What is XXE (XML External Entity) injection?
XXE is a web vulnerability that allows an attacker to manipulate and intercept the web application’s XML data. By exploiting the XXE vulnerability, an attacker can perform server-side request forgery (SSRF) attacks to retrieve sensitive data, Remote Code Execution, system scanning, DOS denial of service attack, and in some cases.
How are XXE vulnerabilities exposed?
Some web applications use XML markup language to standardize communication between platforms that enable internet-based data exchange between browser and server.
XXE vulnerabilities occur because XML specifications contain various potentially dangerous features and are supported by standard parsers.
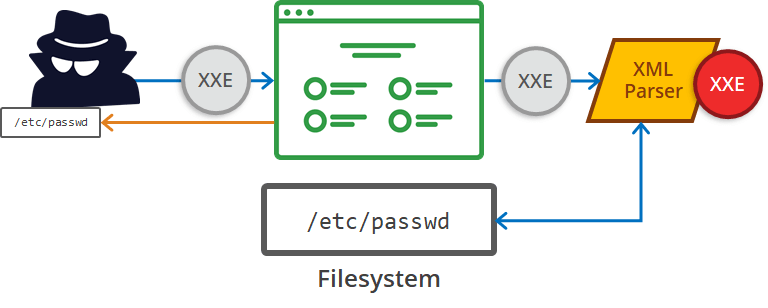
XXE Attack Types
- Exploiting XXE to retrieve files sensitive data can be retrieved when the contents of a file are returned in the HTTP response on the web server.
- Leveraging XXE to perform SSRF attacks Besides retrieving sensitive data, the other main effect of XXE attacks is that they can be used to perform server-side request forgery (SSRF). This vulnerability is very dangerous because the server would be able to make HTTP requests to any URL it can access.
- Blind XXE out-of-band data spoofing is an attack that allows sensitive data to be transmitted from the application server to an attacker-controlled system.
- Leveraging blind XXE to retrieve data via error messages, where an attacker could exploit a parse error message containing sensitive data. This vulnerability will take effect if the web application returns the error message that occurs in the HTTP response, and it can capture important data such as the /etc/passwd file. faydalanabilir. Bu açıklık, web uygulama HTTP yanıtında ortaya çıkan hata mesajını döndürürse etkili olacaktır ve önemli veriler /etc/passwd dosyası gibi ele geçirebilir.
- XXE attack via file upload, some of the web applications allow users to upload files that are more processed on the server side. The file extension uses XML, or another file with XML subcomponents is used, such as DOCX and SVG files. The uploaded file may contain malicious XML code and sensitive data may be stolen.
How to Avoid XXE Vulnerabilities?
For the prevention of XXE:
- Whenever possible, use less complex data formats such as JSON and avoid serialization of sensitive data.
- Patch all XML processors and libraries and keep the version up to date.
- Disable non-XML entity and DTD processing in all XML parsers in the web application.
- Implement positive (“whitelisting”) server-side input validation, filtering, or sanitization.
- Verify incoming XML integrity using XML or XSL file upload functionality, XSD (they are “XML Schemas” that define the structure of an XML document.) validation or similar.
- Using SAST (Source Code Analysis Tools) tools can help detect XXE vulnerability in source code.
Source:
owasp.org
portswigger.net
portswigger.net
portswigger.net
portswigger.net
hdivsecurity.com
en.wikipedia.org
KVKK, ISO 27001, Bilgi ve İletişim Güvenliği Rehberi, ISO 27701, Bilgi Güvenliği, Siber Güvenlik ve Bilgi Teknolojileri konularında destek ve teklif almak için lütfen












