Cybersecurity researchers at the Swiss Technical School Zurich recently identified a critical vulnerability that allows any threat actor to circumvent PIN codes on Mastercard and Maestro contactless cards.
This vulnerability allows contactless payments without entering any PIN code. Thus, contactless payments can be made with stolen Mastercard and Maestro cards.
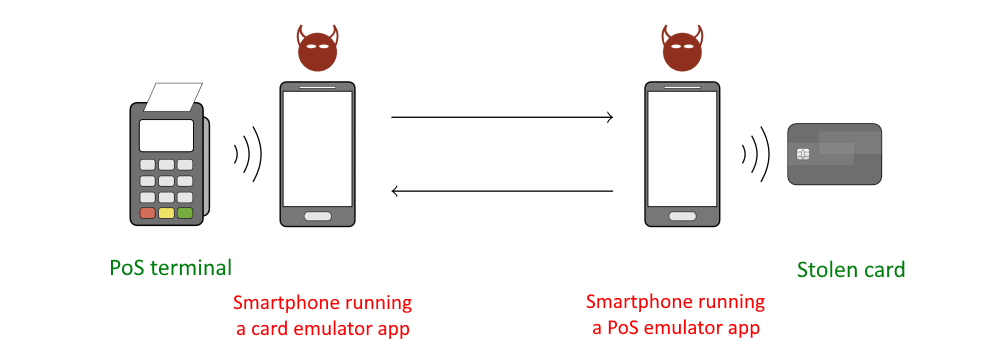
To exploit the vulnerability, researchers have discovered that the PIN can be circumvented as a result of a MITM (man-in-the-middle) attack between a stolen card and a Point of Sale (PoS) terminal. With this attack, in order to make payments from Mastercard and Maestro cards;
- Two Android smartphones
- A custom Android app (to implement MITM)
- Credit card information
How was the vulnerability exploited?
Performed using two Android smartphones (required to be capable of supporting NFC and running Android 4.4 KitKat or later) connected via a relay channel created using TCP/IP server-client communication over WiFi. While the first phone runs an application in POS Emulator mode, the second phone runs the application developed by the researchers in Card Emulator mode. must support. The man-in-the-middle function works on the POS emulator device, while the card emulator acts as a proxy for the relay channel.
The attack scenario is actually simple. Once the attackers place the PoS emulator next to the card to direct the card to initiate a transaction and capture the transaction details, the card emulator can be used to provide this information to a real-life PoS with the modified transaction details.
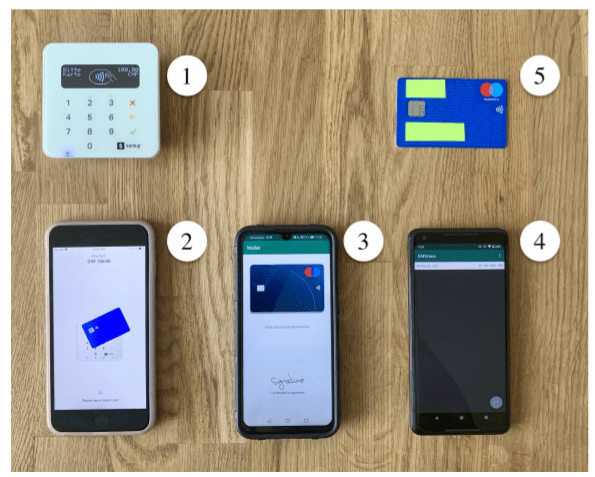
Researchers successfully tested an attack on Visa Credit, Visa Debit, Visa Electron and V Pay cards, with payment transactions over the limit required for Swiss banks to require a PIN.
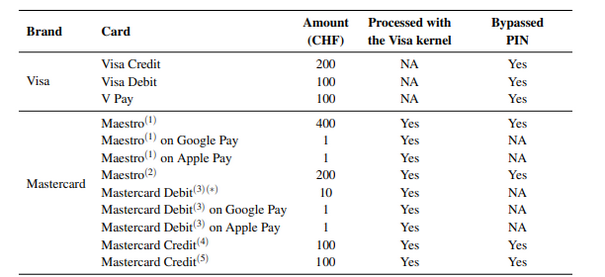
As we can see in the weakness here, every technology that has reached the public must be subjected to penetration tests from multiple perspectives over and over, and if necessary, it is necessary to outsource services other than internal security employees.
Dear visitor, This blog post is for information purposes and has been prepared with the aim of raising awareness against attacks and taking measures in this direction. We remind you that it is not legal to use the attack methods mentioned in this article for purposes other than their intended purpose, and we declare that CyberArts is not responsible for any errors, omissions or malfunctions that may arise due to this situation, and cannot be held responsible for direct or indirect damages and losses that may arise from them.
Regards,
CyberArts Informatics Incorporated Company
Source:
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












