Active Directory kısaca ağ nesnelerini ve kullanıcı bilgilerini depolayan, bu bilgilere ulaşımı ve bilgilerin yönetilmesini kolaylaştıran bir servistir. Ağdaki kullanıcılara kurallar tanımlamak, paylaşılan dosya ve yazıcılara erişmek, ağda kimlik doğrulaması yapmak gibi işlemleri yerine getirmesi için oluşturulmuş servisler bütünüdür.
Domain:
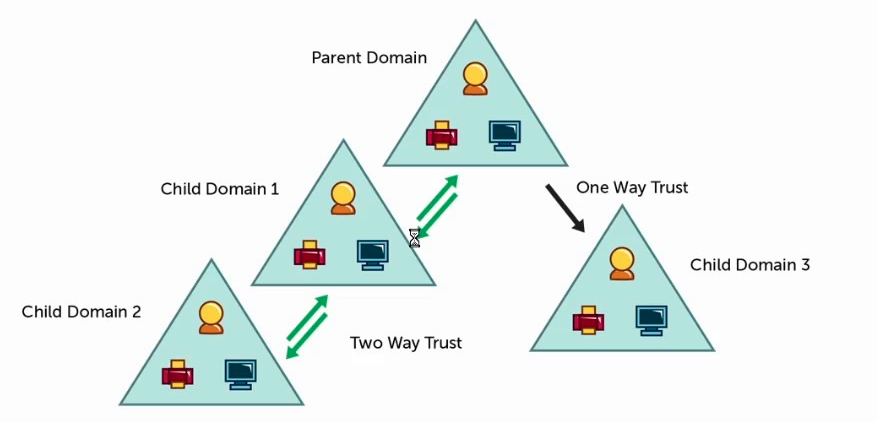
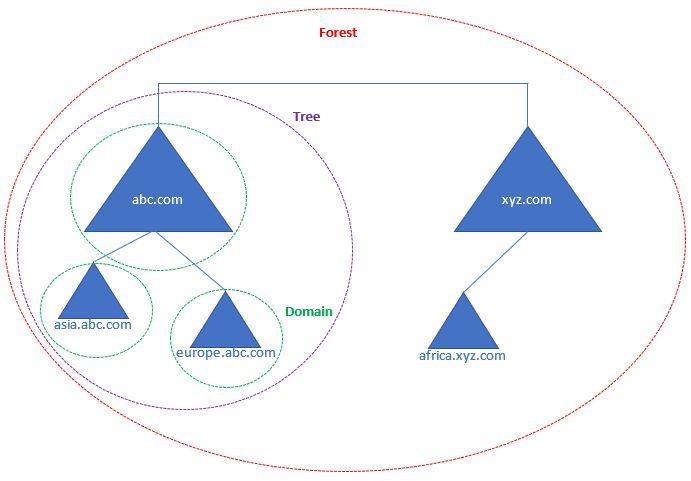
Aynı veritabanını paylaşan bilgisayarlar bütünü olarak da bilinmektedir. Her bir Domain benzersiz bir isme sahiptir ve Domain adı en az iki kısımdan oluşmalıdır, Türkçe karakter olmamalı ve benzersiz olmalıdır. İlk kurulan domain kök domaindir ve hemen altına ağaç yapısı şeklinde devam eden her domain Child domain olarak adlandırılır. Ancak child domain altına yeni bir domain eklediğinizde artık kendisi de sonra eklenen domain ile karşılaştırıldığında Parent domain olarak nitelendirilebilir. Aynı isim altında birden fazla domain yapısının olduğu ağaç yapısına Tree denir. Bu yapı Parent ve Child domainlerden oluşur.
Birden fazla Tree yapısının olduğu yapıya Forest denir. Forest mantıksal yapıdaki en dış katmandır.
- Enterprise Admin: İlk kurulan domain içerisinde bulunur. En yetkili kişidir.
- Global Katalog: Tüm DC bilgilerini barındırır ve Forest yapısında ilk kurulan domain içerisinde bulunan ilk DC global katalog olarak bilinir.
- Forest Root: İlk kurulan Forest yapısındaki domaindir.
Organizational Unıt (OU): Domain içerisindeki nesneleri organize etmeyi sağlayan birimlerdir. Kullanıcı hesapları, grup hesapları, bilgisayar hesapları, yazıcılar, paylaşılmış klasörler bu birimin içerisinde yer alırlar ve organize edilirler. Böyle bir düzenleme yetkilendirme aşamasını da kolaylaştırmaktadır. Böylece yapacağınız düzenlemeler “Users” klasörü altında olan tüm kullanıcıları değil sadece ilişkili birimi etkileyecektir. Ek olarak böyle bir düzenleme sayesinde birimler içerisinde kişiye özel yetkilendirmeler de yapılabilmektedir.
Active Directory Üzerinde Yetkilendirmeler
Bir domain içerisinde bulunan Domain Admin, diğer domain alanlarına müdahale edemez. Tüm domainlere müdahale edebilen tek kişi Enterprise Admin’dir. Bilgisayar korsanları sızma sırasında bir Domain Admin hesabı ele geçirdiyse, bu sadece ilişkili domain üzerinde işlemler yapabileceği ve yetkilerinin sadece o domainde kaldığı anlamına gelmektedir. Eğer bütün forest yapsını yönetmek ister ve yetkilerini de genişletmek isterse, Enterprise Admins grubuna girmeyi başarması gerekmektedir.
Kuruluşunuzu Siber Tehditlere ve Saldırılara Karşı Korumanın Önemli Yolları
- Şirket içi Active Directory ve bulut ortamlarındaki kimlik grupları (dağıtım listeleri, güvenlik grupları, Microsoft 365 grupları).
- Microsoft 365 araçları (SharePoint ve Yammer gibi).
- Microsoft Teams gibi iş iletişimi platformlarındaki kanallar.
Gruplar bir organizasyonun işleyişi için vazgeçilmezdir. Dağıtım listeleri ve kanallar bir kuruluştaki iletişim ağını oluştururken, güvenlik grupları varlıkları ve kaynakları yetkisiz erişime karşı korur. Yine de sosyal mühendislik tehditlerine ve saldırılarına karşı savunmasızdırlar.
Dağıtım listeleri için saldırı yöntemleri gelişti. Resmi olarak tehditler büyük ölçüde içerik merkezliydi (e-postanın kötü amaçlı bir bağlantı veya ek içerdiği durumlarda). Bugün, araştırmalar, e – posta saldırılarının neredeyse % 90’ının, alıcıları kandırmak ve sosyal mühendislik saldırıları başlatmak için gönderen kimliğini manipüle ettiğini gösteriyor.
Bu Açıdan Bakıldığında Active Directory, Azure AD ve Microsoft 365’teki Gruplar İçin Sıfır Güven Güvenlik Modeli Ne Anlama Geliyor?
Dağıtım grupları için çözüm yöntemleri basit sayılır.
- Kimlik doğrulaması yapın, ardından filtreleyin. Bu, kimliği doğrulanabilen ve bu gruba ileti teslim etmek için açık izni olan bir göndericiden gelmedikçe iletilerin teslimine izin vermemekle ilgilidir.
GroupID aracılığıyla Sıfır Güven Güvenliği nasıl uygulanmalı?
- Kimlik yönetimi ortamlarınızda (Active Directory, Azure AD ve Office 365) sıfır güven güvenlik modeli uygulamanın etkili bir yolu, GroupID by Imanami’yi BT altyapınıza entegre etmektir.
GroupID, dağıtım listelerine ve güvenlik gruplarına sıfır güven güvenliği uygulamak için kullanışlı ve güçlü bir yaklaşım sunar ve böylece kimlik tabanlı saldırıları ve bilgisayar korsanlarını engeller.
GroupID ile sıfır güven güvenlik modeli aşağıdaki gibi uygulanabilir:
- Bir gruba e-posta gönderen kullanıcıların kimliğini doğrulayın.
- Bir gruba e-posta gönderebilen kullanıcıları filtreleyin.
- Grup üyeliğinde bir kale gibi koruyun.
- İş akışlarıyla yönetin.
- Grup onayını basitleştirin.
- Grup izinlerini doğrulamayı basitleştirin.
- Kullanımı daha kolay güvenlik seçenekleri kullanın.
- Bir gruba e-posta gönderen kullanıcıların kimliğini doğrulayın.
- Bir gönderenin kimliğini belirlemenin en iyi yolu, iletişim başladığında kimlik doğrulamasını zorunlu kılmaktır.
- GroupID’de, grubun bulunduğu etki alanında kimliği doğrulanamayan kullanıcılardan gelen e-postaları engellemek için grup özelliklerinde “Posta göndermek için kimlik doğrulaması” ayarını etkinleştirebilirsiniz. Bu, grup üyelerinin yalnızca güvenilir göndericilerden e-posta almasını sağlar.
Sıfır güven güvenliği, öncelikle güvenilir göndericilerin kimlikleri hakkında %100 kesinliğe dayanır. Bu paradigmayı elde etmek için GroupID, güvenilir göndericileri belirlemek için bir mekanizma tasarlamanıza yardımcı olur. Bunu yaptıktan sonra, ilgili e-postayı engelleme riski olmadan işaretleyebilir veya engelleyebilirsiniz.
GroupID’yi kullanarak, Kimlik çerçevenizdeki bir Active Directory grubuna aşağıdaki kısıtlamaları uygulayabilirsiniz.
- Grubun yalnızca grup sahiplerinden veya üyelerinden veya her ikisinden e-posta almasına izin verin.
- Grubun belirli kullanıcılardan ve gruplardan e-posta almasına izin verin.
- Belirli kullanıcılardan ve gruplardan gelen e-postaları engelleyin.
- GroupID Dynasties için, tüm alt gruplara aktarılmak üzere devralma yoluyla kontrol edilebildiğinden, yalnızca ebeveyn Dynasty için bu ayarları yönetmeniz gerekir.
Sonuç olarak GroupID, izin vermediğiniz sürece, etki alanları, gönderen hizmetler ve kişiler gibi tüm bilinmeyen varlıkları güvenilmeyen varlıklar olarak değerlendirir.
Hem kimlik doğrulama hem de filtreler, işbirliği platformunda yerleşik olarak bulunur (Şirket içi Exchange ve çevrimiçi Exchange / MS 365). GroupID’nin büyüsü, bu BT odaklı ve genellikle unutulan özellikleri genellikle bu kontrollerin mesajlaşma sağlayıcısında bulunduğunun farkında olmayan grup sahiplerine ifşa etmesinde yatar. Bu şekilde GroupID, aksi takdirde asla göremeyecekleri bu arka uç özelliklerine erişimleri sağlar.
Active Directory, Azure AD ve Office 365 grup üyeliğinde koruyucu duvar örme:
- Güvenlik grupları, kaynaklara ve hatta sınıflandırılmış bilgilere erişime izin verdiğinden, üyelikleri konusunda uyanık olmak zorunludur. Manuel yöntemler çok yavaş ve verimsizdir; BT, üyelik değişikliği istekleriyle aşırı yüklenmiştir ve insan hatası meydana gelir. Grup üyeliği bir sorgu tarafından otomatik olarak kontrol edildiğinden, GroupID’nin güvenli üyeliklere yönelik kesin yaklaşımı daha kolay ve doğrudur.
- GroupID’de, güvenlik grupları, dağıtım listeleri ve Office 365 grupları için dinamik üyelikleri etkinleştirmek adına güçlü LDAP sorguları oluşturabilirsiniz. GroupID, karmaşık sorgular oluşturmak için kullanımı kolay bir arabirim sunan özel bir sorgu tasarımcısına sahiptir. Sorgunuz tarafından getirilecek nesne türünü (gruplar, bilgisayarlar, kullanıcılar, mesajlaşma sistemi alıcıları vb.) belirtmeniz ve filtreler olarak öznitelikleri (departman, şirket, konum ve daha fazlası gibi) eklemeniz yeterlidir. GroupID’nin veri kaynağına bağlandığı ve eşleşen kayıtlar için dizin sunucusunu sorguladığı harici bir veri kaynağıyla hızını daha da artırın. Dahası, sorgu sonuçlarını değiştirmek için komut dosyaları yazabilirsiniz.
Bu sorgu bir kez tanımlanır ve otomatik çalıştırma için programlanır. Dizini sorgular ve grup üyeliğini tüm kurallarını karşılayan kayıtlarla günceller. Bu şekilde, dizin bilgileri değiştiğinde gruplar otomatik olarak güncellenir ve yöneticilerin manuel olarak üye eklemek veya kaldırmak zorunda kalmadan büyük grupları kolayca yönetmesine olanak tanır.
İş akışlarıyla yönetin:
Dizin grupları kurumsal etkinliğe katkıda bulunurken, BT yöneticileri de doğruluk ve güvenlik için grup üyeliğini dikkatli bir şekilde izlemelidir.
Üyelikler bir grubun sorgusunda herhangi bir değişiklikle değiştirilebildiğinden, GroupID’nin güvenlik olarak sunabileceği ne var?
- İş akışları, tüm değişiklikleri denetime ve onaya tabi tutarak kurtarmaya gelir ve böylece şirket içi ve hibrit bulut kimlik ortamlarınızda gerçekten sıfır güven güvenlik modelini teşvik eder.
GroupID’deki bir iş akışı aşağıdakiler üzerine kuruludur:
- İş akışının geçerli olduğu nesne (grup, kullanıcı, kişi)
- Etkinlik (ekleme, düzenleme, silme)
- İzlenecek Active Directory, Azure AD, Exchange veya GroupID özniteliği
- İş akışı talebini onay için gönderecek kullanıcı(lar)
- İş akışları oluşturmaya yönelik bu esnek yaklaşım, herhangi bir olaya ve özniteliğe göre nesnelerde yapılan değişiklikleri izlemenizi sağlar. Buna dayanarak, bir grubun sorgusundaki değişiklikleri kontrol eden iş akışları tanımlayabilirsiniz. GroupID’nin geçmiş izleme işlevi, grup özniteliklerinde ve üyeliklerinde yapılan değişiklikleri de günlüğe kaydeder.
Tüm bunlar bir araya geldiğinde, şirket içi ve hibrit kimlik ortamlarınızda sıfır güven güvenlik uygulaması elde etmenizi sağlar.
Grup onayını basitleştirin:
Kendinize aşağıdaki soruları sorarak Active Directory ve Azure AD gruplarınız hakkındaki farkındalık düzeyinizi yeniden inceleyin.
- Yetim gruplarınız (sahipsiz gruplar) var mı?
- Amaçlarını aşan gruplar var mı?
- Grupların artık bu grupların parçası olmaması gereken üyeleri var mı?
Periyodik grup onayı, bu soruları yanıtlamanın anahtarıdır. Grup sahiplerinin bir grubun yapılandırmasının belirli yönlerinin doğru ve güncel olduğunu inceleyip onayladığı, aşağıdakiler dahil olmak üzere, sıfır güven güvenliği uygulamaları zincirdeki bir bloktur.
- Grup Üyeliği – Kullanıcılar ve/veya üye olarak iç içe gruplar doğrulanır. Grubun atanmış izinlerini kullanan mevcut kullanıcı grubunu temsil ederler.
- Grup İzinleri – Atanan izinler doğrulanır. Grup üyelerinin görevlerini yerine getirmesi gerekenlerle sınırlı olmalıdır.
- Grup öznitelikleri – Açıklama, e-posta ve sona erme ilkesi gibi bir grubun farklı öznitelikleri doğrulanır.
- Grup Varlığı – Grubun iş için gerekliliği doğrulanır. Geçerli bir amacı olmayan gruplar silinmeli veya devre dışı bırakılmalıdır.
- GroupID’de yöneticiler, grup sahiplerini, süresi dolan bir grubun özelliklerini ve üyeliğini yenilemeden önce gözden geçirmeye ve doğrulamaya zorlayabilir. Onaylama sırasında, üyeler grup üyeliğinden anında çıkarılabilir veya belirli bir gün sonra devre dışı bırakılabilir ve ardından çıkarılabilir.
Grup izinlerini doğrulamayı basitleştirin:
Verilerinizi korumak için önce nerede olduğunu, ona kimin erişimi olduğunu ve erişime nasıl izin verildiğini anlamalısınız. Bu bilgi olmadan sıfır güven güvenliği bir rüya olarak kalabilir.
- Active Directory yetki yönetimi, dosya sunucuları ve diğer kaynaklar gibi verilere erişimi verimli bir şekilde yönetmenize yardımcı olabilir.
- Ayrıca, dahili kullanıcılar ve bu kaynaklara erişmesi gereken kuruluşunuzun dışındaki kullanıcılar için SharePoint ortamlarında size yardımcı olur.
GroupID Yetkileri, bu hedefe kolaylıkla ulaşmanızı sağlar. Şunlar için kullanın:
- Etki alanına katılmış dosya paylaşımlarından ‘dosya paylaşımlarını’ keşfedin.
- Her klasör ve dosyadaki izinleri analiz edin.
- Devralmadan gelen basamaklı yetkilerle ilgili raporları görüntüleyin.
- Kaynak yetkilendirme görünümünden ve kaynakların yetkili kullanıcı görünümünden perspektif gösteren detaya inme raporlarındaki verilerle etkileşim kurun.
- Bu iç görü düzeyiyle, sıfır güven güvenlik modeli uygulamak kolaydır. Hassas verilere erişimin özel olmasını sağlayabilirsiniz.
- İzinler, bir rol veya işlevi gerçekleştirmek için mümkün olan en düşük değerdir.
Kullanımı daha kolay güvenlik seçenekleri:
Konu gerçekten sıfır güvenliğe sahip bir güvenlik modeli olduğunda GroupID’nin sunabileceği daha çok şey var.
- GroupID, yetim grupları tanımlayabilir ve her grubun bir sahibi olmasını sağlayabilir. Birden fazla sahip ve grup onayı desteği ile GroupID, yabancı üyelere sahip olmayan grupları destekler.
- Active Directory, Azure AD ve Office 365 grupları geçici üyeler içerebilir, böylece geçici erişime ihtiyaç duyan kullanıcılar, ihtiyaç bittiğinde gruptan otomatik olarak çıkarılır.
- Gruplar için son kullanma tarihleri belirleyerek fiziksel kaynaklara ve bilgi varlıklarına erişimi sınırlandırılabilir.
Sonuç:
Kurumlar kendileri için her zaman en güvenli yolları ve en güvenli mimarileri ister. Bizlerin de inancı tam da bu yönde küçük büyük demeden her kurumun her şeyin en iyisini, istedikleri gibi elde etmeleri yönündedir. AD vb. ortamlar için sürekli güvenliğini denetlemek, yazdığınız kuralları sürekli incelemek ve bu kuralların güncel kalabilmesi kritik bir konudur. ‘T’ anında yapılan pentestler size o anın bir ekran görüntüsünü verecektir. Oysa bunu sürekli otomatize hale getirip denetlemek, kurumunuzdaki bu tarz yapıların güvenliği konusunda sizleri güncel tutacak ve koruma sağlayacaktır.
[vc_row][vc_column][vc_cta h2=”” add_button=”bottom” btn_title=”Teklif Talep Edin” btn_style=”flat” btn_shape=”square” btn_color=”danger” css_animation=”fadeInLeft” btn_link=”url:https%3A%2F%2Fcyberartspro.com%2Fteklif-isteme-formu%2F||target:%20_blank|”]Siber Güvenlik, Dijital Dönüşüm, MSSP, Sızma Testi, KVKK, GDPR, ISO 27001, ISO 27701 ve DDO Bilgi ve İletişim Güvenliği Rehberi başlıklarıyla ilgili teklif almak için lütfen tıklayın.[/vc_cta][/vc_column][/vc_row]