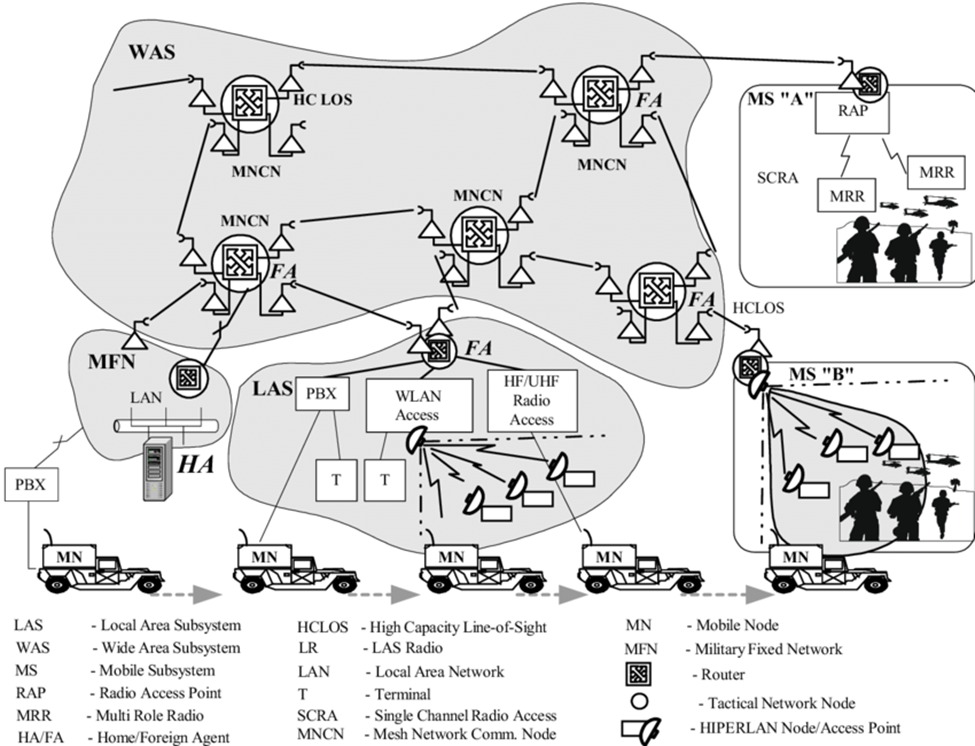
As with the simple illustration below, armies in many parts of the world prefer almost such methods of communicating. For communication, radyo frequencies, mobile nodes, satellite communication, local network, etc. are exemplary methods. It should be noted that during pentest, armies developed and established their own fiber network infrastructures. Therefore, public networks are not used.
From here we can create the two simplest black box scenarios.
- How can I disable satellite communication, radio frequency, etc. methods or listen to all communication?
- How do I get access to the army’s own local network? (Withmalware contagion, etc.)
The steps of the security tests for the ‘satellite communication’ method in the first scenario areas follows.
-
HARDWARE
To smell the satellite broadcast, you will need a Satellite dish with Low Noise Cancellation converter feature (LNB). The larger the dish, the better the signal range it can choose. A good satellite dish can cost between $50 and $300 and is easily available.
The size of the antenna depends on thesatellite you want to ff; If you only want to smell a specific satellite, a small 75 cm dish will suffice. you can easily find out by searching the internet or by visiting the satellite company’s website.
You can get detailed information about the satellite you want to block from theInternet. Thefollowing are details of some satellites in Latin America.
According to Mike Stevens, an expert at the International Institute for Cybersecurity, you can use the Internet tofind Polarization Setting (LNB Skew), Height, Azimuth for your dish placement based on your satellite and location.
-
INTERFACE
The next thing you need is a DVB Tuner card (DVB-S/S2 tuner card). The DVB tuner card is a type of card that allows satellite signals to be received by the computer. Most DVB tuners also function as video and multimedia content capture cards that allow them to record satellite content on a hard drive. Cards come in PCI Express (PCIe), PCMCIA, ExpressCard, or USB devices. The Tuner cardiseasily available onthe market and costs around 100 USD. The different card brands that work smoothly are DVBWorld, TBS/QBOX, Azureware, TechniSat, TechnoTrend, Genitech and TeVii. According to ethical hacking experts, the most widely used card is Technisat skystar 2. You can install these cards in the form of regular PCI cards or USB and they are very easy to install.
-
HUNTING
Now you will need a Feed browser software (Feed Hunt) to makeautomatic scanning and streamreader ‘.dll’. Temelde files with binary and ASCII streams “Protocol driver, iso files that convert videos, documents, pages, torrents into readable data such as”. There are many free software offered online. Some of the scanning software is CrazyScan and Easy Blind Scan. With this software, you can do Manual Scan and Auto Scan.
-
SATELLITE PHISHING
Depending on what your ultimate goal is, you will need sniff software. This software allows offline downloading of data, live radio and video streaming, satellite internet and signal capture. Some of this software includes:
a) SkyGrabber
SkyGrabber is software used to set up a satellite dish for the best retrieval of satellite internet service or television programs. The software has the browser mentioned in step 3 and offers the option to choose a satellite from the drop-down list. Almost all of the world’s regional satellite networks appear in this list, organized by longitude. If your satellite provider is not listed, you can manually add it from the New Provider dialog box. As soon as you select a satellite,it shows the various signal quality configurations that you can use to guide the satellite antenna and correct the direction as described in step 2. You can set file filters to download a specific data type.
You can even watch television shows on the card at the same time while using the software to download the content. The price of this software is around 40 USD euros and belongs to a Russian company. However, most people use a cracked version of this software that is easier to find.
b) SkyNet
This is software similar to Skygrabber, but in this we need to configure pid for certain transponderlar. This list is available on the Internet.
c) FishNet
This software is free but mostly used in the Middle East and is for DSL frequencies to download DSL-related data.
d) DVBDream Streaming software for Windows.
e) PROG DVB
Streaming software is also available for Android.
f) ALTDVB
Streaming software.
g) TSReader
TSReader is a transport flow analyzer, decoder, recorder and flow manipulator for MPEG-2 systems
h) DVBSNOOP
Dvbsnoop is a DVB/MPEG streaming analysis program that allows you to monitor streaming information (live) in a human-readable format. Its purpose is to debug, unload, or view digital streaming information (e.g. digital television broadcasts) sent by satellite, cable or land. You can use DVBSnoop type software for data analysis with wireshark.
i) Assume that all inbound and outbound traffic is encrpyt. The method of encrypting should be determined and decrypt operations should be performed in a form suitable for it.
Conclusion:
%100 güvenli sistem yoktur. CyberArts siber güvenlik firması olarak düşüncemiz kamu kurumlarının sızma testlerinin sürekli tek bir firma yapmasının yanında, siber güvenlik mimarilerinin ve siber güvenlik katmanlarının da birden fazla pentester ile farklı bakış açısı getirilebilecek siber güvenlik firmaları tarafından testlerinin yapılması gerektiğini düşünmekteyiz.
Because what did they say? “What’s wrong with a hand? There’s a voice in two hands.”
Disclaimer
Dear visitor,
This blog post is for information purposes and has been prepared with the aim of raising awareness against attacks and taking measures in this direction. We remind you that it is not legal to use the information in this article for any other purpose. We declare that CyberArts company cannot be held responsible for direct or indirect damages and losses that may arise from what is explained.
To request a quotation for the following: Cyber Security, Digital Transformation, MSSP, Penetration Testing, KVKK, GDPR, ISO 27001 and ISO 27701, please click here.












