Hello, in this article, we will talk about CloudCyte technology and features of CyberCyte company.
 About CloudCyte
About CloudCyte
CloudCyte is an MDR platform for threat hunting and asset attack surface management to identify cyber risks more quickly and easily through a zero trust model. The system provides a unified risk scoring framework for assets, information, and forensic artifacts
The platform also monitors every communication for complete protection from end users, data centers, cloud platforms, email applications and OT devices to block any unverified communication attempts or devices within the network.
Product Review
CyberCyte Dashboard
Asset Management
We can examine the status of the endpoints where the agent is installed on the Dashboard screen. We see that the collected artifacts are categorized in this area according to the degree of risk. We can say that there are some risk levels such as Malicious, Critical, High Risk, Medium Risk, Low Risk. The main dashboard consists of 3 sub-headings in itself; Asset Analysis, Windows Asset Analysis, IT Overview.
It is observed that the collected artifacts are categorized in each of the 3 dashboard titles and the collected artifacts are also given graphically. Graphically, some of the data are Processes by Name, Processes by Company, Processes by Command Line. We can say that findings such as the name of the running process, the area to which the process is connected and the way the process is running are detected.
Device Management
In this section, we can learn the information about the devices we analyze and see the devices listed under the group, allowed devices and blocked devices.
For example; Date first added, computer name, IP Address, operating system, etc.
Asset Analysis
In this section, as a result of the analysis made for the devices, we move on to the ability to examine the general risk score of the devices and the risk category according to the analysis.
Network Device Management:
In the Network Management module, we can perform the settings and control of the devices on the network. The modules included are shown in the image below
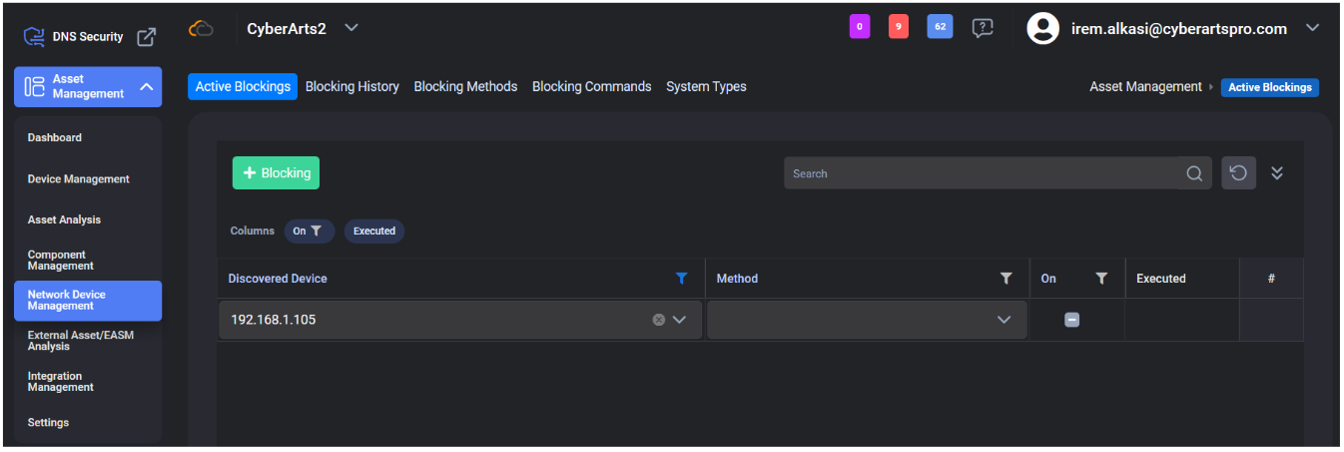
Active Blockings: Here you can activate the option of blocking suspicious devices or an IP address that we see as a risk.
Blocking History: You can also see the blocking operations we have done before, and you can include the ones you want to change or add later, among these operations.

Blocking Methods: In this section, you have the option to specify a method for the blocking process. With this module, you can take advantage of the methods that come automatically in the system or you can specify your own method.
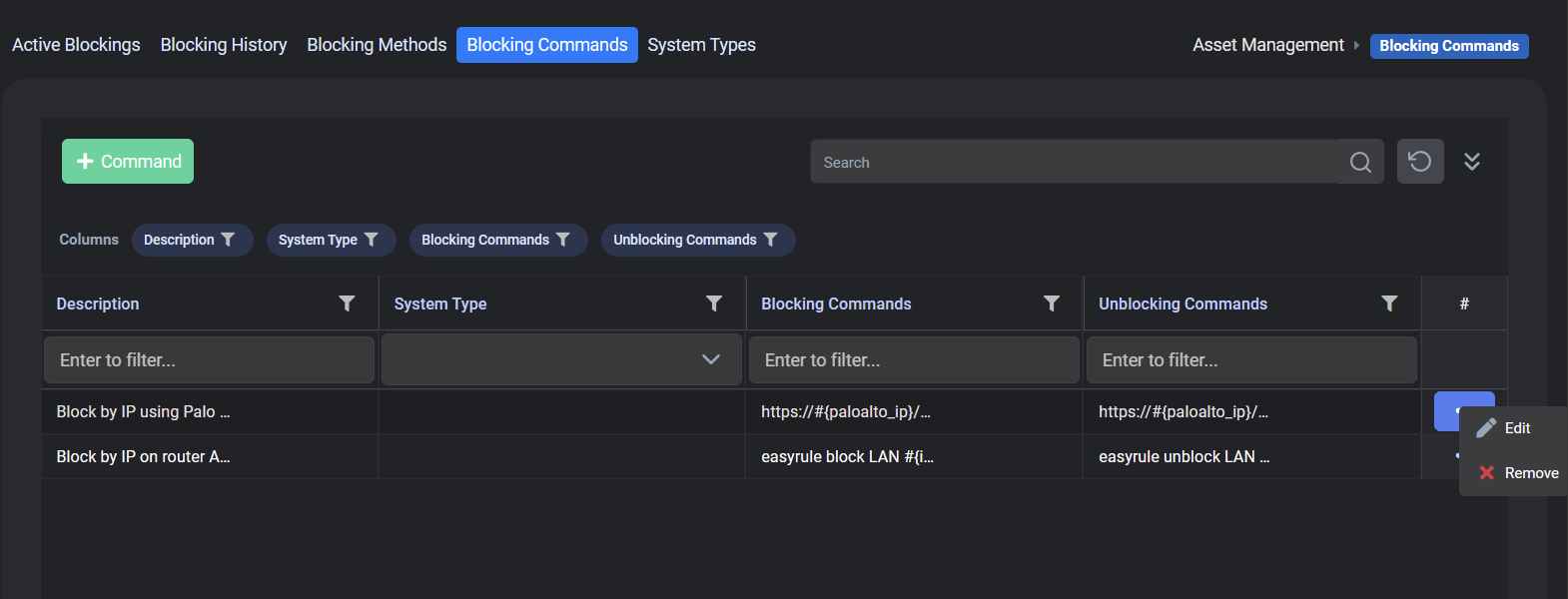
Blocking Commands: In this option, you can also take advantage of the commands that come automatically in the system. For example, you have the option to write a rule for a network transaction that you want Palo Alto to block. If we Support he example with a visual;

Threat Hunter
Threat Analysis
On Windows systems; Autorun analysis, process analysis, Macro file analysis, event log analysis, sysmon analysis, security software analysis, application analysis, firewall analysis, antivirus software analysis, network adapter analysis, port listening, file analysis, Thor analysis, network traffic analysis, DNS traffic provides analysis.
Linux sistemlerde; Users, crontabs, commond history, authentication logs, syslog messages provides analysis.
CloudCyte Threat Hunter module; It allows us to see the captured evidence in detail and shows the risk score. As seen below; Besides the evidence it brings, it offers us some options. The options we use most often are Actions and Virus Total.
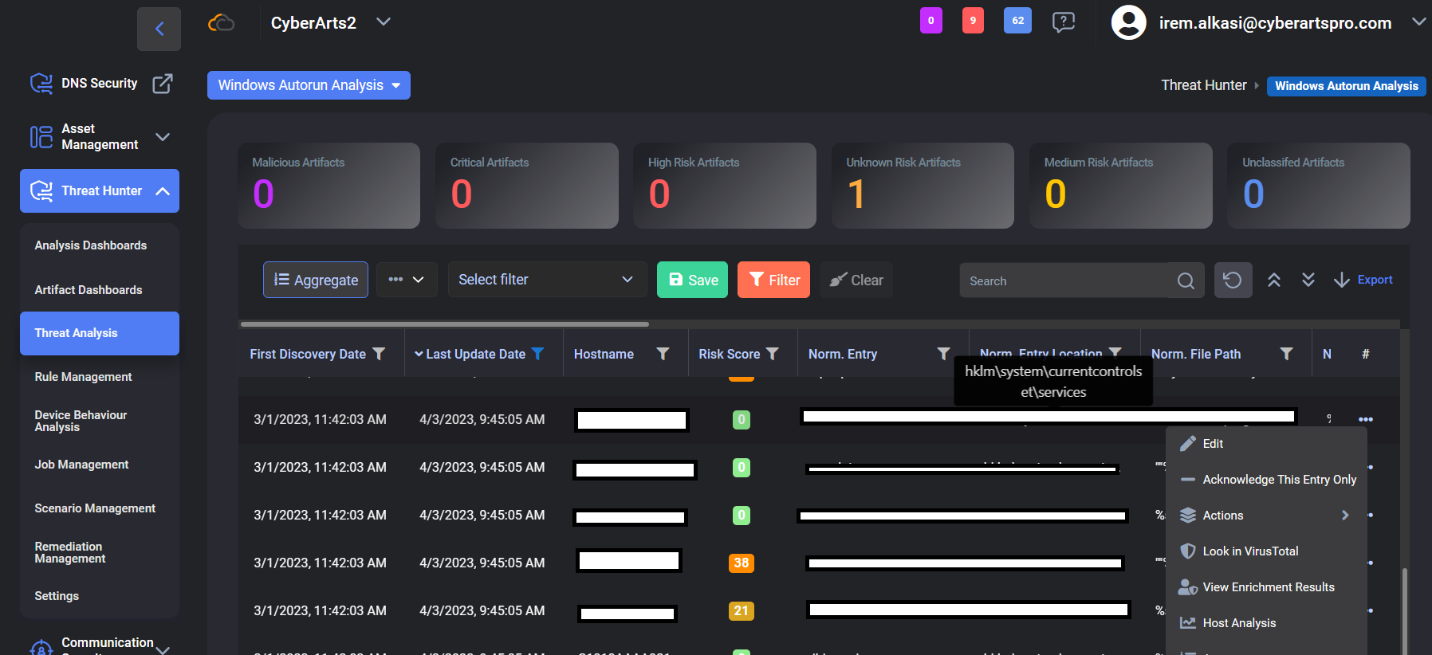
Incidentally, we would like to point out that the product can integrate with solutions such as AlienVault, Thor, Virus Total and Sophos.
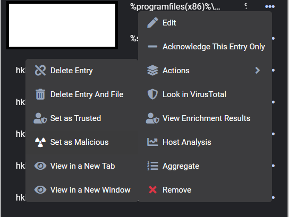 We have the authority to react faster with Actions. After doing some research on the result, we can perform the labeling operations. (Ex: Labeling as harmful or safe.)
We have the authority to react faster with Actions. After doing some research on the result, we can perform the labeling operations. (Ex: Labeling as harmful or safe.)
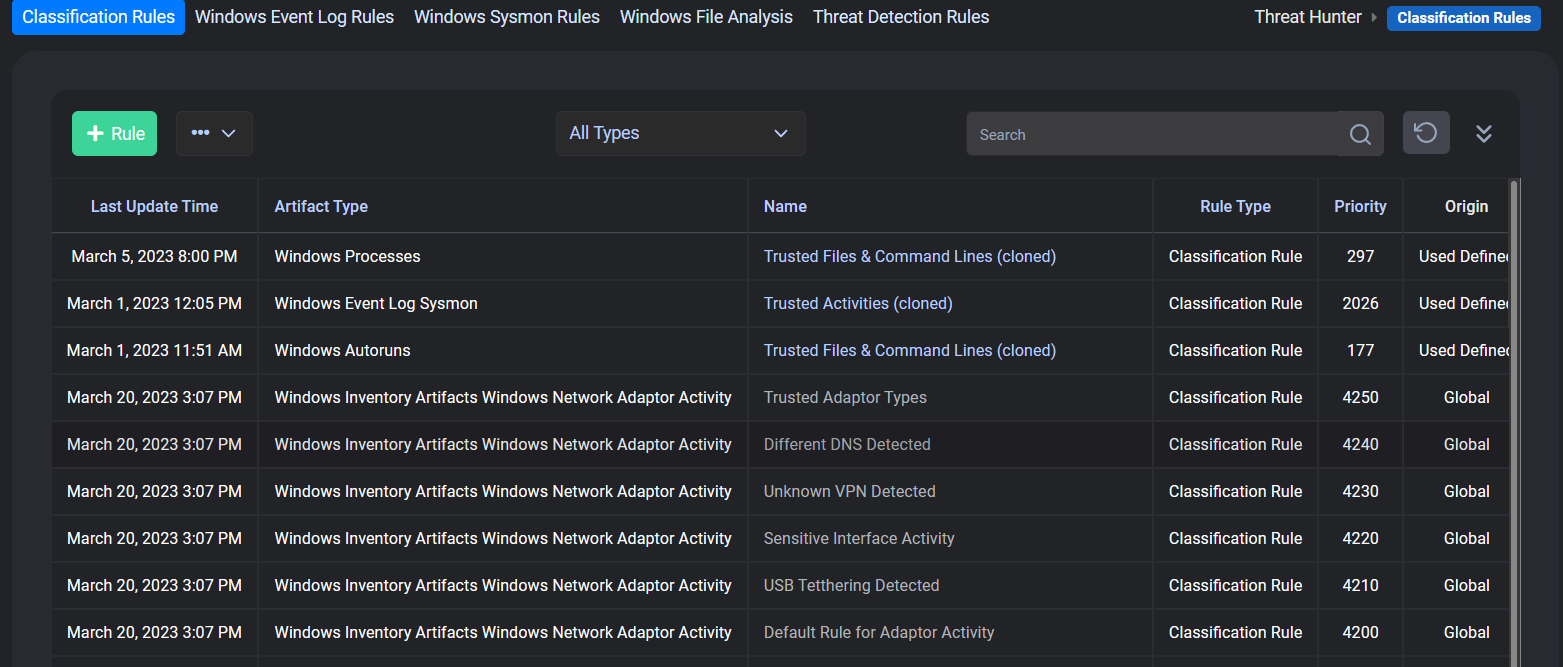
Rule Management
Under this feature, we are offered; It allows you to write and run rules (YARA&SIGMA) for various fields on endpoints. CloudCyte automatically brings, you have the option to add and run rules. Below is a list of rules for which fields you can write.
- Classificaiton Rules
- Windows Event Log Rules
- Windows Sysmon Rules
- Windows File Analysis
- Threat Detection Rules
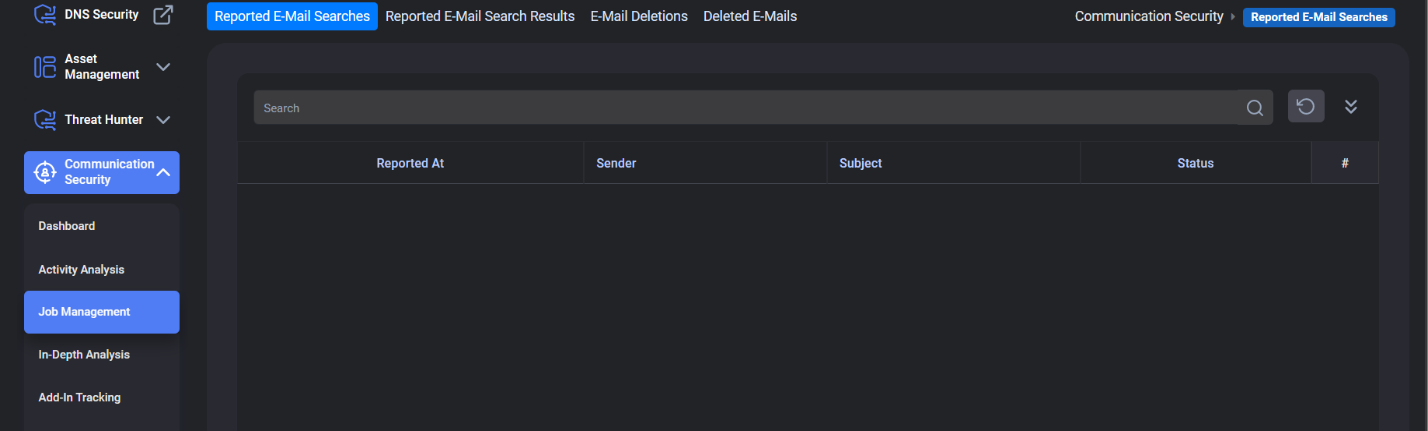
Communication Security
The most important feature that draws our attention in this module is its focus on e-mail security.
The module is a GDPR compliant email phishing detection and inbox security solution. The system allows organizations to identify and delete malicious email and Microsoft Teams communication, bypassing security checks.
Users can report emails they suspect are suspicious. The platform provides unmatched visibility for malicious emails reaching end users. When an email is identified as malicious, the system may initiate an investigation. The search process ensures that risky emails are found without requiring mailbox access. When an email is identified as malicious, the email can be deleted from all user mailboxes.
The relevant interface is as follows. You can go from the sub-properties to the above properties.
Policy Management
In this module, an interface is offered to us to perform operations such as security settings, standard configurations and application distribution in line with needs. CloudCyte has a few rules ready as in its other modules, but you have the option to create new rules for your devices according to your needs and requests.
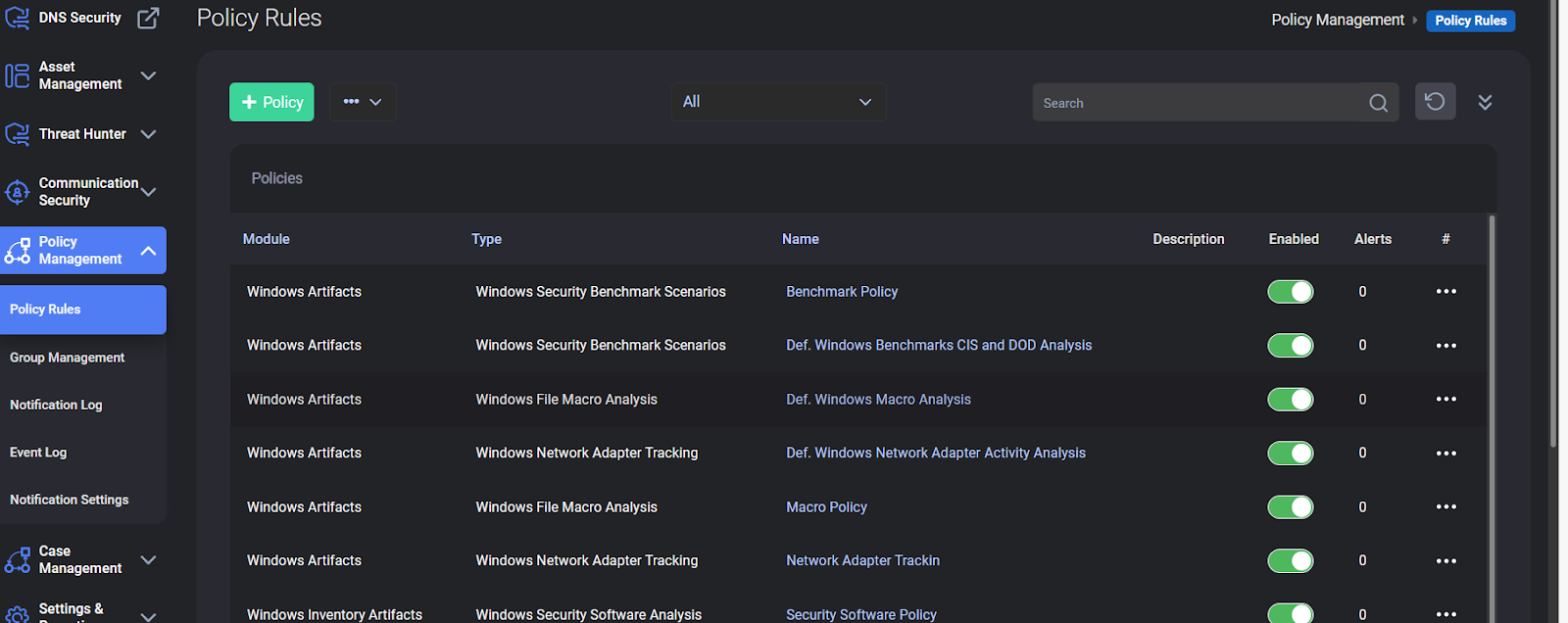
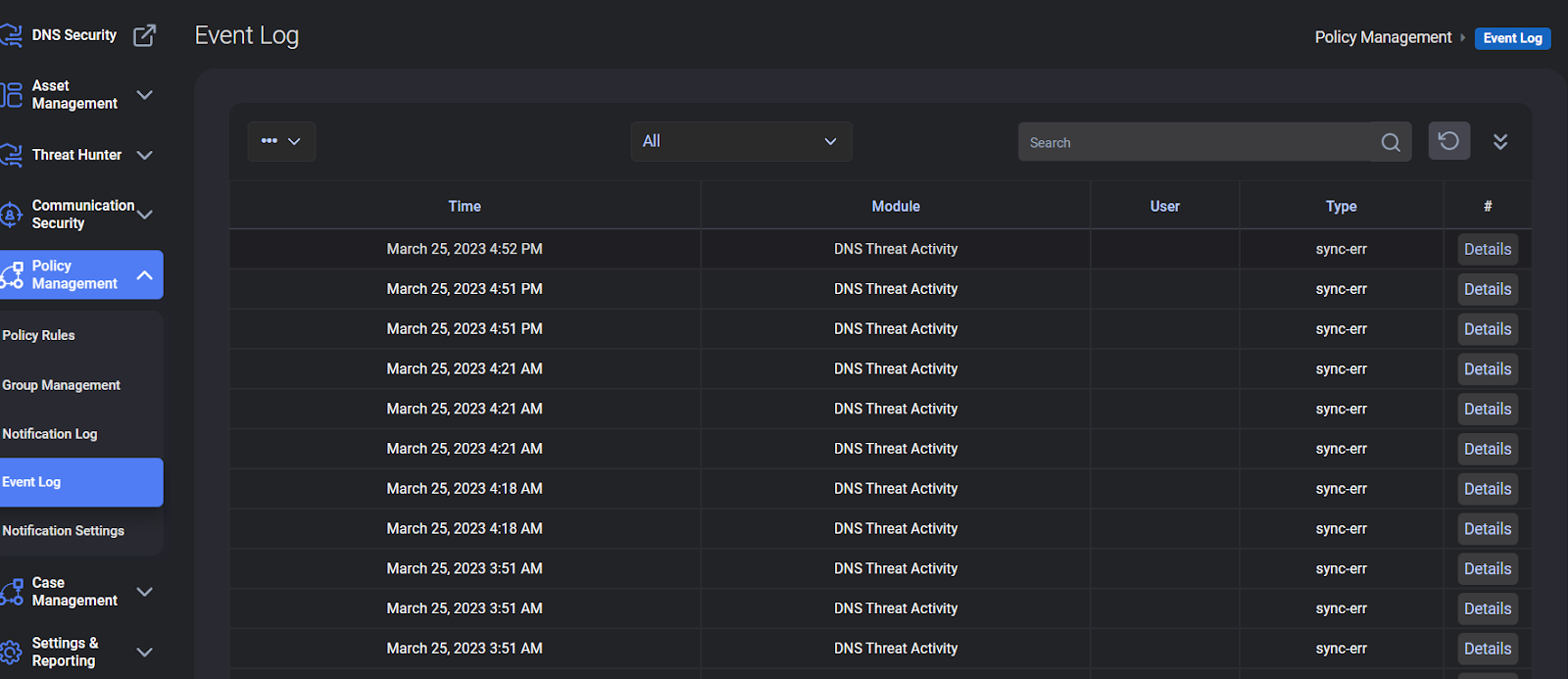
Under this module; You encounter the subheadings of Group Management, Notification Log, Event Log, Notification Settings.
It should not be overlooked in this section that CloudCyte is more of an MDR solution than incident response.
Case Management
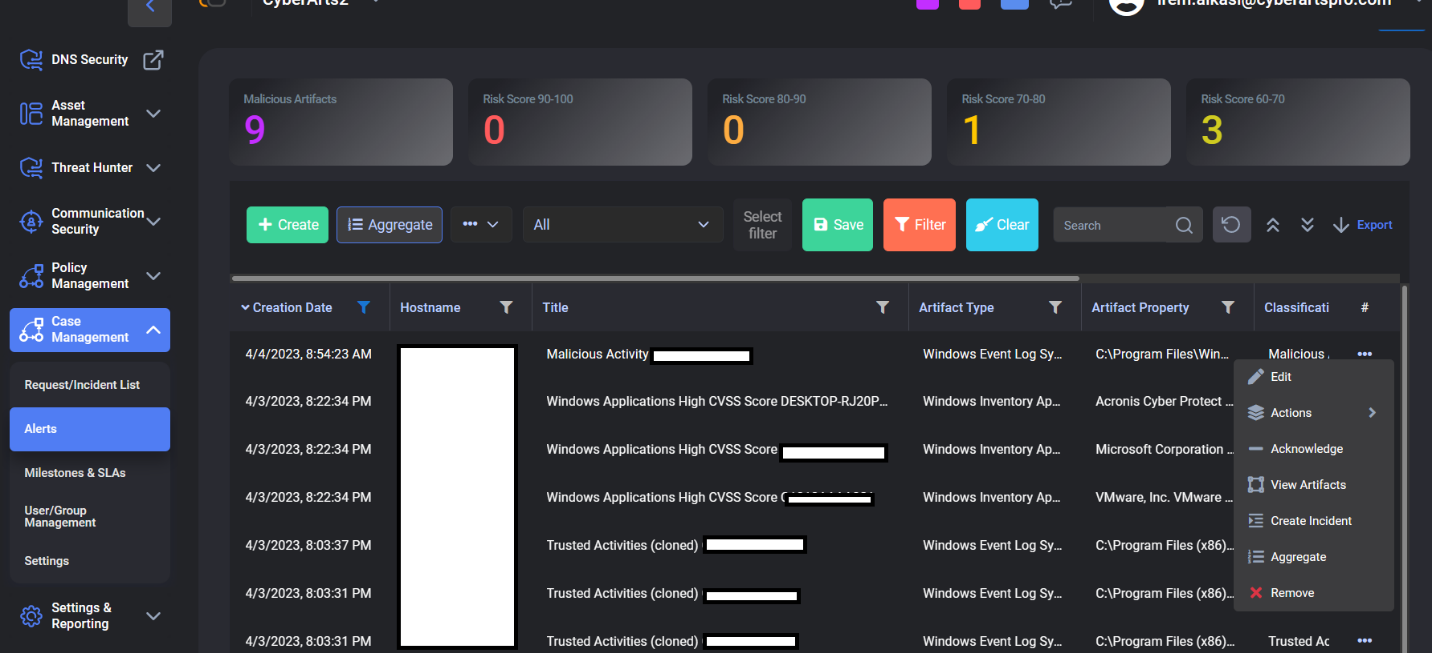
Case Management area is one of the most important modules of our technology. You can see the alarms given in this section in detail with a user-friendly interface, so you can get a quick reaction. As a result of our tests, we observed that when we encounter a harmful activity, the warnings drop in a healthy way and give the right alarms.
The scenario we followed at this point: We ran a file that we knew was malicious in the test machine where the CloudCyte agent was installed.
We have observed that the file is tagged as malicous by CloudCyte, although it does not give warnings or is not understood by most technologies.
Settings and Reporting
In this module, there is content that allows us to get a report as a result of the analysis. It is aimed to analyze the results better and to use the time effectively by automating the report process.
We have concluded our technology review with this area. We tried to convey to you the relevant modules and purposes of technology in a short and concise manner.
In the last part of our article, we would like to remind you that the product is an MDR technology, if you want to learn more about MDR technology or see its difference with other technologies here you can reach our article of interest 😊
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












