Cybersecurity firm Check Point Research, which disclosed the problem to the Facebook-owned platform on November 10, 2020, said that it was able to crash WhatsApp by switching between various filters on malicious GIF files.
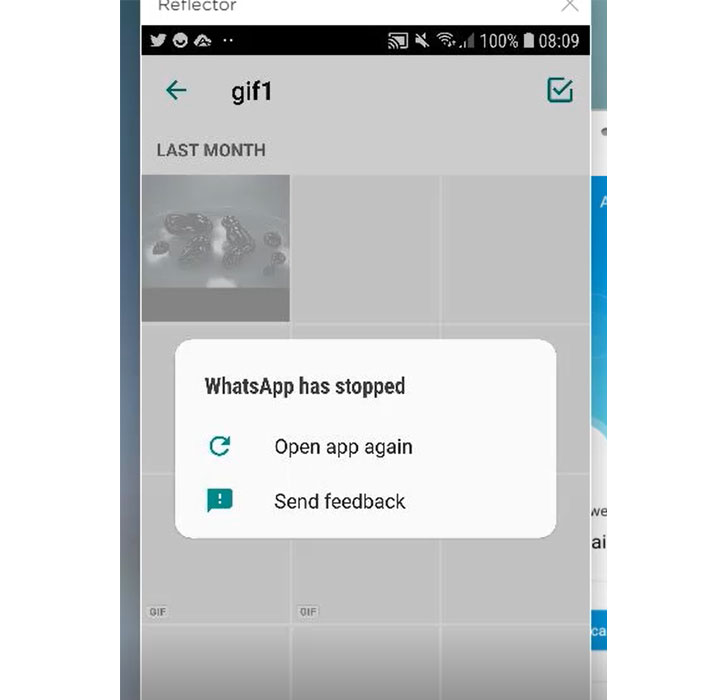
The issue was specifically caused by an "applyFilterIntoBuffer()" function that handles image filters, applying the user-selected filter that retrieves the image from the source and copying the result to the target buffer. By reverse-engineering the library “libwhatsapp.so”, the researchers found that the vulnerable function relies on the assumption that both the source and filtered images have the same dimensions and the same RGBA color format.
Given that each RGBA pixel is stored as 4 bytes, a malicious image with only 1 byte per pixel could be used to gain an out-of-bounds memory access, as the function tries to read and copy 4 times the allocated resource.
WhatsApp said there was "no indication that users are currently affected by this bug". Since WhatsApp 2.21.1.13, the company has added two new controls to the source image and filter image, which ensure that both source and filter images are in RGBA format and the image is 4 bytes per pixel to prevent unauthorized reads.
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












