Introduction
As firewall technologies have evolved, so have hackers. There is no problem in the IP and Transport layers in the OSI model, but what should we do if the real threat is in the data part of the package?
At this point, Deep Packet Inspection / In-depth Packet Inspection (DPI) method comes in.
For example, many applications (e.g. Skype, P2P torrent apps) run on standard HTTP and HTTPS ports. A firewall using static and/or stateful filtering will allow traffic from applications that think it's normal web traffic.
DPI, on the other hand, can basically examine not only the general information carried by a packet, but also the contents of the packet. In other words, DPI can say "While the port used is HTTP, the ported application is actually Skype".
What is Deep Packet Inspection?
A packet or data being sent over TCP/IP passes directly through the router, and this data being sent to the routers is delivered to the destination with the Destination Address transmitted to the router. Although the main purpose of routers is to transmit data as fast as possible, a router can do more than just transmit data when requested; because the data being sent passes through the router first when going out of the network and the router has the opportunity to view the content of this data.
In DPI, instead of making simple inspections on the package, in addition to other package inspection methods, it provides a more in-depth inspection by examining all layers in the OSI model, especially the Application Layer and the Data/Payload information in the package being sent.
How Does Deep Packet Inspection Work?
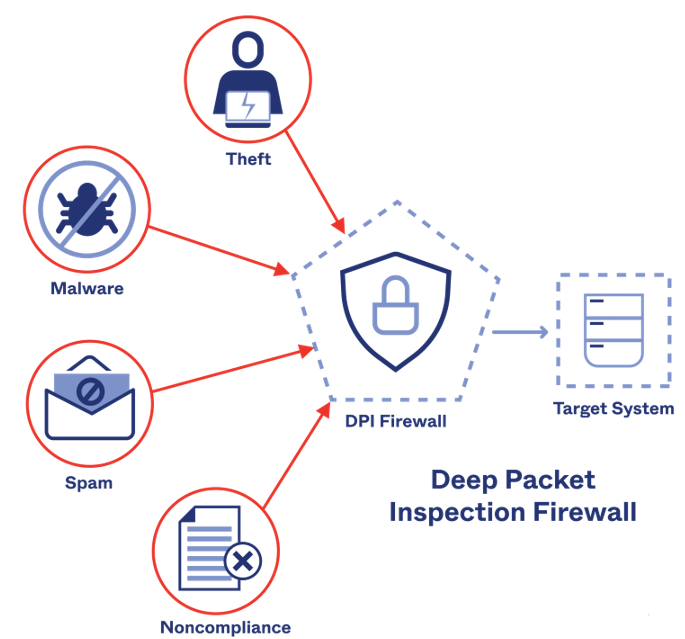
Deep packet inspection is packet filtering, often integrated into firewalls.
Deep packet inspection evaluates the contents of the packet passing through a checkpoint. Deep packet inspection can be performed using rules assigned by your internet service provider or network system administrator.
DPI can check the contents of the packets and then find out where the service that sent it came from. Also Twitter, Facebook etc. Various filters can be used to find and route network traffic from an online service or a specific IP address.
Deep Packet Inspection Techniques
Some techniques used in deep packet inspection are listed below:
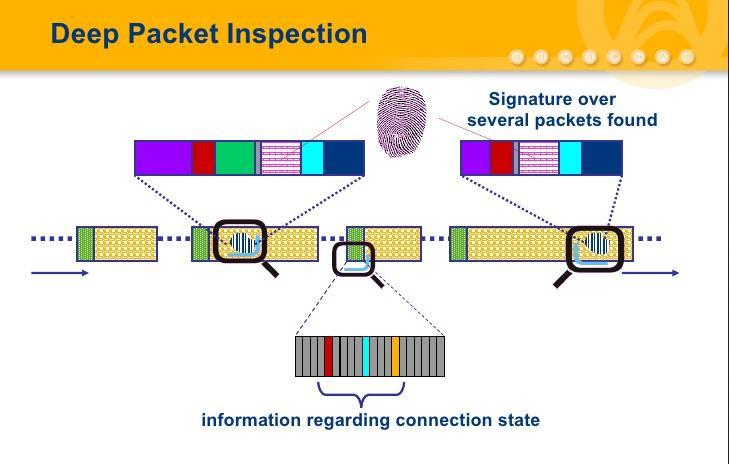
Pattern or signature matching
A firewall with Intrusion Detection System (IDS) analyzes each packet against a database of known network attacks. IDS looks for specific signatures that are known to be malicious, and if it finds such a signature, it blocks traffic. The disadvantage of the signature matching technique is that it is effective when signatures are updated regularly.
Also, this method only works against known threats or attacks. As new threats are discovered every day, ongoing signature updates are critical to ensure the firewall can detect threats and continue to keep the network safe and secure.
Heuristic and Behavioral Analysis
Understanding an application or protocol starts with examining its behavior. like measuring. Even if the protocol or application changes its signature, the behavior is likely to remain the same. For example, Voice over IP (VoIP) traffic usually starts with session initiation, and many UDP packets are used to deliver call traffic.
Protocol anomaly
The protocol anomaly technique is also used by firewalls with IDS, but here it follows a default deny approach where the firewall determines what content/traffic should be allowed based on the protocol definitions. So the difference is that unlike signature matching, this method also protects the network from unknown attacks.
Intrusion prevention system (IPS)
IPS solutions can block detected attacks in real time by blocking the delivery of malicious packets based on their content. Therefore, if a particular packet represents a known security threat, IPS proactively blocks network traffic based on a defined rule set. However, the database needs to be regularly updated with information about new threats.
The downside of IPS is that FP situations may arise, but these can be mitigated by regularly reviewing logged events to improve network monitoring and alerts by establishing appropriate basic behaviors, policies for protection, and custom thresholds for network components.
Deep Packet Inspection Advantages and Disadvantages
Advantages
- Allows to detect, identify, classify, redirect or block malicious codes that cannot be detected by normal packet filtering.
- Communications service providers can use DPI to facilitate traffic flow.
- Restricted data transfer can be provided to prevent network abuse, thus improving network performance for most users.
Disadvantages
- It can create new security vulnerabilities.
- It can be used to facilitate attacks in some categories.
- It adds additional security measures to existing firewalls and other security-related software, but makes it difficult to use.
- It may decrease the computer speed as it increases the processor load.
Usage Examples for Deep Packet Inspection
There are several uses for deep packet inspection. It can be used as both an intrusion detection system and a combination of intrusion prevention and intrusion detection. It can identify attacks that your firewall, intrusion prevention and intrusion detection systems cannot adequately detect.
If your organization has users who use their laptops for work, deep packet inspection is vital to prevent worms, spyware, and viruses from entering your corporate network. Also, using deep packet inspection relies on rules and policies defined by you. It allows your network to detect if there are prohibited uses of approved applications.
Deep packet inspection is also used by network administrators to help streamline the flow of network traffic. For example, if you have high-priority data, it can use deep packet inspection to ensure that high-priority data is transmitted first to other low-priority data. It can also prioritize mission-critical packets over ordinary scan packets.
Finally, deep packet inspection can help you avoid any information leaks, such as emailing a confidential file.
Why is Deep Packet Inspection Important?
Deep packet inspection provides advanced network management, user service and security functions as well as internet data mining, eavesdropping and internet censorship. DPI is used by telecommunications service providers and government in a wide variety of enterprise applications.
Against rapidly evolving threats and zero-day attacks, DPI is critical to providing an effective network security strategy.
Some Software Offering Deep Packet Inspection Solution
The DPI solution is usually a feature located within different products. Some technologies that provide this solution are listed below:
- Omnis CyberStream Network Security Sensor: NETSCOUT CyberStream network security sensors strategically deployed in any network environment (including public cloud), a rich layer 2-7 metadata raw packets provide cybersecurity teams with comprehensive network visibility and a rich data source for better It uses a proprietary, highly scalable, Deep Packet Inspection (DPI) technology to convert it into a data source.
- SolarWinds Network Performance Monitor: This network monitoring tool provides deep packet inspection to identify source and target applications, endpoints in network traffic. It is just one feature of this product that includes automatic detection and continuous device monitoring. It runs on Windows Server.
- Paessler Packet Sniffing with PRTG: It is an infrastructure monitoring tool and includes a packet sensor.
- OpManager: It is a network performance monitor that can capture packets for offline analysis. It works on Windows and Linux.
- nDPI: Inspects packets in the application layer.
- Netifyd: An implementation of nDPI that captures packets for review by other services.
- AppNeta: It is a Cloud-based network monitoring system with offline traffic analysis.
- NetFort LANGuardian: It is a network security analysis tool that uses DPI and runs on Linux.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












