What are LNK Files?
LNK files (Windows shortcut files) are files that are automatically created by the Windows operating system, usually each time a user opens their file. These files are used by the operating system to provide quick access to a particular file. It can also be created by users themselves to facilitate their activities.
Location of LNK files
- for Windows 7 – 10: C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Recent
- for Windows XP: C:\Documents and Settings\%USERNAME%\Recent
- On the desktop (such files are usually created by users for quick access to documents and applications)
- C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Office\Recent\ (For Microsoft Office documents from Windows 7 to 10)
- Startup folder
Why are LNK Files Important for Forensics?
LNK files can offer forensic researchers an excellent solution for finding files that no longer exist in the system.
Files may be securely wiped (Wiped), stored on a USB or network share, so even though the file is no longer on the system, the LNK files associated with the original file still exist in the system, revealing valuable information about what was playing on the system.
LNK files contain the following evidence-value items:
- The original path of the file.
- MAC times of the original file (metadata that records when files were created, modified, and accessed).
- The volume name, serial number, NetBIOS name, and MAC address of the host where the LNK file is stored.
- Network share details if the file is shared on the network or stored on a remote computer.
- The file size of the LNK file.
LNK file recovery
If the LNK file we need has been deleted, it must be recovered via any "Carving" tool. LNK files can be found with the file header signature, hex: 4C 00 00 00.
Collecting LNK files with Binalyze Air
Binalyze Air provides the opportunity to respond to cyber incidents in real time without wasting time, and automatically collects more than 120 digital forensic evidence within 10 minutes, integrated with existing SIEM/SOAR products.
With this tool, you can collect all the LNK files available on a system.
1- We will create a new profile in the Acquisition section, we only want LNK files to be brought.
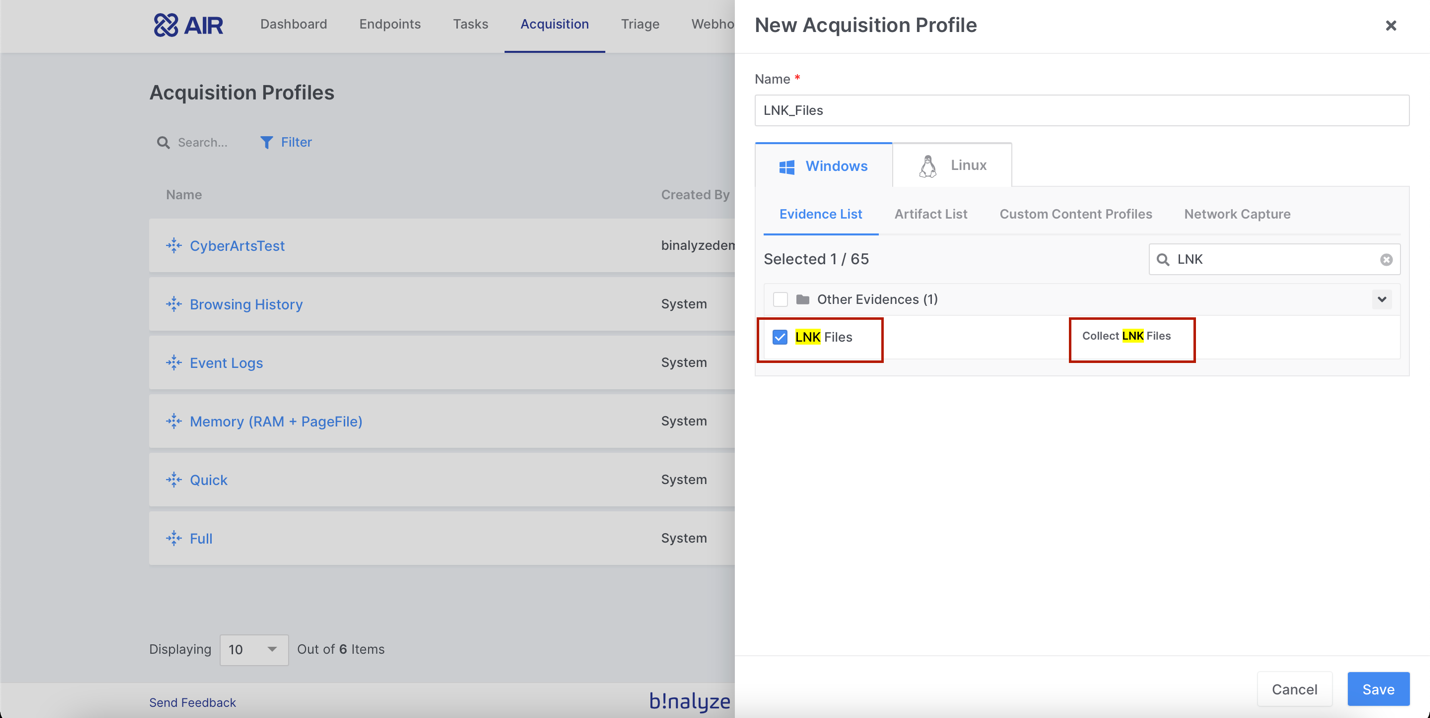
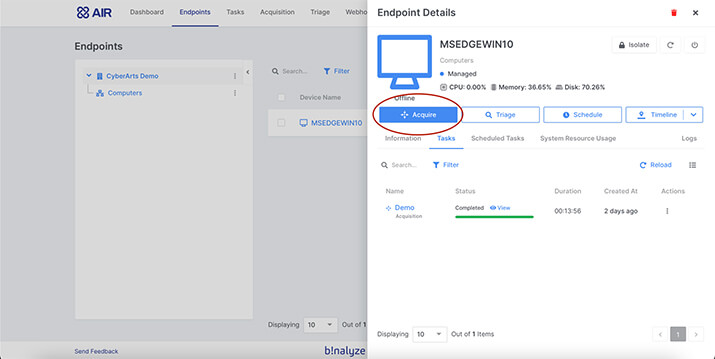
2- In the next step, we can start the collection of LNK files on the system we want in the Endpoints section.
3- We specify the path where LNK files will be saved (local or network storage) and we can also encrypt or compress the data we collect.
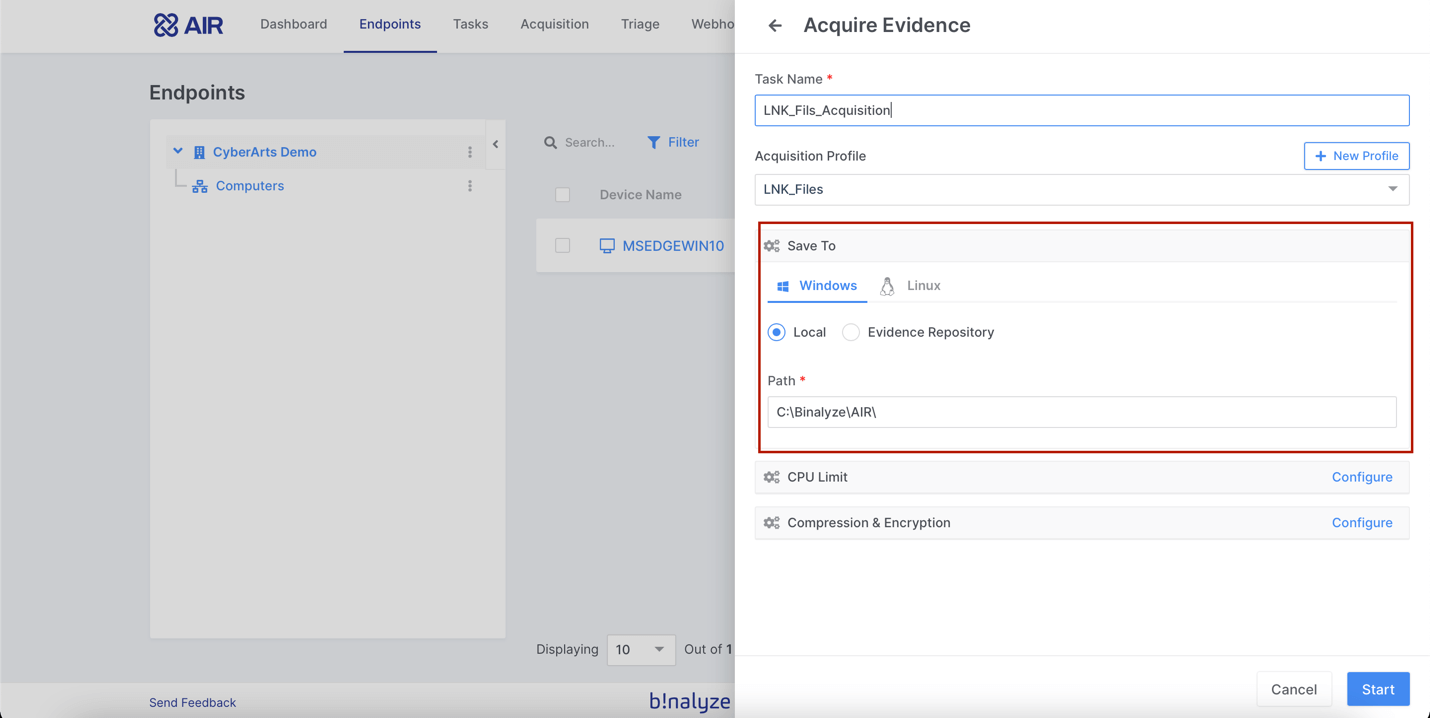
4- Binalyze Air collected all LNK files above the endpoint in 14 seconds.
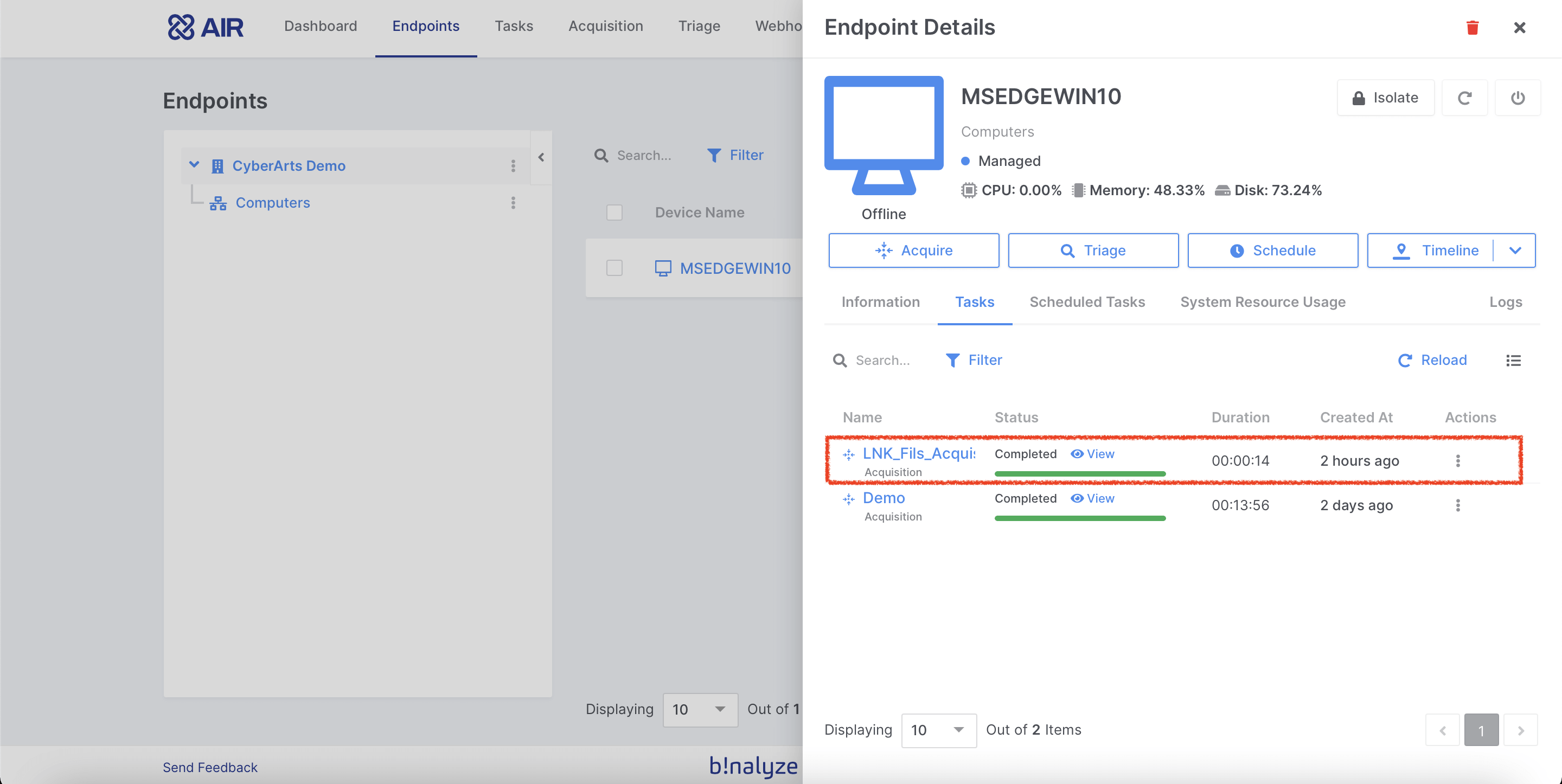
5- After collecting LNK files, we can perform offline analysis with the “LECmd” (LNK explorer) tool and run the following command to get csv output.
LECmd.exe -d [path to LNK files we collected] -q --csv
Source
magnetforensics.com
forensicswiki.xyz
belkasoft.com
binalyze.com/air
ericzimmerman.github.io
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












