What is a Cyber Threat?
To put it at a basic level, the actions taken by malicious people with the aim of causing harm are called cyber threats.
Who can be exposed to Cyber Threat?
Hackers, terrorists, commercial competitors, spies, governments and intelligence agencies, unhappy employees, organized crime groups.
What types of attacks can we be exposed to?
Malware; They are malicious software.
Spyware; They are spyware.
Phishing; They are phishing attacks.
Ransomware; They are ransomware.
Trojan; It is malicious software that provides remote access to the computer. (Trojan horse)
Man in the Middle (MiTM); Man-in-the-Middle attacks.
Botnet; Attacks made on compromised (zombie) computers are generally used for DDoS purposes.
Malvertising; They are malicious software embedded in advertisements.
Wiper Attacks; They are malicious software that irreversibly deletes everything on the infected system.
Distributed Denial of Service (DDoS); They are denial-of-service attacks.
DataBreaches; They are data leaks.
Worm; They are worms.
Keylogger; Malware that Logs keyboard actions.
Backdoor; It is backdoor software that allows you to (silently) access the system again.
Advanced Persistent Threats; They are targeted attacks.
How Do We Protect Against These Attacks?
The cyber security world realized in the early 2010s that conventional cyber security solutions such as firewall, antivirus and DLP products are not sufficient to combat cyber threats. Because these solutions were ‘reactive’ tools that could only take charge when an attack was launched.
This approach was not enough and ‘proactive’ prevention mechanisms were needed that could provide advance information about attacks. This need led to the emergence of the field we call cyber intelligence.
We can define cyber intelligence as different solutions and tools that pre-analyze the cyber threat factors that may become a risk for an institution and provide the institution with the opportunity to take warning and precautions in this direction.
Thanks to this information given beforehand, institutions; they become more prepared by increasing their level of knowledge about the threats that may target them, the methods they use, and the risky targets in their organizations.
What is Cyber Intelligence?
Cyber intelligencez is the collection and discovery of threats that can harm business elements and security of institutions and organizations at any level, from electronic media.
It is a type of intelligence that allows early measures to be taken by detecting the aims, methods or attack types of the attackers as a result of analyzing the data collected and enriched from electronic media through a process.
Cyber threat intelligence is divided into groups according to their level. These;
Strategic Intelligence: It is the type of intelligence aimed at recognizing the enemy. It is formed as a result of monitoring institutions, organizations, individuals and groups that have the potential to cause harm. It contains information about the attackers’ intentions, motivations, tactics and strategies, past actions and possible attacks.
Operational Intelligence: This type of intelligence includes the techniques, tactics and procedures of the attackers. This information is served to the teams providing the SOC (Security Operation Center) service and can be analyzed by them and used as a precaution against possible attacks.
Tactical Intelligence: This type of intelligence includes data that identifies potential malicious activity on the system and network. These data, called IoC (Indicators of Compromise), are unusual and suspicious movement data in their structure. Tactical intelligence is integrated into security solutions such as SIEM, Firewall, IDP/IPS, DLP, Anti-Spam, Endpoint Protection.
Open Source Coded Cyber Intelligence Solutions
MISP; It is a threat intelligence platform to share, store and correlate reconciliation indicators of targeted attacks, threat intelligence, financial fraud information, vulnerability information and even counter-terrorism information..
At the same time, IoCs and information are used to detect and prevent attacks, frauds or threats against ICT infrastructures, organizations or individuals.
It is a free and open source project that helps share cyber threat intelligence.
 Cuckoo Sandbox; You can throw it at it planned in a plan and you will plan a few minutes Cuckoo about a plan outlining that you will plan a plan(test) in the plan of the file. What can you do in the Cuckoo Sandbox?
Cuckoo Sandbox; You can throw it at it planned in a plan and you will plan a few minutes Cuckoo about a plan outlining that you will plan a plan(test) in the plan of the file. What can you do in the Cuckoo Sandbox?
- Detects many different malicious people (executable files, office documents, pdf analysis files, etc.) and malicious websites etc in Windows, Linux virtualized environments.
- Parse the API calls and the overall state of the file into high information and scores by the followers.
- Offload and analyze the gateway even if it is encrypted with SSL/TLS. Forwarding local routing to forward or forward all remediation or InetS.
- Perform a detailed inspection of the vehicle in the virtual environment using YARA, through Volatility, and in a detailed preparation phase.
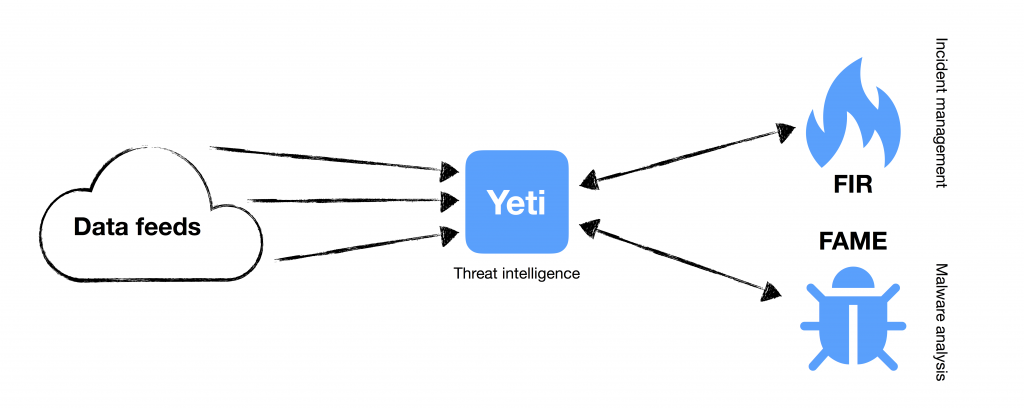
YETI; The ideal world of the Yeti is a world where all its features are used well. This includes data-driven features such as feeds, analytics, and exports, but also provides higher-level information such as identifying TTPs and connecting them to different actors. FAME and FIR, offered by the CERT Société Générale team, have features that allow them to work closely with Yeti, both transmitting and attracting information.In addition to being an extensible event management platform,
FIRparses all observables found in an event’s description or comments and displays any matches and sends them to Yeti to see what it knows about them. On the other hand, unrecognized observables can be pushed to the Yeti and tagged.
FAME, is also closely integrated with Yeti. Whenever observables are extracted from a sample (via one of FAME’s many modules), they are matched with what Yeti knows, and the results are displayed on the FAME analysis results page. Unknown observables can, once again, be tagged and forwarded to Yeti so it can be quickly associated with other submitted instances.
This is probably one of the best ways to set up Yeti in your daily incident response workflow. This setup works particularly well in teams with rotations specific to each task (threat intelligence, incident management, malware analysis, etc.).
What is the Collective Intelligence Framework?;
Yeti is one of many recently released tools aimed at facilitating threat intelligence management. There is a very wide combination of tools that allow you to compile and enrich the feed data and get results.
Yeti is very flexible in this regard and can easily connect to your existing ecosystem as it has both feeding and exporting capabilities. Yeti complements other already existing systems and will give you a different approach to the analysis of your data and the intelligence you can perform on it.
It is worth noting that the Yeti was designed with modularity in mind. Creating new feeds, analytics and exports is pretty easy. Yeti's full system is also available via the HTTP API, so interacting with it from other tools or even from the command line is pretty straightforward. Python contexts to the HTTP API (work in progress) are available in the pyeti repository.
CIF (Collective Intelligence Framework); CIF allows you to combine known malicious threat information from many sources and use that information for identification (incident response), detection (IDS) and mitigation (null route). The most common types of threat intelligence warehoused in CIF are IP addresses, FQDNs and URLs that are observed to be related to malicious activity.
This framework pulls in various data-observations from any source; create a series of messages “over time” (eg: reputation). When you query for the data, you’ll get back a series of messages chronologically and make decisions much as you would look at an email thread, a series of observations about a particular bad-actor.
CIF helps you to parse, normalize, store, post process, query, share and produce data sets of threat intelligence.
The Process;
Parse, CIF supports ingesting many different sources of data of the same type; for example data sets or “feeds” of malicious domains. Each similar dataset can be marked with different attributes like source and confidence to name a few.
Normalize, Threat intelligence datasets often have subtle differences between them. CIF normalizes these data sets which gives you a predictable experience when leveraging the threat intelligence in other applications or processes.
Post Process, CIF has many post processors that derive additional intelligence from a single piece of threat intelligence. A simple example would be that a domain and an IP address can be derived from a URL ingested into CIF.
Store, CIF uses JSON and ElasticSearch as it’s data store to warehouse billions of records of threat intelligence
Query, CIF can be queried via a web browser, native CLI client or directly using the API.
Share, CIF supports users, groups and api keys. Each threat intelligence record can be tagged to be shared with specific group of users. This allows the sharing of threat intelligence among federations.
Produce CIF, CIF supports creating new data sets from the stored threat intelligence. These data sets can be created by type and confidence. CIF also supports whitelisting during the feed generation process.
ABUSE; It collects and analyzes data about botnet infections from supposedly reliable reporters and provides the data to providers so they can alert their customers in case of an infection.
In addition, the Abuse Information Exchange is a forum where members of the association can share relevant information and information.
Confidential Source Cyber Intelligence Solutions Dark Web What Is Dark Web Threat Intelligence?
Dark Web
What is Dark Web Threat Intelligence?
The dark web is a portion of the internet focused on privacy and anonymity, making it an ideal location for cybercriminals to share tools and information and offer their services for sale. This also makes dark web threat intelligence invaluable for companies as monitoring information posted on the dark web provides an uncensored view into the current cybercrime landscape and trends in cyberattacks.
Implementing a Dark Web Monitoring program allows organizations to integrate dark web intelligence into their cyber risk management process, enabling them to improve their security posture by taking advantage of relevant, timely, and actionable insights.
Finding Threats On The Dark Web
The dark web can be a valuable source of threat intelligence where analysts can learn about the ways that cyberattacks are performed, which attack tools are for sale and being purchased, and the success rates of current cybersecurity campaigns (based on the sales of stolen data).
Threat Information to Look For
Cybercriminals use the dark web to exchange tools, share information, buy and sell data, and for other activities. This makes it a rich source of threat intelligence that organizations can use to predict, identify, and protect themselves against cyber threats. Some types of threat information that analysts can find on the dark web include:
Security vulnerabilities:
Cybercriminals often discuss software vulnerabilities, and proof of concept or ways to exploit the vulnerabilities can be discussed or offered for sale on Dark Web marketplaces.
- Data Access: Data stolen as part of a cyberattack can be offered for sale or discussed in forums on the Dark Web.
- Open Credentials: User credentials exposed through data breaches, credential stuffing, and other attacks are frequently offered for sale on Dark Web marketplaces.
This and other types of information exposed on the Dark Web can enable analysts to assess both the impact and probability of attacks and then defend their organizations appropriately.
Scanning the Dark Web for Threat intelligence
The dark web can be a valuable source of threat intelligence, but useful data can be difficult to locate. The dark web’s focus on privacy and anonymity means that no directory of dark web sites exists, making it difficult to identify important sources of threat intelligence on the dark web.
A smart approach to dark web monitoring is to use a dark web monitoring service. These services have already performed the work of mapping out useful sections of the dark web and determining important sources of threat intelligence. With a dark web monitoring service, an organization can subscribe to a feed of threat intelligence regarding their company and industry without the need to employ in-house analysts to seek out, aggregate, and analyze it manually.
Who Is Active On The Dark Web And Why?
Dark web actors vary in sophistication from complete novices to nation-state-sponsored hackers. Some of the main categories of hackers on the dark web include:
- Script Kiddies: Script kiddies have little or no hacking knowledge and experience. They commonly use the dark web to find hacking tools and information on how to perform different types of attacks.
- Proficient Hackers: Proficient hackers work solo or in small groups and have at least some level of hacking knowledge. In addition to seeking out tools and information on the dark web, they may also buy or sell information about compromised organizations or user accounts for use in attacks.
- Crime Syndicates: Organized crime is increasingly moving into the cybercrime space due to its profitability and the difficulty of attributing cyberattacks. They are often more sophisticated and operate at a larger scale than other hacking groups.
- APTs: Advanced Persistent Threats (APTs) are the most sophisticated type of hacker present on the dark web. They are also often the most subtle, making their presence difficult or impossible to detect.
The various levels of hackers also seek out different types of malware on the dark web. For example, script kiddies are more likely to have or be looking for a password cracker, while APTs are generally the only ones with access to many zero-day exploits. In most cases, high-reward malware, such as ransomware, is in the hands of organized crime or APTs.
Types Of Threats On The Dark Web
Dark web threats come in a variety of forms. When searching for threat intelligence on the dark web, it’s important to look for the various types of data and services that cybercriminals offer for sale.
Vulnerability Information
Software vulnerabilities are common and could allow an attacker to access corporate systems or vulnerable devices. If a vulnerability is ethically reported by the discoverer, a complete report of how the vulnerability works is usually not released until a patch is released. However, there is often a gap between the initial discovery of the patch and its widespread implementation.
The dark web provides a forum for cybercriminals to discuss vulnerabilities that are not ethically reported or patches are not widely available or used. Discussions may include information about how a vulnerability works, potential exploits, and its use in various cyberattack campaigns.
Cybercriminals may be discussing vulnerabilities on the dark web before information about them is made public. Monitoring these channels enables an organization to protect vulnerable software until a patch is found and applied, and can reveal previously unknown vulnerabilities in a company's products.
Insider Threats
Insider threats pose a significant risk to an organization's IT assets, intellectual property and other sensitive data. Insider threats can be current or former employees, partners, vendors, resellers, and other parties with access to sensitive information. Additionally, insider threats can intentionally or through negligence put the organization at risk.
Information about insider threats can be found on the Dark Web. Insiders may offer sensitive data or sell it on Dark Web marketplaces. Additionally, users can upload software or other data collected from an organization to some platforms. By monitoring these locations, an organization can identify potential insider risks and compromised sensitive data.
Open Credentials
Credentials exposed as part of data breaches, credential stuffing attacks, and similar cyberattacks are commonly for sale on dark web marketplaces. Exposed credentials may be used to gain access to the named account or as part of a spear-phishing campaign where the attacker claims that the credentials were collected by malware that they installed on the target’s computer. Alternatively, exposed credentials can be used for credential stuffing attacks, where cybercriminals test to see if breached credentials are reused across multiple accounts.
Information on compromised credentials can be invaluable for corporate cybersecurity. Data on breached passwords can help to improve password policies, and, if the credentials of an organization’s employee(s) are breached, this is a red flag to change the account password and investigate for potential use of the compromised credentials.
Targeted Attacks
Cybercriminals are increasingly moving toward a service-based economy where specialists offer their services for sale. In many cases, these services are sold on dark web marketplaces.
For example, a botnet operator may be selling distributed denial of service (DDoS) attacks where the buyer can select the timing, duration, and intensity of the attack against a target of their choice for varying prices. Alternatively, a buyer on a dark web marketplace may be able to purchase a very tailored attack, such as hacking a social media account of their significant other.
Information about targeted attacks for sale can help an organization to identify unknown and upcoming threats to its security. If an attacker is offering access to an organization’s software or online accounts or a buyer is seeking a DDoS attack against corporate assets, this requires further investigation and response.
Hacked Accounts
Hacked accounts are commonly for sale on dark web marketplaces. Hacked personal accounts include access to financial accounts, email, social media, e-commerce sites, and other online accounts. Additionally, cybercriminals may offer access to corporate accounts for sale, allowing other attackers to purchase a foothold within an organization’s environment.
Monitoring dark web marketplaces for sales of hacked accounts is essential to protecting an organization’s data and network security. Sales of access to corporate networks or data indicate a current threat to the enterprise. Additionally, hacked email and other personal accounts may impact the company if password reset emails are sent to those accounts or the attacker expands their access from personal emails to corporate resources.
Botnets for Sale
Botnets are a collection of compromised machines that a cybercriminal controls and uses in automated attacks. For example, an attacker could exploit a vulnerability in an IoT device to take control of a number of vulnerable devices. These IoT devices can then be used for distributed denial of service (DDoS), credential stuffing, and other automated attacks.
Botnet operators can have thousands of bots under their control and the ability to break their botnets up into smaller groups. On dark web marketplaces, these operators may sell control over bots or sets of bots to other cybercriminals looking to use them in their attacks.Botnet operators can have thousands of bots under their control and divide their botnets into smaller groups. In Dark Web marketplaces, these operators can sell controls over bots or bot kits to other cybercriminals who want to use them in their attacks.
Bots are useful for cybercriminals because they make it difficult to trace cyber attacks back to the person behind them. When investigating a security incident, it can be helpful to monitor botnet sales to help correlate the attack.
These services must be performed by professionals. The cyber intelligence service received by people who are not experts in their field can lead your institution to the abyss.
Source
- https://www.bankinfosecurity.com/blogs/cyber-intelligence-what-exactly-it-p-1061
- https://www.recordedfuture.com/threat-intelligence/
- https://www.misp-project.org
- https://cuckoosandbox.org
- https://yeti-platform.github.io/yeti-ecosystem
- https://csirtgadgets.com/collective-intelligence-framework
- https://github-wiki-see.page/m/csirtgadgets/massive-octo-spice/wiki/What-is-the-Collective-Intelligence-Framework%3F
- https://www.ericooi.com/threat-intelligence-cif/
- https://www.logsign.com/blog/cyber-threat-intelligence-framework/
- https://tricksonflicks.blogspot.com/2017/11/collective-intelligence-framework-v3_7.html
- https://www.abuseinformationexchange.nl
- https://www.britannica.com/story/whats-the-difference-between-the-deep-web-and-the-dark-web
- https://flare.systems/resource-center/blog/dark-web-threat-intelligence/
- https://www.cybersixgill.com/dark-web/
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.