Zero Trust Network Access emerges as a new area of cybersecurity that replaces cybersecurity measures that have now become standard and are easier for attackers to circumvent.
Zero Trust Network Access allows users to seamlessly and securely connect to applications used in-house without ever gaining network access or exposing applications to the internet. Unlike network-centric solutions such as VPNs and firewalls, Zero Trust Network Access takes a fundamentally different approach, securing access to applications within the enterprise. They often replace traditional technologies such as VPNs and offer various authentication methods to protect the identity and context of users accessing corporate applications.
First of all, with Zero Trust Network Access, users are isolated from network access in the institution and applications are isolated from the internet. This situation; It minimizes the risks that compromised devices may pose on the corporate network. Basically, instead of connecting to the corporate network and opening to the internet, only the applications used are allowed to communicate with each other in an isolated environment.
Many third-party users have extremely privileged access with these applications, which creates a security vulnerability for the organization. Zero Trust Network Access significantly reduces third-party risk by ensuring that external users never access the corporate network and only authorized users can access permitted applications.
For example; There are data that you share with third parties or business partners and many applications that you use to transmit this data. Even if you have taken all the necessary cyber security measures within the institution, it is not possible to control the network and devices from the other party. Because Zero Trust Network Access technologies create this communication in a completely isolated environment; It makes it possible for you not to be harmed by such vulnerabilities, to be protected from possible attacks and not to experience a data breach.
With Zero Trust Network Access, not only third party vulnerabilities are contained. You make only "outgoing" connections, which makes the network and application infrastructure invisible to unauthorized users. IPs are not exposed to the internet, creating a "dark web" that makes it impossible to find the network. It is known that it is not possible to attack something that you cannot see.
The native application segmentation of Zero Trust Network Access allows one-to-one application access once users are authorized. With detailed application access policies, only applications are accessed instead of providing full access to the corporate network. In addition, full control of user activities can be audited in real time.
Today's dynamic business environment; mobile workforce needs suppliers/vendors and contracted parties that can access corporate resources and systems. It is clear that ZTNA technologies will be one of the core technologies in cyber security solutions of the near future for “zero secure” access to these resources without providing network access or exposing them to the internet. With this technology, Gartner's predictions are as follows:
- 80% of the applications opened to business partners in 2022 will be accessible through ZTNA.
- In 2023, 60% of large companies will start to prefer ZTNA over VPN in their new investments.
How Does ZTNA Work?
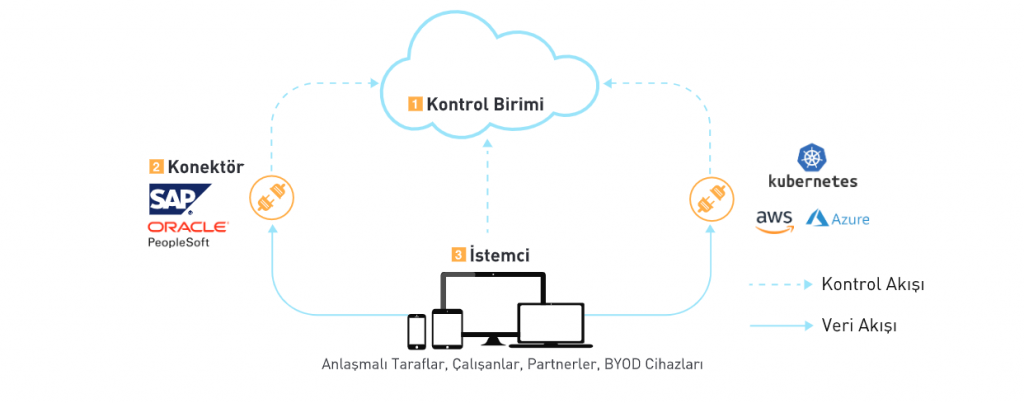
- Controller: The component that controls, allows and regulates connections. Zero Trust Network Access is delivered as a service in the cloud (SaaS)
- Connector: Connectors are located in front of the applications to be accessed, usually in a cloud environment or on-premises data centers.
- Client: Users install Zero Trust Network Access Solution clients on their devices to access corporate resources and applications.
When an authenticated user requests access to a “remote enterprise resource” (corporate application, server, etc.), a temporary application network is created on the user's device and on the enterprise resource. Users can only access the resources and applications for which they are authorized through this temporary network. The connectors are never exposed to the internet, they only have an outgoing connection and are behind a firewall or other security component. A peer-to-peer tunnel is established between the application on the user's device and the connector on the corporate network, with no data traffic passing through third-party cloud gateways.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












