Cyber threat actors began to carry out serious destructive attacks day by day. The importance of cyber security has increased, especially when states and companies have become aware of the damage they have suffered as a result of cyber attacks. Cyber security researchers are working on various models in order to analyze cyber attacks, that is, they use various models to think like an attacker to eliminate the incoming attack or to analyze the actual attack. Finding the reason behind the cyber attackers' actions is crucial to understanding what the attacker is up to and what we need to protect against the enemy. One of the models used to make sense of the cyber attack is the Cyber Kill Chain attack methodology.
Cyber Kill Chain was developed by Locheed Martin. In military terms, "Kill Chain" is a model that defines the stages of an attack and uses various methods to carry out/prevent this attack and is adapted to cyber security.
According to the Cyber Kill Chain attack methodology, a targeted cyber attack takes place in 7 stages. It aims to model the entire process from the discovery phase of the cyber threat actors' target system to the cyber attacker's achievement of his goal.
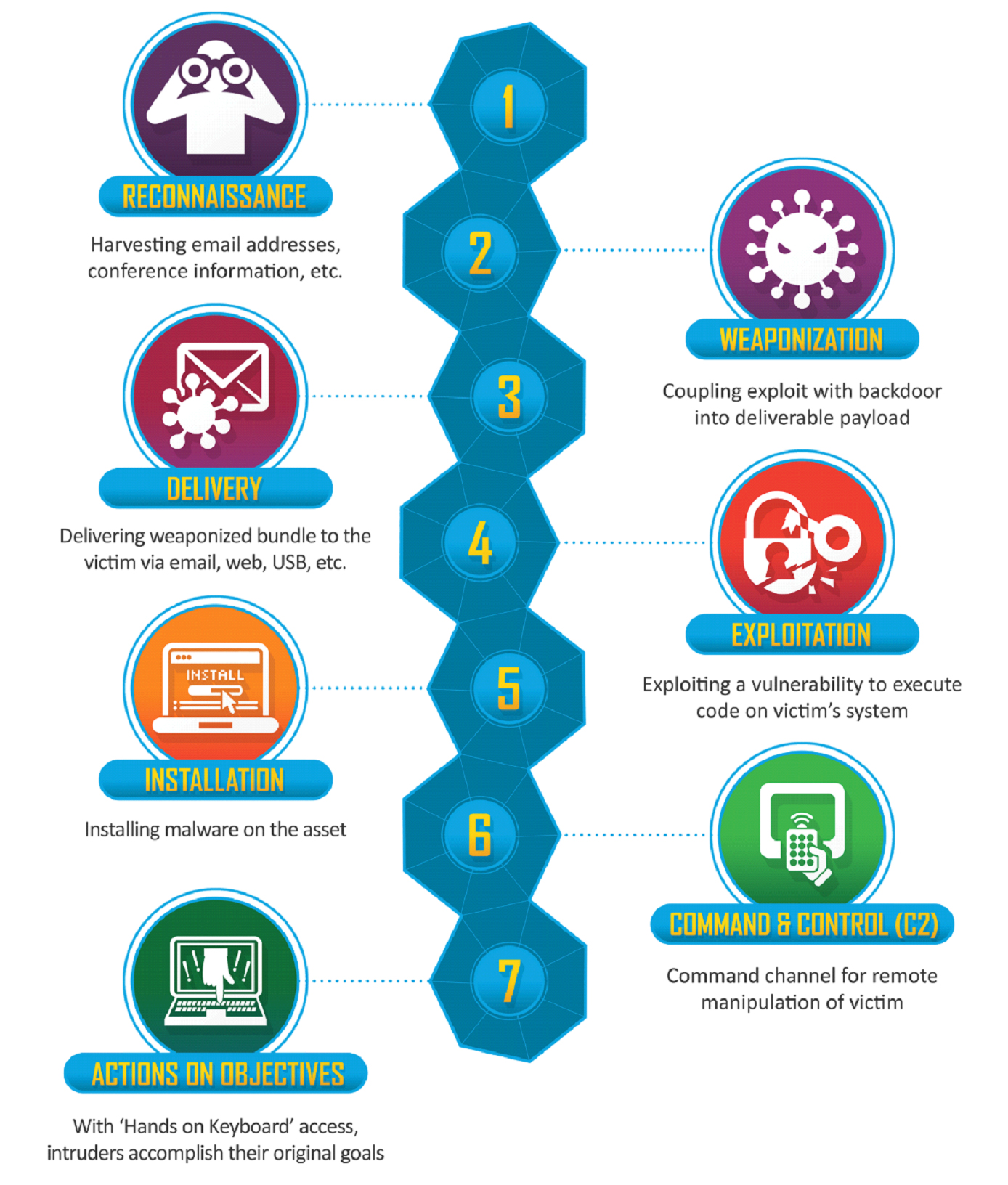
⦁ Discovery (Reconnaissance):
This is the attacker's stage of gathering information on the target system. The purpose of this stage is to determine the method of infiltration into the system. The attacker detects the IP addresses of the target system, employee information, and the security systems used. The attacker's main goal is to look for vulnerabilities that they can exploit.
Attackers include whois queries, shodan, social media platforms, forum sites, network mapping, recon-ng, theHarvester, archieve.org, nmap, dmitry. It uses various methods such as using social engineering attack methods, open source intelligence (OSINT), creating websites containing malware, and detecting existing Zeroday vulnerabilities.
⦁ Weaponization:
At the discovery stage, the attacker, who obtains the necessary information about the target system and determines the entry point to infiltrate the system, decides which attack vector to use at this entry point. It is the stage where the attacker completes his final preparations before the attack. Malware that should be used at the same time is created here.
Attackers create malicious files such as .pdf, .doc, .xls, which contain malicious software, files that can extract information (Invoice, personnel list, credit card statement), exploits after detecting points that can exploit zeroday vulnerabilities.
⦁ Delivery:
This is the stage where the prepared malicious activity is transmitted to the target system. The transmission method is determined at this stage. At this stage, the attacker transmits the malware to the target via an e-mail, usb, etc. Here the attacker performs the phishing attack. Here, it targets the person who is the weak link of cyber security and makes the attack through him.
⦁ Exploitation:
This is the stage where the attacker exploits the security vulnerability of the target system by using the weapon created in the 2nd stage. The purpose here is for the malware to run on the target system. It can take advantage of existing vulnerabilities such as ShellShock bash vulnerability, Adobe Acrobat vulnerabilities, Microsoft Office vulnerabilities, or the attacker can exploit the system with malwares that are infected with the target system after a phishing attack.
⦁ Installation:
After the exploitation of the target system is successful, the attacker begins to perform malicious activities. The attacker, who has successfully settled on the system, uses various techniques at this stage to hide and can also install different software to ensure persistence on the system. At this stage, the attacker can successfully control the system.
⦁ Command & Control (command & control, c2):
It is the stage where the target system is controlled remotely. The attacker has taken over the target system. Malicious codes are embedded in the network. At this stage, after capturing the target system, it performs activities on the targeted system and creates a communication channel in the target system.
⦁ Actions On Objectives:
The attacker takes various actions to achieve his goal. These actions can be exemplified as stealing data, deleting or attacking another system. After performing the above steps, the attacker takes action in this step.
These 7 stages are interconnected like a chain. Success at each stage will affect the next stage.
Recommendations of CyberArts Information Security Team
In order to take precautions against cyber attacks, it is necessary to know the attack methodologies well. Thanks to models such as Cyber Kill Chain, missing points in the IT infrastructure of the institutions can be detected, the intervention method can be decided according to the attack stage at the time of the attack, and a risk analysis can be made after the attack to what extent the institution is affected by this attack.
Questions you should ask in your own internal structure;
⦁ Are existing systems up to date?
⦁ Do you know all the software running on the systems?
⦁ Has a current threat assessment been done?
⦁ Do you know your weak points in terms of security?
⦁ Have you planned to close these weaknesses?
⦁ Is the action planned in case of a potential security breach?
⦁ Does he/she have security awareness?
⦁ Can employees understand social engineering attacks or phishing attacks?
⦁ Blocked access to known malicious websites?
⦁ Is the firewall configured well?
⦁ Are safety devices well-monitored?
⦁ Is data backed up?
⦁ Is there a backup system when the system is down?
⦁ Do you have a cyber incident response plan?
Source:
lockheedmartin.com
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












