Nowadays, we use the internet for many things. This ranges from entertainment to work, shopping and everything in between. All of our modern household goods can communicate with each other over the web, thanks to IoT technology. However, this also comes with certain risks.
IoT is a communication network that enables physical objects to communicate and be connected with each other or with larger systems.
IoT APPLICATION AREAS
• Smart home appliances (cleaner, refrigerator, oven, air conditioner, etc.),
• Smart city applications (traffic systems, parking applications, etc.),
• Sensor Technologies,
• Data analysis applications etc.
WHY IS IOT SECURITY IMPORTANT?
Since IoT technologies, which have started to surround all parts of our lives, communicate with devices over networks, protection of our personal data, etc. It is clear that the situation will become more difficult. We think we don't need to be a prophet to guess. Therefore, the need for people working in the field of 'Cyber Security' will increase even more. As a matter of fact, we can say that our thinking is in the same situation for IoT technologies as we were at the beginning of technology in the early 90s. If you ask why; Considering today's technology, IoT technologies can be said to be cumbersome. That doesn't mean it will stay that way. In fact, we think that it will integrate with today's technology level much faster. On another issue, for those who work in the field of 'Cyber Security'; We see IoT technologies as a VERTICAL field.
Come on now, to the architecture of IoT technology, how security vulnerabilities that may arise and how we can take precautions.
IOT COMMUNICATION ARCHITECTURE
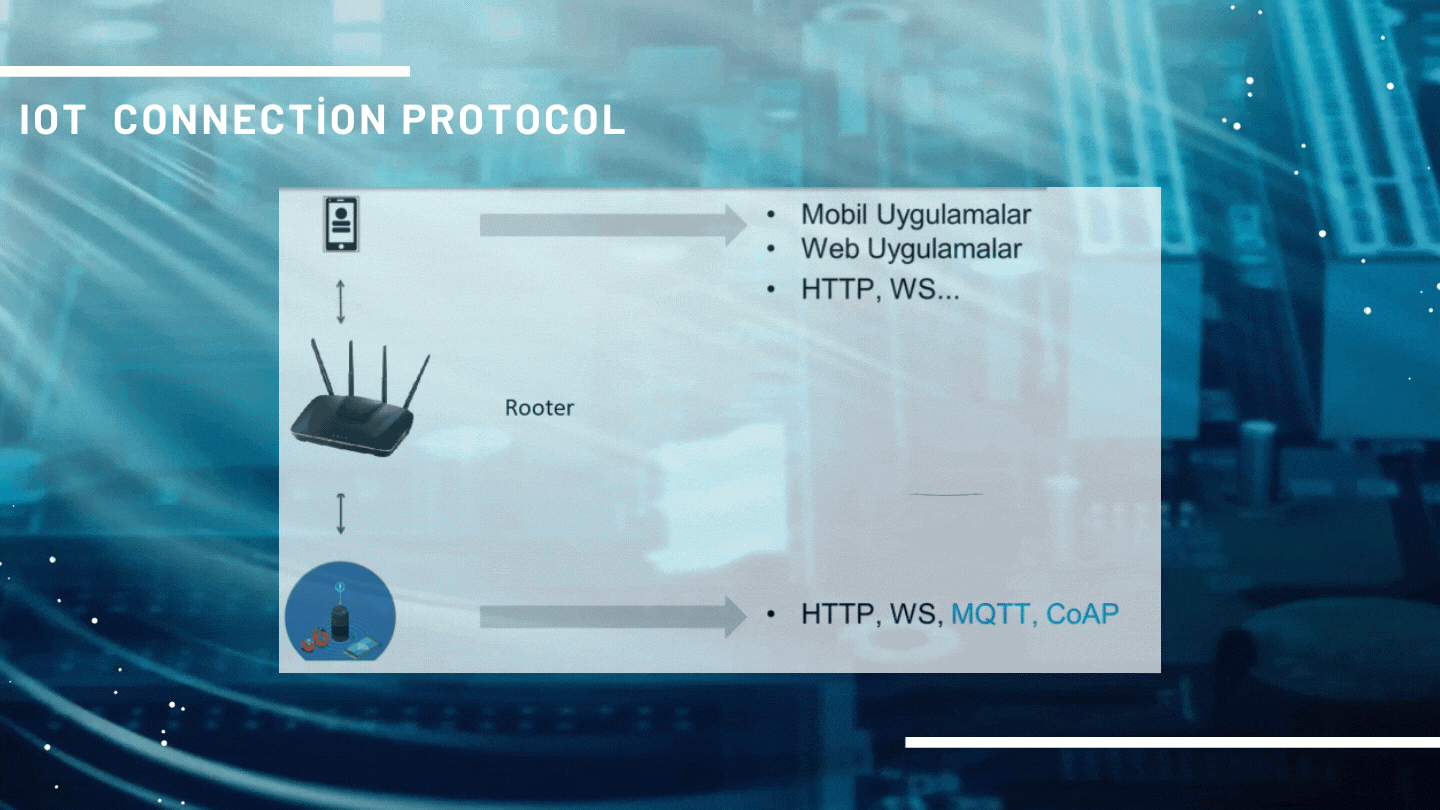
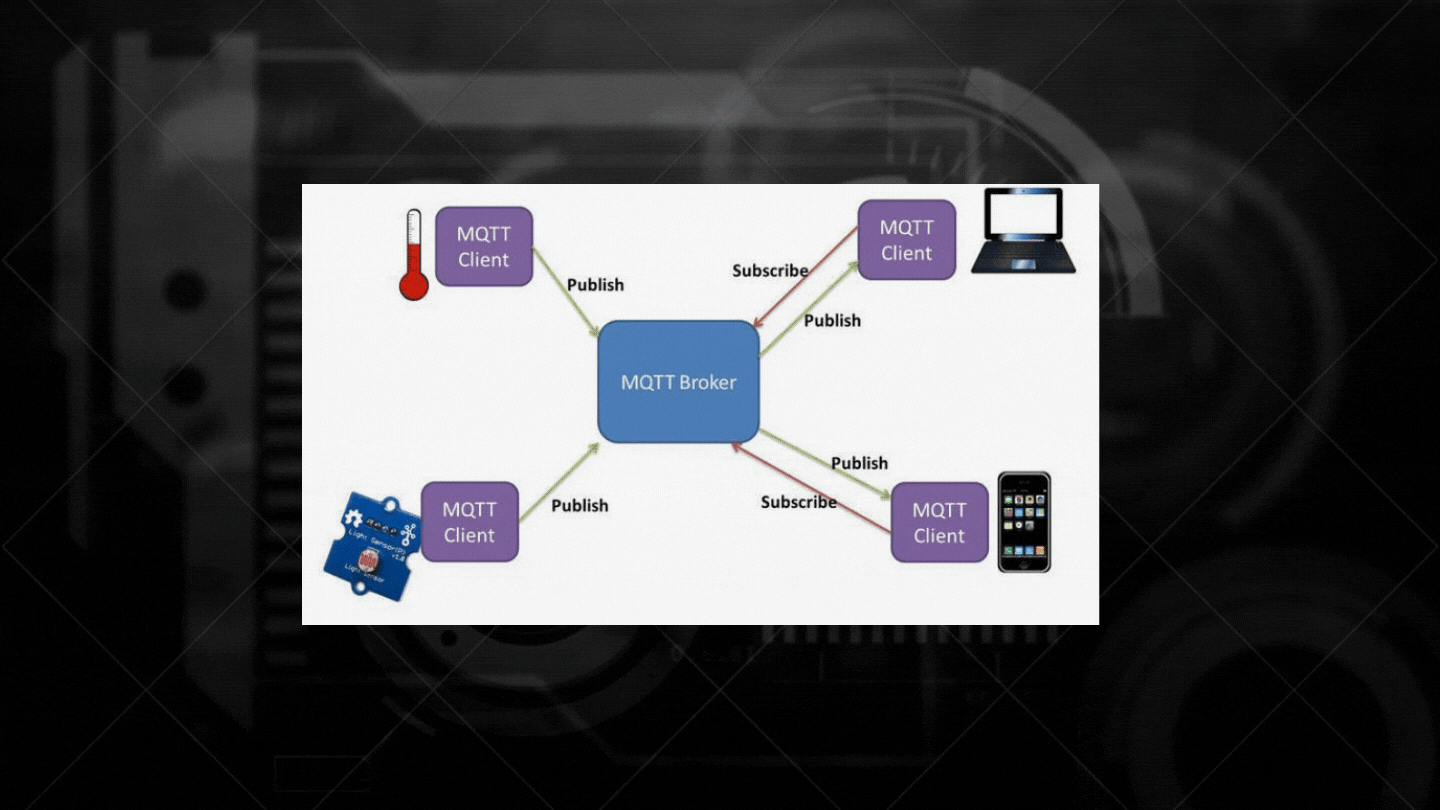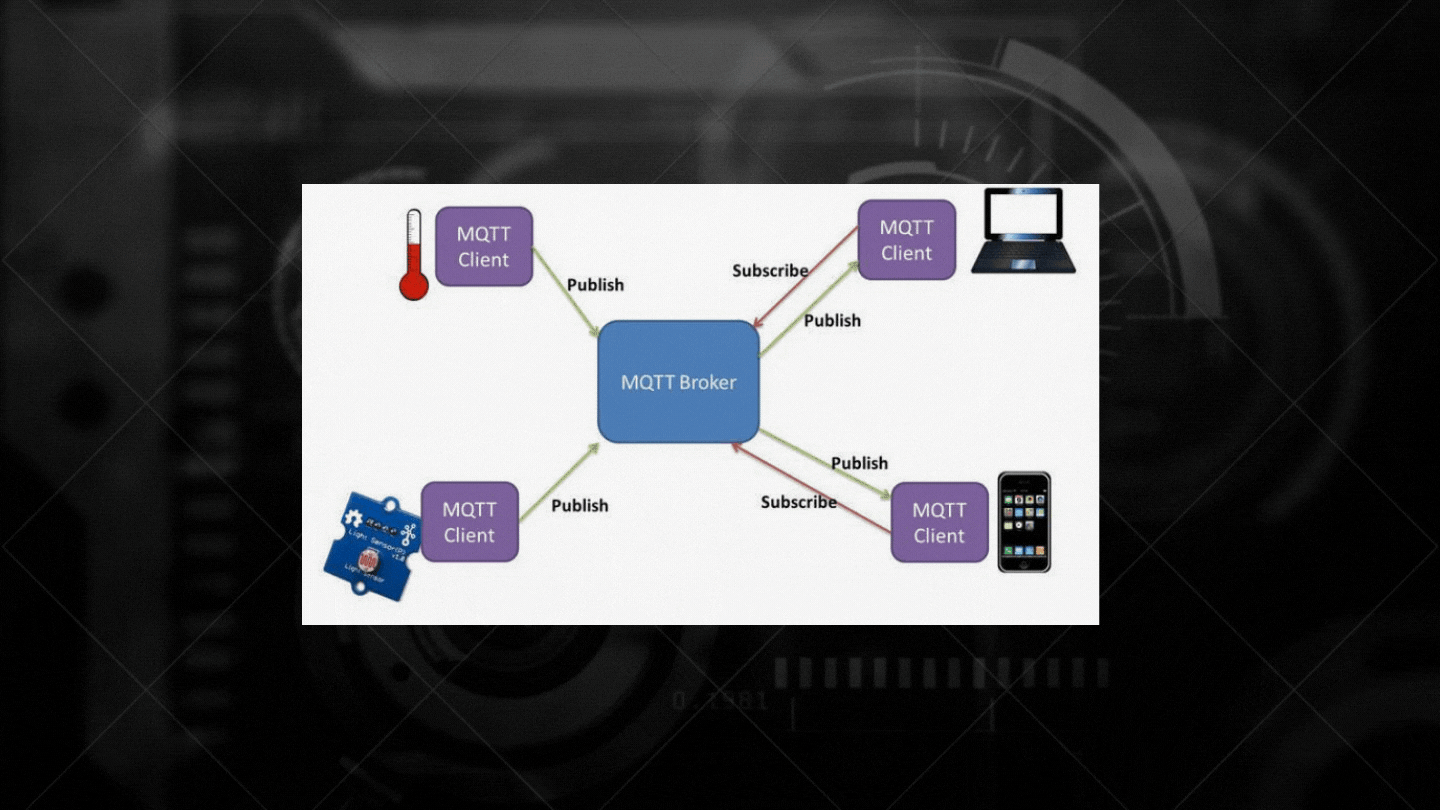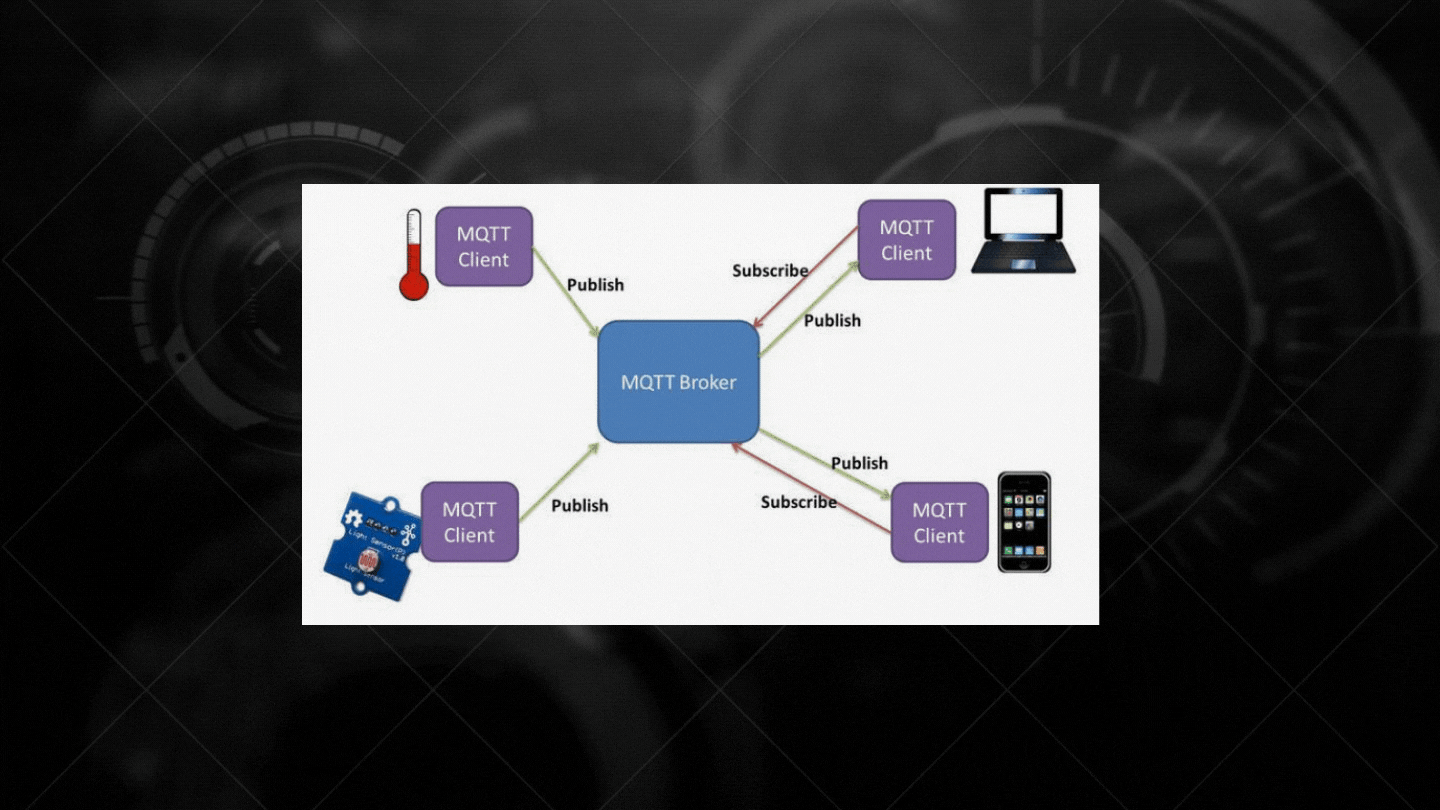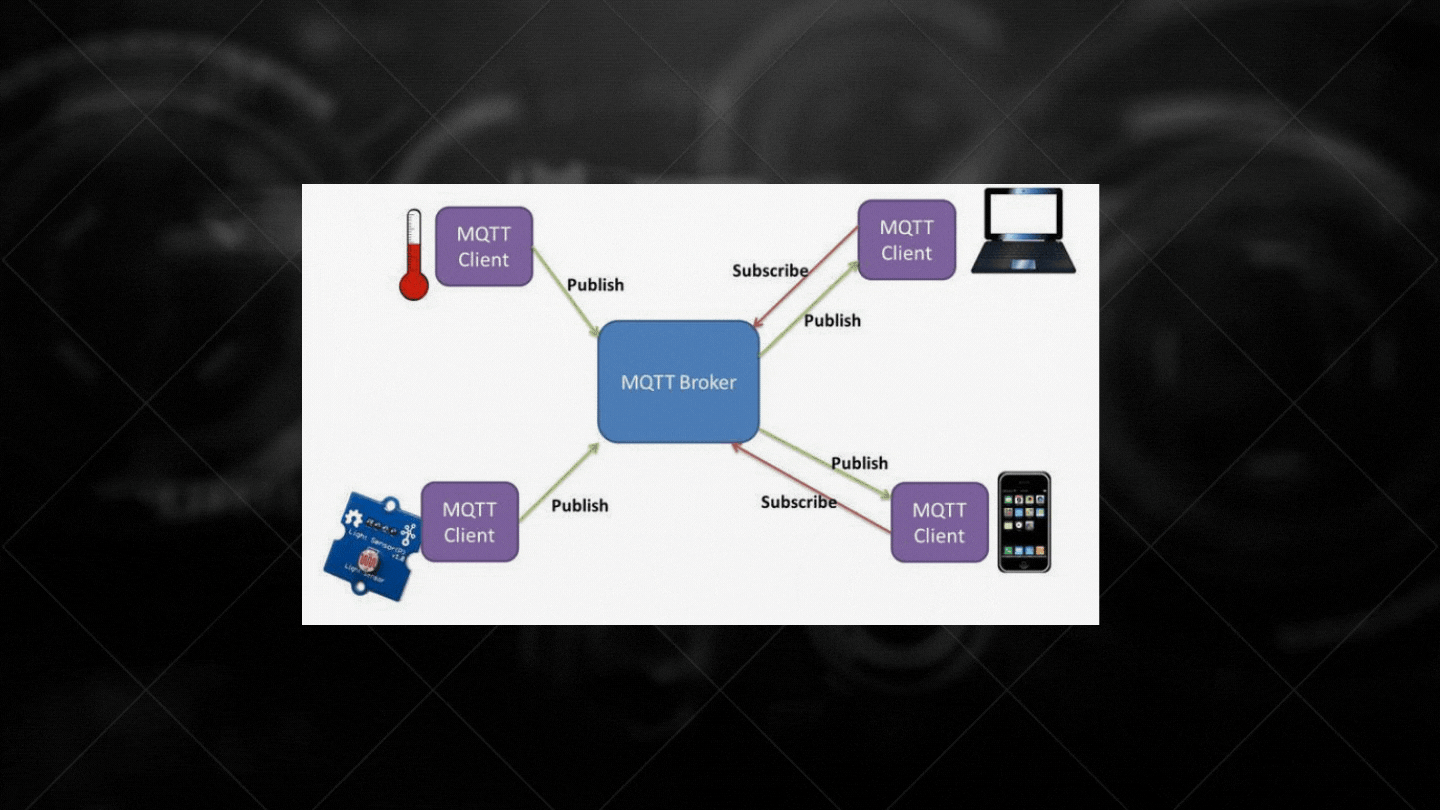
IoT devices do not generally need Cloud systems when communicating with the network, but it does not mean that there will be no need for developments. The technology most commonly used in interior architectures is MQTT and Coap technologies. There is also a 'web socket' system under MQTT. The only reason why this communication system is widely preferred is as follows; When you try to send a request over http, the system will try to detect it, start broadcasting to see if it has come to me, and try to match, although there may be a delay of seconds, the transaction will take place. However, there will be no such delay as MQTT is constantly dependent on the application.
As follows; The way IoT technologies are connected with 'MQTT Broker (can be rooter)' is reflected.
IOT SECURITY VULNERABILITY EXAMPLES
1. Man In The Middle (MITM) man-in-the-middle attack may be a cliché of cybersecurity. But unfortunately, it is one of the main problems that can be encountered everywhere. Therefore, incoming requests and responses can be manipulated with the man-in-the-middle attack method in IoT devices.
HOW DOES IT WORK ON ATAK IoT DEVICES?

To put it in its simplest form;
As seen in the figure above, 'Attacker' says to 'Client A' machine: 'I am IoT rooter, send me your message.' Then it says to 'IoT rooter' machine: 'This is my message to Client A, waiting for your return. . And thus, 'Attacker' has captured incoming and outgoing messages.
MITM attacks can be prevented or detected in two ways: authentication and tamper detection. The summary of the work is due to incorrect or incomplete configuration errors. Authentication etc. If the methods are not done, another user's cookie, session id, token value, etc. With the captured information, access to IoT devices can be obtained.
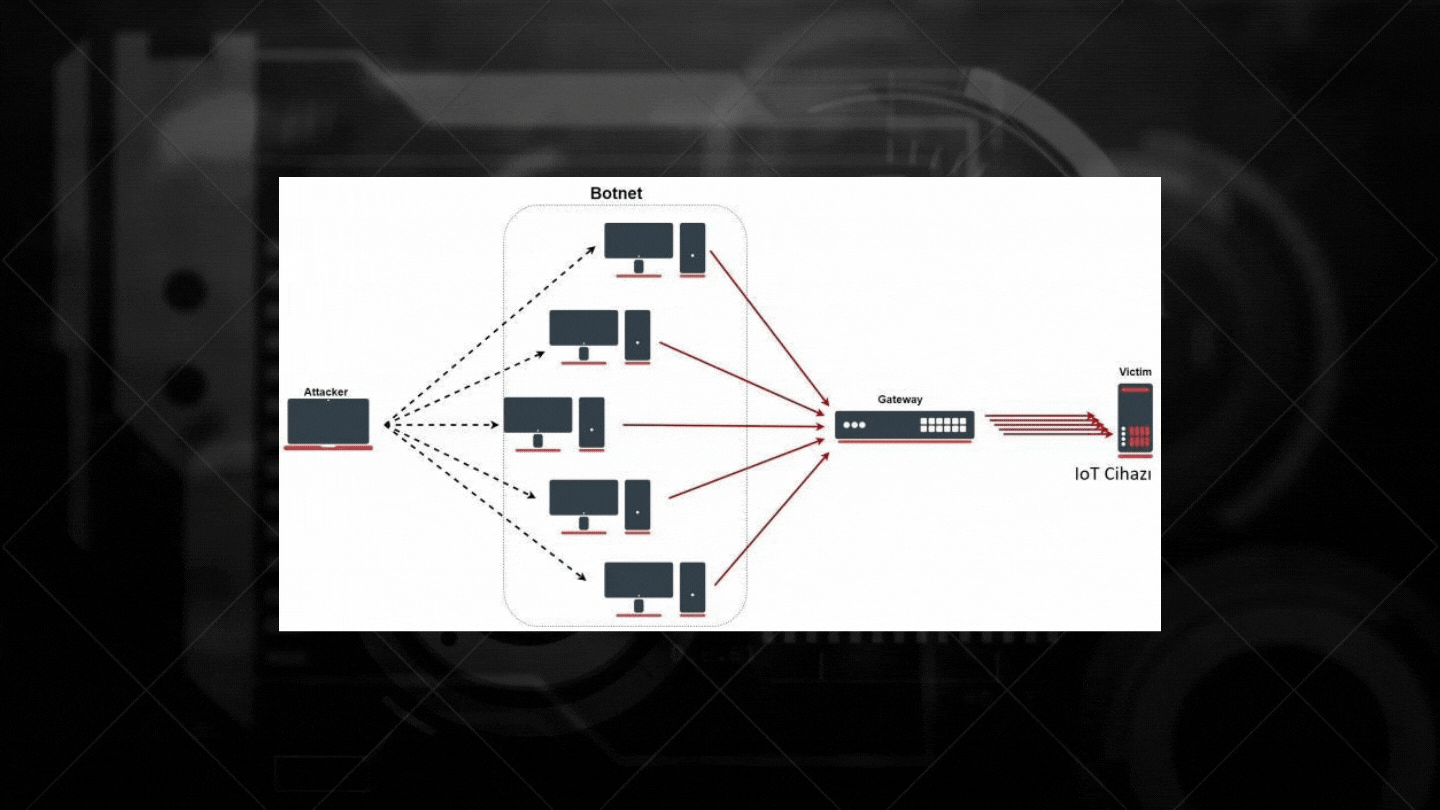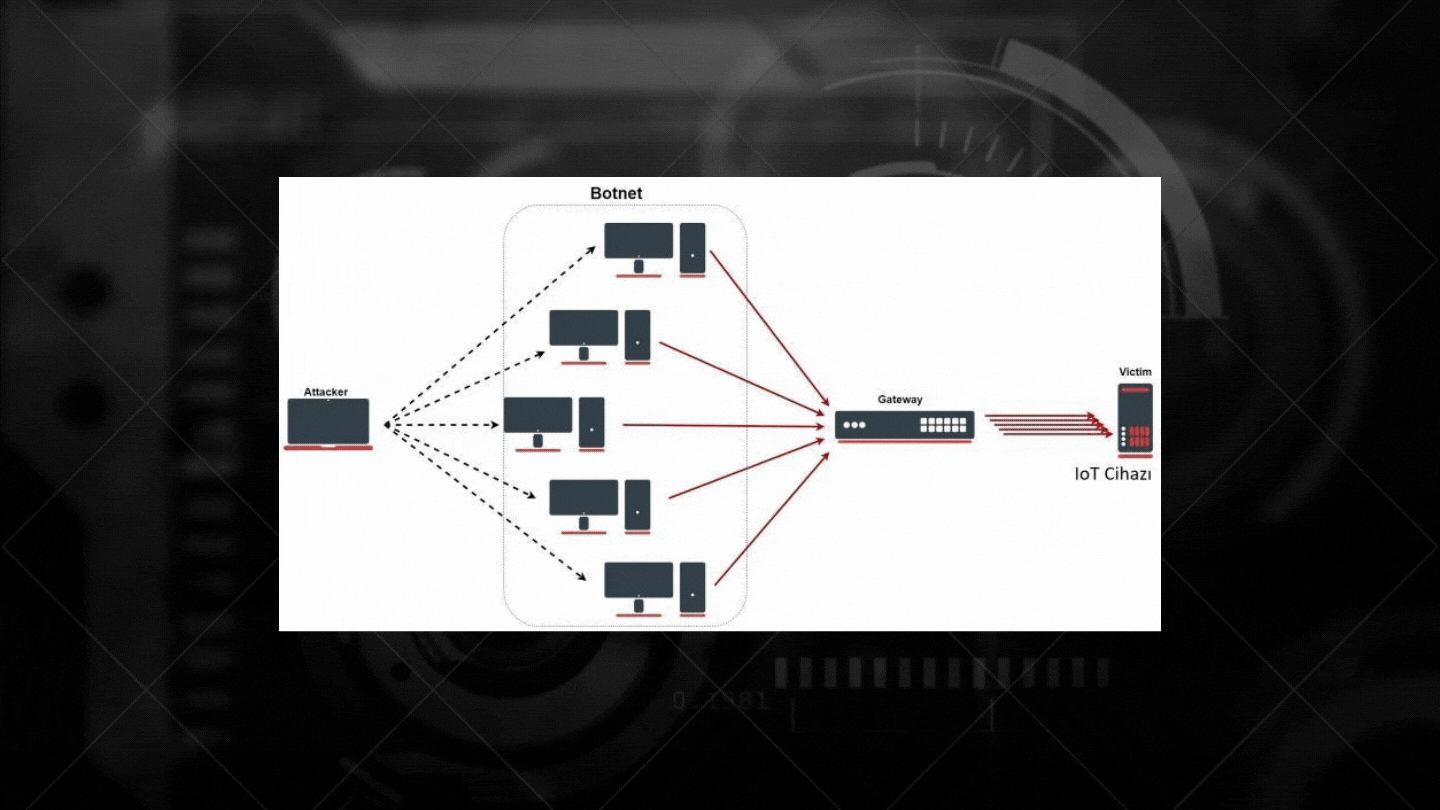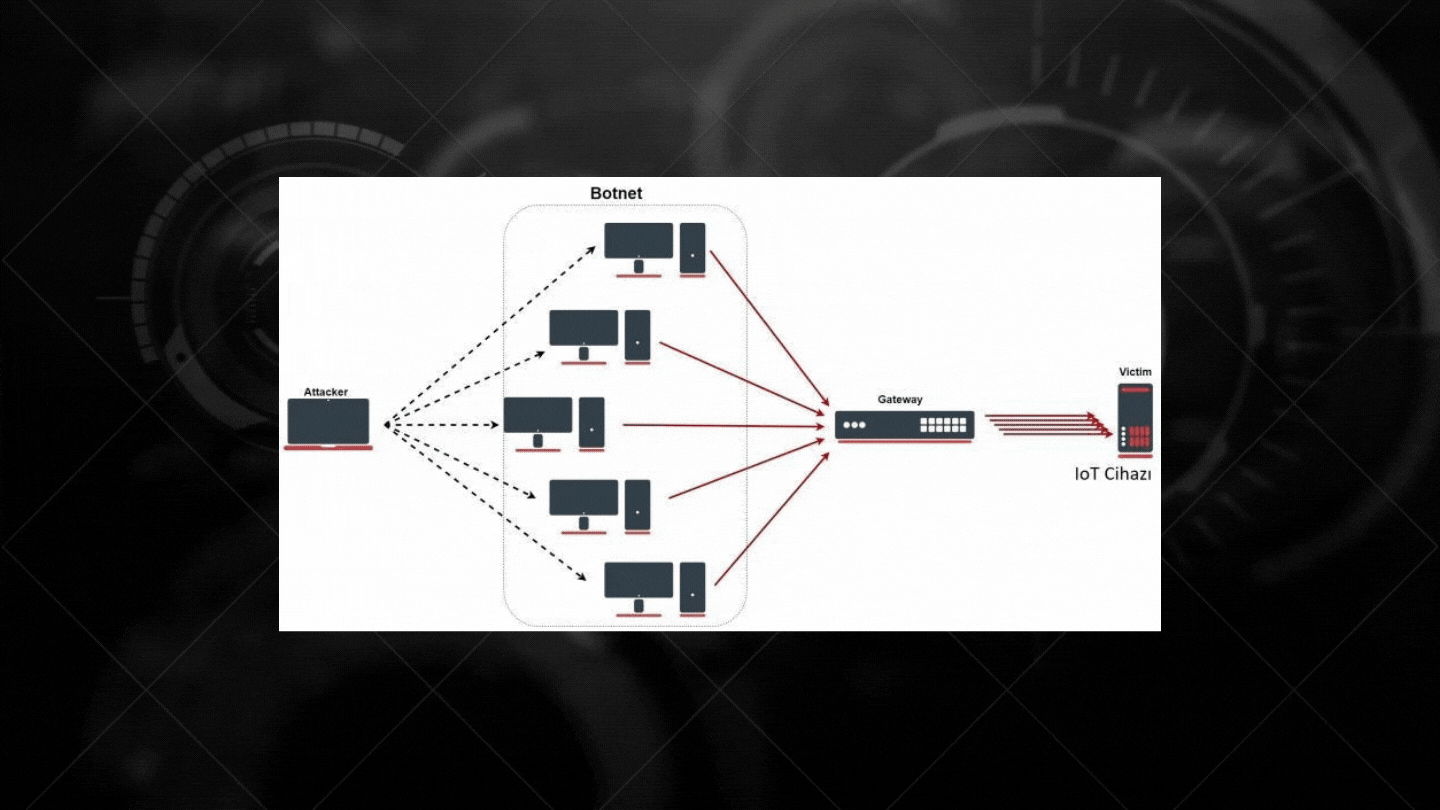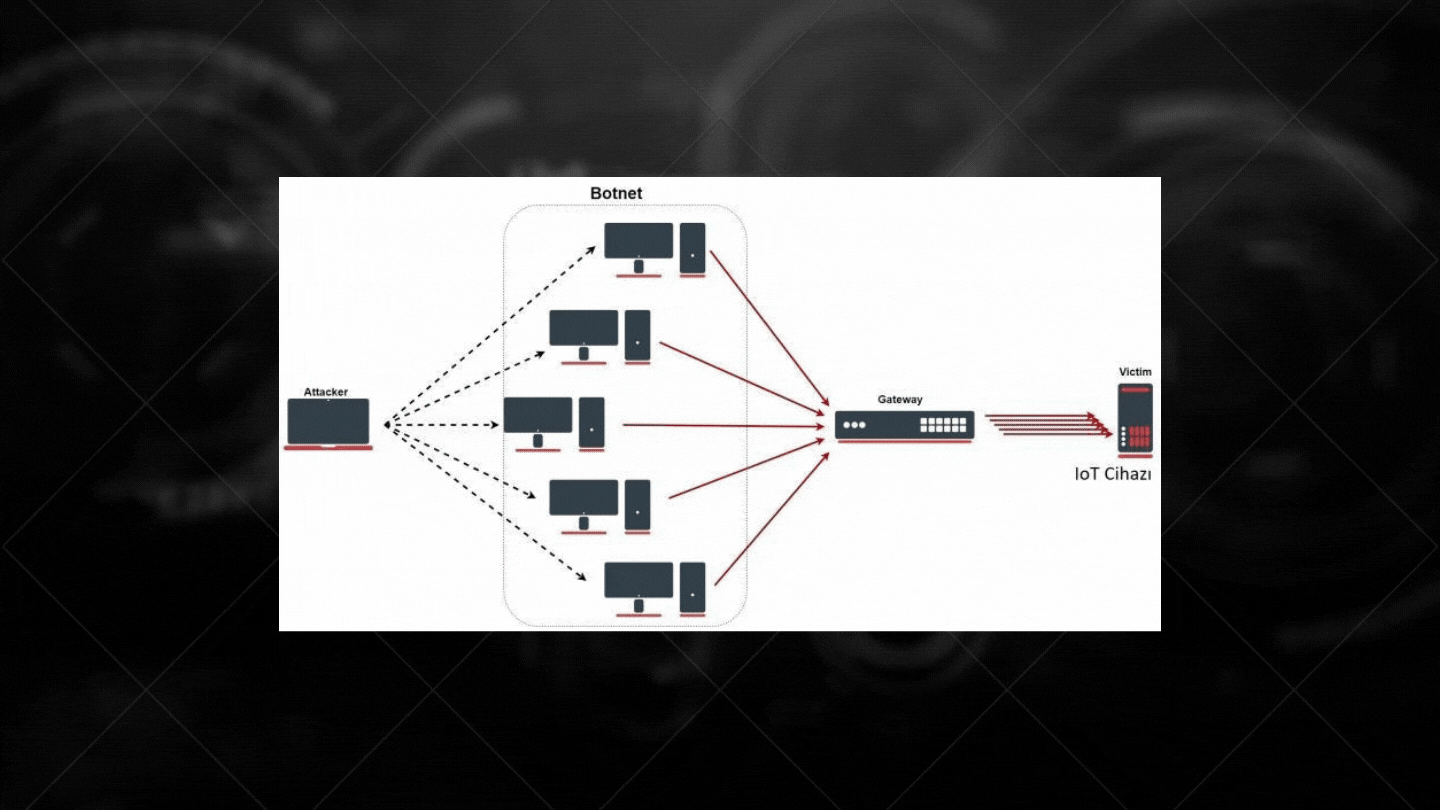
2. DDoS Attacks are a type of attack that aims to temporarily or indefinitely disrupt the services of an internet-connected host, so that a machine or network resources cannot be reached by the actual users.
HOW IS DDOS ON IOT DEVICES?
As you can see in the figure below, service interruptions may occur on IoT devices without DDos protection using botnet networks.
These examples do not end as you write. Therefore, we share with you the top ten (10) lists of Owasp's IoT vulnerabilities.
OWASP IOT – TOP 10 LIST OF IOT Vulnerabilities
- Weak, Predictable, or Hard-coded Passwords
- Unsecured Network Services
- Insecure Ecosystem Interfaces
- Lack of Secure Update Mechanisms
-
Use of Unsafe or Outdated Components
- Insufficient Privacy Protection
- Insecure Data Transfer and Storage
- Lack of Device Management
-
Unsafe Default Settings
- Lack of Device Physical Security
Conclusion:
We foresee that IoT technologies will increase day by day and reach institutions and people from all walks of life. With the development of IoT technologies, we think that it is necessary to further develop and attach importance to the security corridors of IoT technologies for the security and protection of personal data.[:]
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












