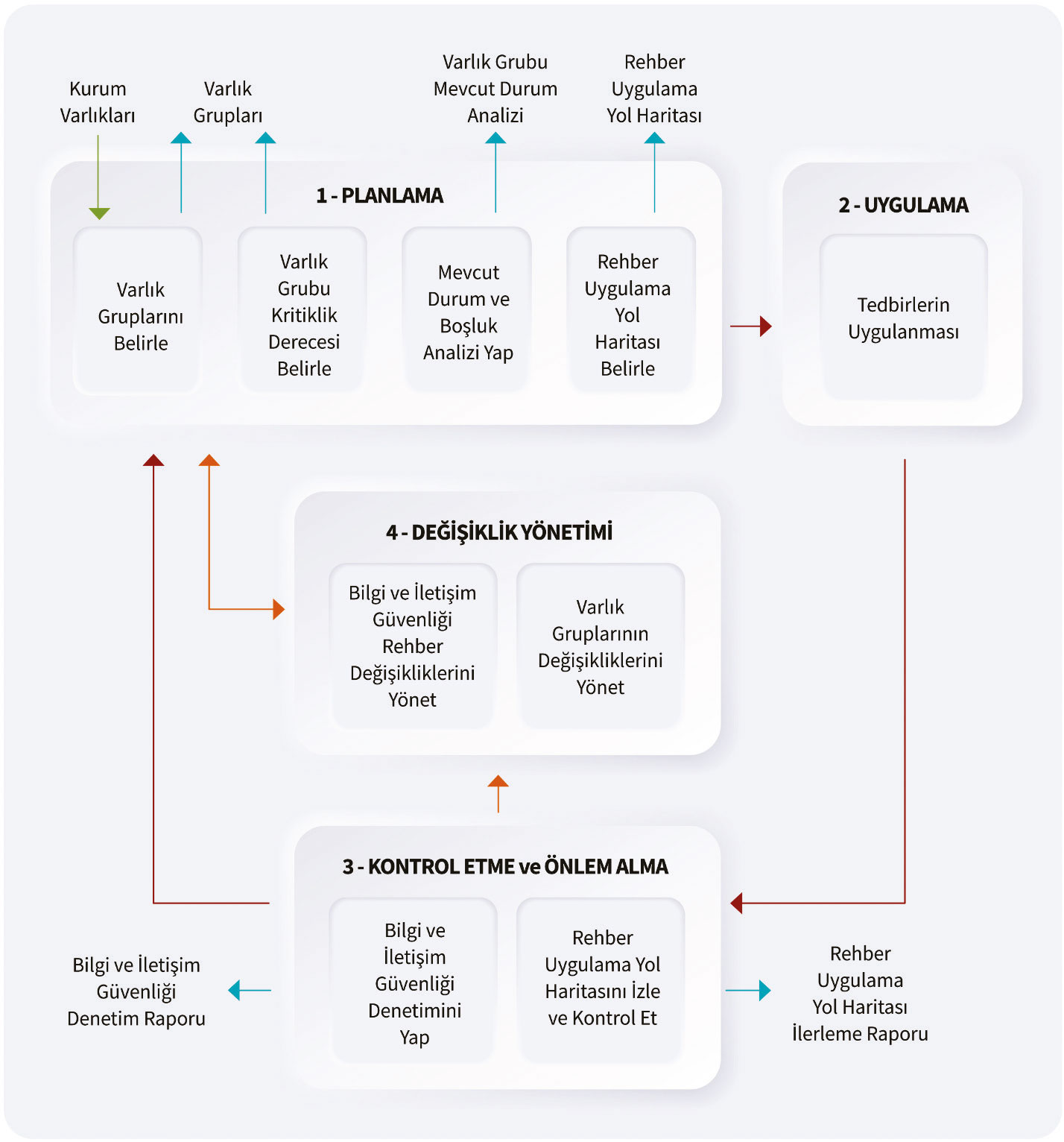
Figure 5. Implementation Process of the Information and Communication Security Guidelines
In summary, within the scope of planning; The activities are carried out by grouping the corporate assets, making the criticality rating of the asset groups obtained as a result of the grouping, analyzing the current situation of the security measures to be applied to this asset group, and preparing the road map by making gap analysis. Studies to be carried out in accordance with the roadmap are carried out in the implementation sub-process. Monitoring and control activities of the works carried out within the scope of the guide are carried out within the scope of the control and taking precautions. In the phase of controlling and taking precautions, internal and external audit activities are also carried out in order to determine the implementation status of the measures in the guide. Determining the changes to be made in order to comply with the updates in the guide, ensuring the compliance of the changes that will take place in the institution asset groups (change of the asset group content, definition of new asset groups, change in the asset group criticality level, etc.) with the measures defined in the guide are handled within the scope of change management. In the following sub-headings, the phases defined in Figure 5 and the activities to be carried out within these processes are explained. Table 1 contains explanations of the abbreviations for SAM roles. The activities to be carried out within the scope of sub-processes and the responsibilities defined specifically for the sample roles for each activity are indicated in the SAM table in Table 2.
Table 1. SAM Roles Descriptions
Abbreviation | Description |
S | Responsible: Task performer personnel |
O | Approved by: personnel who can suspend, resume, make the final decision and be accountable |
D | Client: personnel whose knowledge should be consulted before performing the task |
B | Informed: personnel who is informed that the task is finished after the task is done |
Roles in Table 2; It is handled under two categories as internal stakeholder and external stakeholder and is expressed as the task undertaken by the relevant personnel or assigned to that person. The activities to be carried out in line with the sub-processes are defined as activities, and each role has areas of responsibility and authority defined specifically for the activities.
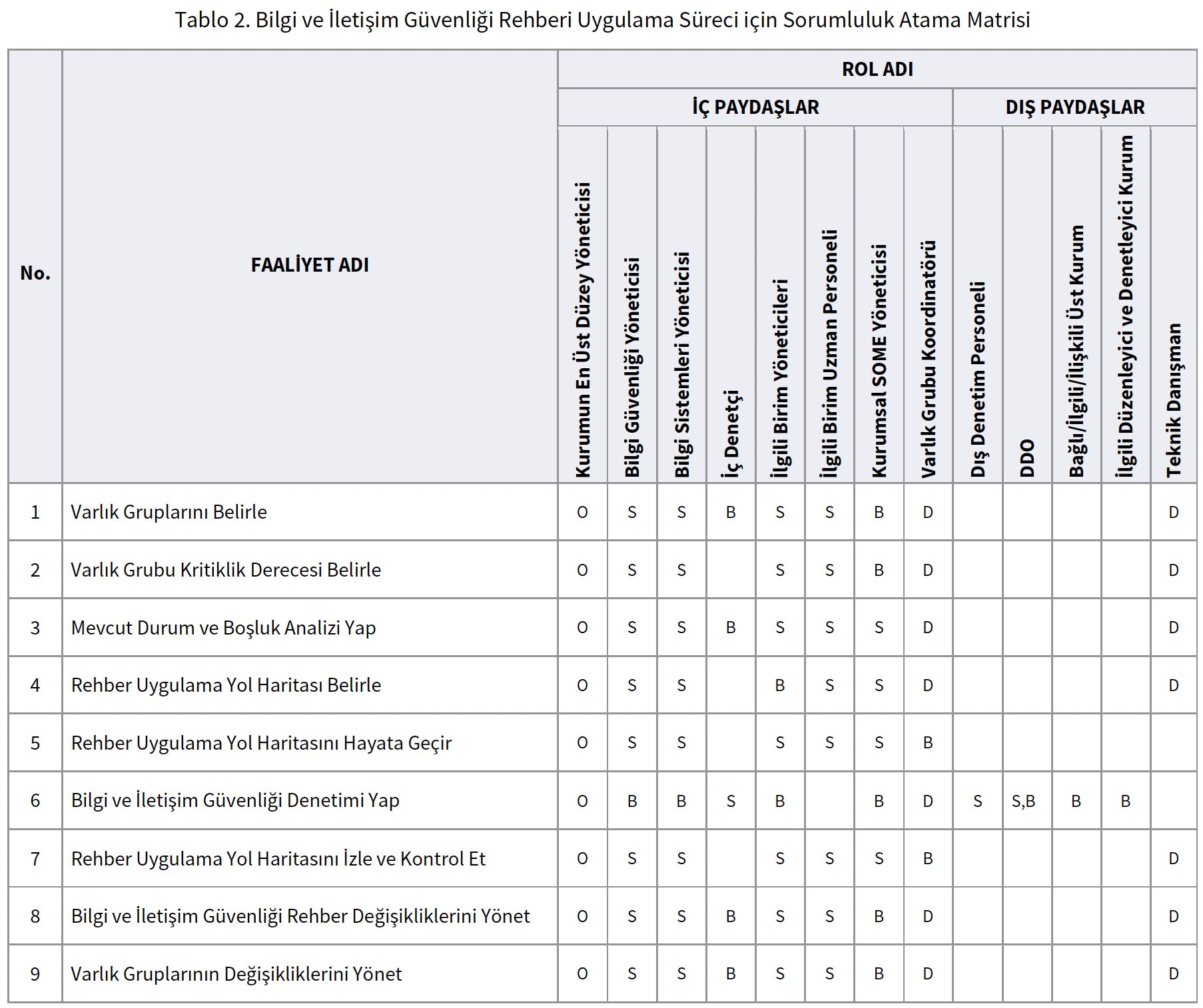
The descriptions of the roles mentioned in Table 2 are given below:
Top Level Manager of the Organization: The person in the highest position in the organization hierarchy responsible for ensuring and managing information security.
Information Security Manager: Personnel responsible for ensuring and managing information security in the institution.
Information Systems Manager: Personnel/unit manager responsible for the management of information systems in the institution.
Internal Auditor: Personnel performing internal audit in the organization. Relevant Unit Managers: Unit managers in the institution who will be responsible for realizing the stages in the implementation process of the Guide.
Relevant Unit Expert Personnel: Unit personnel who will be responsible for carrying out the stages in the guideline implementation process.
Corporate SOME Manager: The manager of the cyber incident response team in the institution.
Asset Group Coordinator: Personnel whose knowledge is consulted at the stages of the guideline implementation process and who coordinate these stages.
External Audit Personnel: Third-party auditors who audit whether the guideline implementation process and security measures are implemented in the organization.
DDO: Presidential Office of Digital Transformation
Affiliated/Related/Associated Senior Institution: The higher institution to which the Institution is affiliated/related/related (eg Ministries).
Relevant Regulatory and Supervisory Authority: Regulatory/supervisory institutions such as BRSA, EMRA, SPK and BTK.
Technical Advisor: Third-party staff whose knowledge is consulted during the guideline implementation process.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












